Bugs in billions of WiFi, Bluetooth chips allow password, data theft
- December 13, 2021
- 11:04 AM
- 1

Researchers at the University of Darmstadt, Brescia, CNIT, and the Secure Mobile Networking Lab, have published a paper that proves it's possible to extract passwords and manipulate traffic on a WiFi chip by targeting a device's Bluetooth component.
Modern consumer electronic devices such as smartphones feature SoCs with separate Bluetooth, WiFi, and LTE components, each with its own dedicated security implementation.
However, these components often share the same resources, such as the antenna or wireless spectrum.
This resource sharing aims to make the SoCs more energy-efficient and give them higher throughput and low latency in communications.
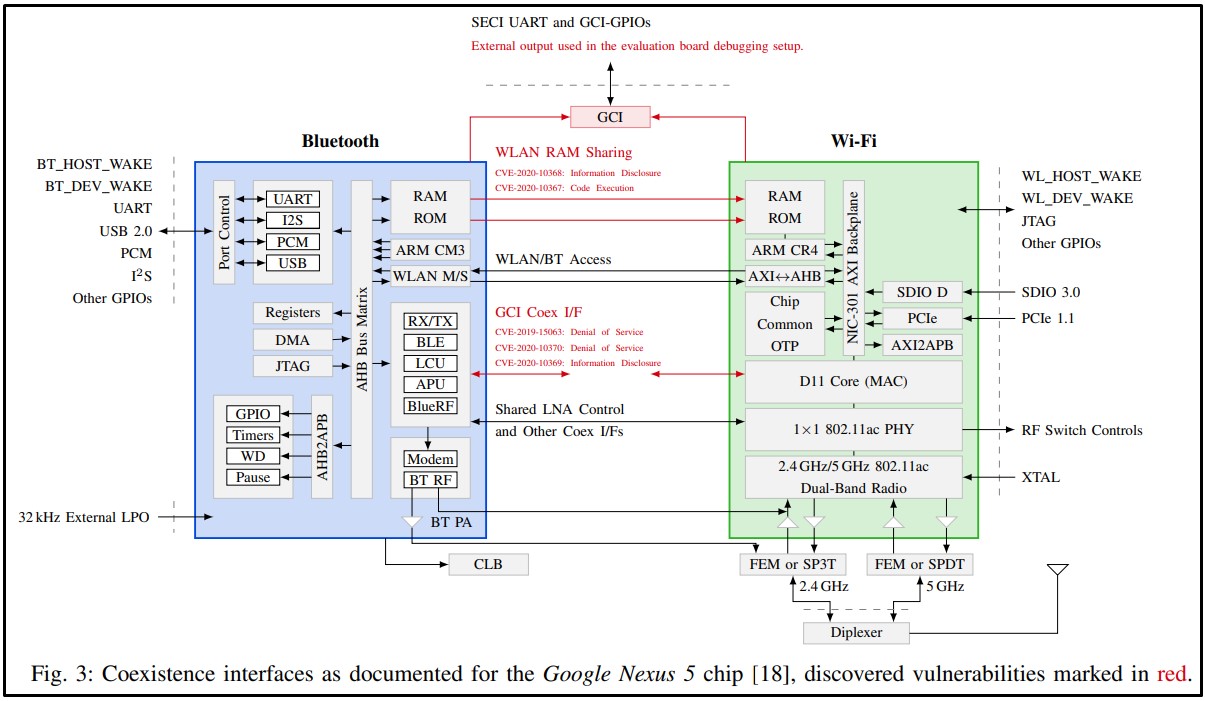
As the researchers detail in the recently published paper, it is possible to use these shared resources as bridges for launching lateral privilege escalation attacks across wireless chip boundaries.
The implications of these attacks include code execution, memory readout, and denial of service.
Source: Arxiv.org
Multiple flaws in architecture and protocol
To exploit these vulnerabilities, the researchers first needed to perform code execution on either the Bluetooth or WiFi chip. While this is not very common, remote code execution vulnerabilities affecting Bluetooth and WiFi have been discovered in the past.
Once the researchers achieved code execution on one chip, they could perform lateral attacks on the device's other chips using shared memory resources.
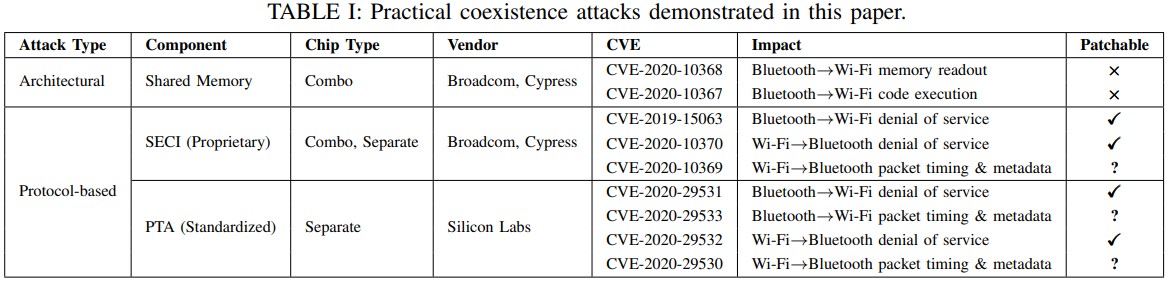
In their paper, the researchers explain how they could perform OTA (Over-the-Air) denial of service, code execution, extract network passwords, and read sensitive data on chipsets from Broadcom, Cypress, and Silicon Labs
Source: Arxiv.org
These vulnerabilities were assigned the following CVEs:
- CVE-2020-10368: WiFi unencrypted data leak (architectural)
- CVE-2020-10367: Wi-Fi code execution (architectural)
- CVE- 2019-15063: Wi-Fi denial of service (protocol)
- CVE-2020-10370: Bluetooth denial of service (protocol)
- CVE-2020-10369: Bluetooth data leak (protocol)
- CVE-2020-29531: WiFi denial of service (protocol)
- CVE-2020-29533: WiFi data leak (protocol)
- CVE-2020-29532: Bluetooth denial of service (protocol)
- CVE-2020-29530: Bluetooth data leak (protocol)
Some of the above flaws can only be fixed by a new hardware revision, so firmware updates cannot patch all the identified security problems.
-
Google pushes emergency Chrome update to fix zero-day used in attacks
Google has released Chrome 96.0.4664.110 for Windows, Mac, and Linux, to address a high-severity zero-day vulnerability exploited in the wild.
- December 13, 2021
- 05:31 PM
 1
1
-
TinyNuke info-stealing malware is again attacking French users
The info-stealing malware TinyNuke has re-emerged in a new campaign targeting French users with invoice-themed lures in emails sent to corporate addresses and individuals working in manufacturing, technology, construction, and business services.
- December 13, 2021
- 04:22 PM
 0
0
-
Phishing campaign uses PowerPoint macros to drop Agent Tesla
A new variant of the Agent Tesla malware has been spotted in an ongoing phishing campaign that relies on Microsoft PowerPoint documents laced with malicious macro code.
- December 13, 2021
- 03:49 PM
 0
0
-
Dell driver fix still allows Windows Kernel-level attacks
Dell's driver fix of the CVE-2021-21551 vulnerability leaves margin for catastrophic BYOVD attacks resulting in Windows kernel driver code execution.
- December 13, 2021
- 03:21 PM
 0
0
-
Kronos ransomware attack may cause weeks of HR solutions downtime
Workforce management solutions provider Kronos has suffered a ransomware attack that will likely disrupt many of their cloud-based solutions for weeks.
- December 13, 2021
- 12:57 PM
 0
0
-
Attackers can get root by crashing Ubuntu’s AccountsService
A local privilege escalation security vulnerability could allow attackers to gain root access on Ubuntu systems by exploiting a double-free memory corruption bug in GNOME's AccountsService component.
- December 13, 2021
- 12:05 PM
 0
0
-
Bugs in billions of WiFi, Bluetooth chips allow password, data theft
Researchers at the University of Darmstadt, Brescia, CNIT, and the Secure Mobile Networking Lab, have published a paper that proves it's possible to extract passwords and manipulate traffic on a WiFi chip by targeting a device's Bluetooth component.
- December 13, 2021
- 11:04 AM
 1
1
-
Ukraine arrests 51 for selling data of 300 million people in US, EU
Ukrainian law enforcement arrested 51 suspects believed to have been selling stolen personal data on hacking forums belonging to hundreds of millions worldwide, including Ukraine, the US, and Europe.
- December 13, 2021
- 09:09 AM
 1
1










No comments:
Post a Comment