- They showed in a report published today that the vulnerability (named Sploitlight and described by Apple as a "logging issue") could be exploited to harvest valuable data, including Apple Intelligence-related information and remote information of other iCloud account-linked devices.

Attackers could use a recently patched macOS vulnerability to bypass Transparency, Consent, and Control (TCC) security checks and steal sensitive user information, including Apple Intelligence cached data.
TCC is a security technology and a privacy framework that blocks apps from accessing private user data by providing macOS control over how their data is accessed and used by applications across Apple devices.
Apple has fixed the security flaw tracked as CVE-2025-31199 (reported by Microsoft's Jonathan Bar Or, Alexia Wilson, and Christine Fossaceca) in patches released in March for macOS Sequoia 15.4 with "improved data redaction."
This includes, but is not limited to, photo and video metadata, precise geolocation data, face and person recognition data, user activity and event context, photo albums and shared libraries, search history and user preferences, as well as deleted photos and videos.
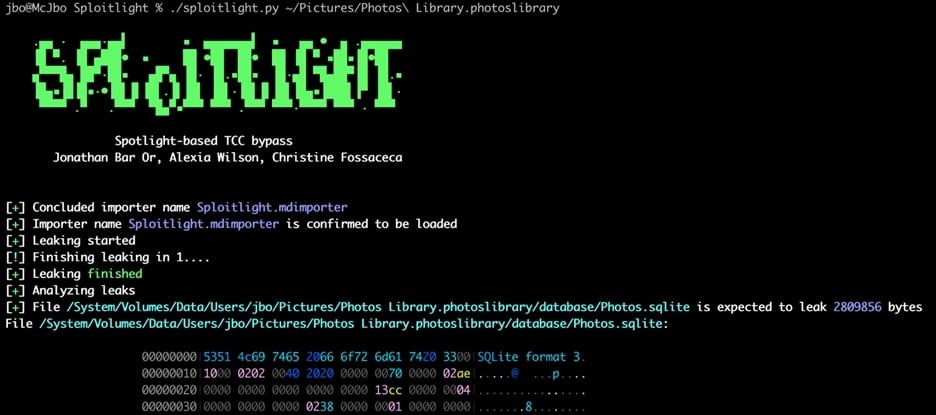
Since 2020, Apple has patched other TCC bypasses that exploit Time Machine mounts (CVE-2020-9771), environment variable poisoning (CVE-2020-9934), and a bundle conclusion issue (CVE-2021-30713). In the past, Microsoft security researchers have also discovered several other TCC bypasses, including powerdir (CVE-2021-30970) and HM-Surf, that could also be abused to gain access to users' private data.
"While similar to prior TCC bypasses like HM-Surf and powerdir, the implications of this vulnerability, which we refer to as 'Sploitlight' for its use of Spotlight plugins, are more severe due to its ability to extract and leak sensitive information cached by Apple Intelligence, such as precise geolocation data, photo and video metadata, face and person recognition data, search history and user preferences, and more," Microsoft said on Monday.
"These risks are further complicated and heightened by the remote linking capability between iCloud accounts, meaning an attacker with access to a user's macOS device could also exploit the vulnerability to determine remote information of other devices linked to the same iCloud account."
In recent years, Microsoft security researchers have found multiple other severe macOS vulnerabilities, including a SIP bypass dubbed 'Shrootless' (CVE-2021-30892), reported in 2021, which enables attackers to install rootkits on compromised Macs.
More recently, they discovered a SIP bypass dubbed 'Migraine' (CVE-2023-32369) and a security flaw named Achilles(CVE-2022-42821), which can be exploited to install malware using untrusted apps that bypass Gatekeeper execution restrictions.
LATEST ARTICLES
Lovense sex toy app flaw leaks private user email addresses
The connected sex toy platform Lovense is vulnerable to a zero-day flaw that allows an attacker to get access to a member's email address simply by knowing their username, putting them at risk of doxxing and harassment.
- July 28, 2025
- 10:39 PM
 0
0
How to conduct an AI risk assessment [Free Guide] 
Shadow AI is growing fast. Stay one step ahead.
Learn how to take a scalable approach to AI risk assessments so you can safeguard your org's proprietary data without blocking innovation.
Tea app leak worsens with second database exposing user chats
The Tea app data breach has grown into an even larger leak, with the stolen data now shared on hacking forums and a second database discovered that allegedly contains 1.1 million private messages exchanged between the app's members.
- July 28, 2025
- 04:55 PM
 1
1
Flaw in Gemini CLI AI coding assistant allowed stealthy code execution
A vulnerability in Google's Gemini CLI allowed attackers to silently execute malicious commands and exfiltrate data from developers' computers using allowlisted programs.
- July 28, 2025
- 03:40 PM
 0
0
Endgame Gear mouse config tool infected users with malware
Gaming peripherals maker Endgame Gear is warning that malware was hidden in its configuration tool for the OP1w 4k v2 mouse hosted on the official website between June 26 and July 9, 2025.
- July 28, 2025
- 02:48 PM
 0
0
Exploit available for critical Cisco ISE bug exploited in attacks
Security researcher Bobby Gould has published a blog post demonstrating a complete exploit chain for CVE-2025-20281, an unauthenticated remote code execution vulnerability in Cisco Identity Services Engine (ISE).
- July 28, 2025
- 01:29 PM
 0
0
CISA flags PaperCut RCE bug as exploited in attacks, patch now
CISA warns that threat actors are exploiting a high-severity vulnerability in PaperCut NG/MF print management software, which can allow them to gain remote code execution in cross-site request forgery (CSRF) attacks.
- July 28, 2025
- 12:59 PM
 0
0
Microsoft will stop supporting Windows 11 22H2 in October
Microsoft has reminded customers today that the last supported editions of Windows 11 22H2 will reach their end of servicing on October 14.
- July 28, 2025
- 11:52 AM
 0
0
OpenAI prepares GPT-5 for roll out
OpenAI's ChatGPT-5 could drop in the coming days, and it could be one of the best models from the Microsoft-backed startup.
- July 28, 2025
- 11:43 AM
 0
0
France's warship builder Naval Group investigates 1TB data breach
France's state-owned defense firm Naval Group is investigating a cyberattack after 1TB of allegedly stolen data was leaked on a hacking forum.
- July 28, 2025
- 11:31 AM
 0
0
OpenAI could rival Google Shopping with ChatGPT Shop
AI companies like OpenAI and Perplexity like to be the "everything company," and OpenAI's latest ChatGPT feature, "Shopping," makes that obvious.
- July 28, 2025
- 11:25 AM
 0
0
Internet Archive is now a US federal depository library
The Internet Archive has become an official U.S. federal depository library, providing online users with access to archived congressional bills, laws, regulations, presidential documents, and other U.S. government documents.
- July 28, 2025
- 11:19 AM
 0
0
Free Autoswagger Tool Finds the API Flaws Attackers Hope You Miss
Exposed API documentation is a gift-wrapped roadmap for threat actors. The free Autoswagger tool from Intruder scans for exposed docs and flags endpoints with broken access controls—before attackers find them.
- July 28, 2025
- 10:01 AM
 0
0
Access 56 languages with one $40 app and zero monthly payments
With the Qlango Language Learning platform, it feels more like a challenge you want to win. For just $39.99, you get lifetime access to an impressively deep platform where you can study 56 different languages, each packed with 6,679 essential words and real-world example sentences.
- July 28, 2025
- 07:12 AM
 0
0














No comments:
Post a Comment