Critical Solar Power Grid Vulnerabilities Risk Global Blackouts
Cybersecurity firm Bitdefender reveals critical vulnerabilities in solar power management platforms, putting 20% of global solar production at risk. Attackers could cause blackouts and disrupt power distribution. Learn about the vulnerabilities and how to protect your systems.
- A new report from cybersecurity firm Bitdefender has revealed major critical security vulnerabilities in two widely used platforms managing solar power systems, potentially impacting 20% of global solar power production.
The research focuses on Solarman, a major photovoltaic (PV) plant management platform, and Deye, a solar grid inverter platform. The platforms are interconnected, and the vulnerabilities, if exploited, could grant attackers control over inverter settings, potentially causing blackouts and disrupting power distribution worldwide.
Why worldwide?Solarman’s platform manages millions of installations worldwide, overseeing the production of approximately 195 gigawatts of solar power.
- full account takeover,
- token reuse, and
- excessive data exposure.
- hard-coded credentials,
- information leakage, and
- authorization token generation flaws.
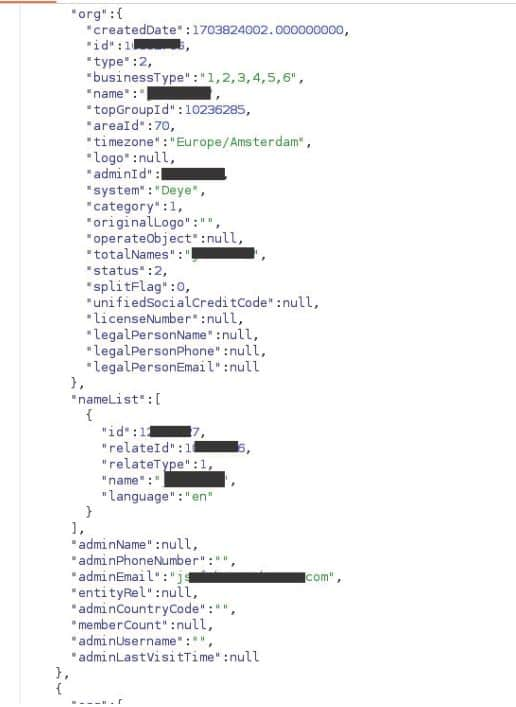
If exploited, these vulnerabilities could enable attackers to gain control over solar inverters, manipulating settings and potentially causing grid instability. The exploitation can also allow attackers to access sensitive information including extracting user data, and information on organizations and solar installations.
According to Bitdefender’s blog post shared with Hackread.com ahead of publishing on Wednesday 7 August 2024, the company has responsibly disclosed these vulnerabilities to the affected vendors, who have since implemented fixes.
- However, the researchers urge users and partners to ensure they are running the latest software updates for both Solarman and Deye platforms.
The report highlights the growing importance of cybersecurity in the energy sector, particularly as renewable energy sources like solar power become increasingly integrated into the grid.
The research will be presented at Defcon 32, a prominent cybersecurity conference, on August 9, 2024.
Controller flaws can let hackers physically damage moving bridges
Power Grids to Airports: TETRA Radio Hacking Risks Global System
ICS/OT
Vulnerabilities Exposed Widely Used Solar Power Systems to Hacking, Disruption
Vulnerabilities found in solar power systems could have been exploited by hackers to cause disruption and possibly blackouts
Researchers at cybersecurity firm Bitdefender claim to have found serious vulnerabilities in widely used solar power systems, potentially enabling attackers to cause disruption and blackouts.
- The security holes were found in the products of two companies, but their solutions are interconnected.
- Solarman develops solar management and monitoring solutions and
- Deye provides inverters, the component that converts DC electricity to AC and synchronizes the output with the power grid.
Details were disclosed by Bitdefender on Tuesday in separate papers documenting the Solarman and Deye vulnerabilities, as well as in a blog post titled ‘60 Hurts per Second – How We Got Access to Enough Solar Power to Run the United States’.
Other flaws could have been exploited to gain access to sensitive data, including personal information and location data for solar installations.
According to Bitdefender, exploitation of these vulnerabilities could have led to the disruption of power generation or voltage fluctuations, the exposure of sensitive information about users and organizations, and to cause disruptions that could lead to grid instability or blackouts.
Bitdefender said it reported its findings to Solarman and Deye in May and patches were deployed in the summer.
SecurityWeek has reached out to Solarman for comment and will update this article if the company responds.
“Integrating solar power into the grid offers immense benefits, but it also introduces attack surfaces that equipment makers must take into account. The security flaws found in the Deye and Solarman platforms highlight the need for robust cybersecurity in managing solar energy systems, as well as in general IoT setups,” Bitdefender said.
| Learn More at SecurityWeek’s ICS Cybersecurity Conference The leading global conference series for Operations, Control Systems and OT/IT Security professionals to connect on SCADA, DCS PLC and field controller cybersecurity. October 21-24, 2024 | Atlanta www.icscybersecurityconference.com |
Related: Exploited Solar Power Product Vulnerability Could Expose Energy Organizations to Attacks
Related: Research Shows How Solar Energy Installations Can Be Abused by Hackers
Eduard Kovacs (@EduardKovacs) is a managing editor at SecurityWeek. He worked as a high school IT teacher for two years before starting a career in journalism as Softpedia’s security news reporter. Eduard holds a bachelor’s degree in industrial informatics and a master’s degree in computer techniques applied in electrical engineering.















No comments:
Post a Comment