Tuesday, June 29, 2021
FOR IMMEDIATE RELEASE: New Data: Mesa sees #3 largest monthly rent increase in June
- Rents in Mesa grew 3.0% in June, compared to 2.3% nationally. Mesa's monthly rent change ranks #3 among the nation's 100 largest cities.
- Rent prices in Mesa are currently 19.8% higher than they were one year ago, and 19.1% higher than they were last March, right before the start of the pandemic.
- Median rents in Mesa currently stand at $1224 for a 1-bedroom apartment and $1404 for a two-bedroom.
ON THE MESA CITY COUNCIL AGENDA: Proposed Audit Plan FY 2021/2022
| File #: | 20-1230 |
| Type: | Presentation | Status: | Agenda Ready |
| In control: | Audit, Finance and Enterprise Committee |
| On agenda: | 12/14/2020 |
| Title: | Hear a presentation, discuss, and provide a recommendation on the City's Comprehensive Annual Financial Report (CAFR) for Fiscal Year Ended June 30, 2020. |
| Attachments: | 1. Presentation, 2. 2020 CAFR |
Factors considered when selecting audits may include:
Requests or suggestions received from the City Council or City Manager Statutory mandates and/or volume of regulations (highly regulated vs. unregulated) Prior audit history or lack thereof Activities commonly susceptible to fraud Complexity of operations, significant changes in operations, or high turnover Cash handling volume and number of locations Impact and likelihood of potential adverse events (risk management/control failures)
1) Implemented as agreed2) Effective in resolving the underlying audit findings
Provide independent consulting/advisory servicesdata collectionvalidation, or analysisinternal control reviewsrisk analysesfinancial statement reviewsetc. as needed.
| File #: | 21-0727 |
| Type: | Presentation | Status: | Agenda Ready |
| In control: | City Council Study Session |
| On agenda: | 7/1/2021 |
| Title: | Hear a presentation, discuss, and provide direction on the proposed Audit Plan for FY 2021/22. |
| Attachments: | 1. Presentation, 2. FY 2021-2022 Audit Plan (Proposed) |
Current work in progress:• DoIT – Software/Application Management• Business Services/Purchasing – Procurement Processes• Fleet – Parts Management• Police – Badging Security Access• PCI DSS Annual Review• Audits planned for FY 2022• Follow-up reviews due in FY 2022• Other activities
New audits:• *Falcon Field – Leases• PRCF – Mesa Tennis Center• Police Department – Property and Evidence• Police Department – Criminal Investigations Case Management*Carried over from FY21 Audit Plan
• DoIT – Remote Access• Transportation – Street Maintenance• Community Services/Housing & Community Development – VASH Program
Follow-up reviews:• *PRCF – Convention Center Revenues• *HR/Employee Benefits – Claims Admin. Contract• Transient Lodging Tax • Police – Photo Safety Program*Delayed in FY 21 due to COVID-19
Arizona Gets Impacted by "Record-Breaking Temperatures" All The Time > But The Pacific Northwest Grabs All The Headlines
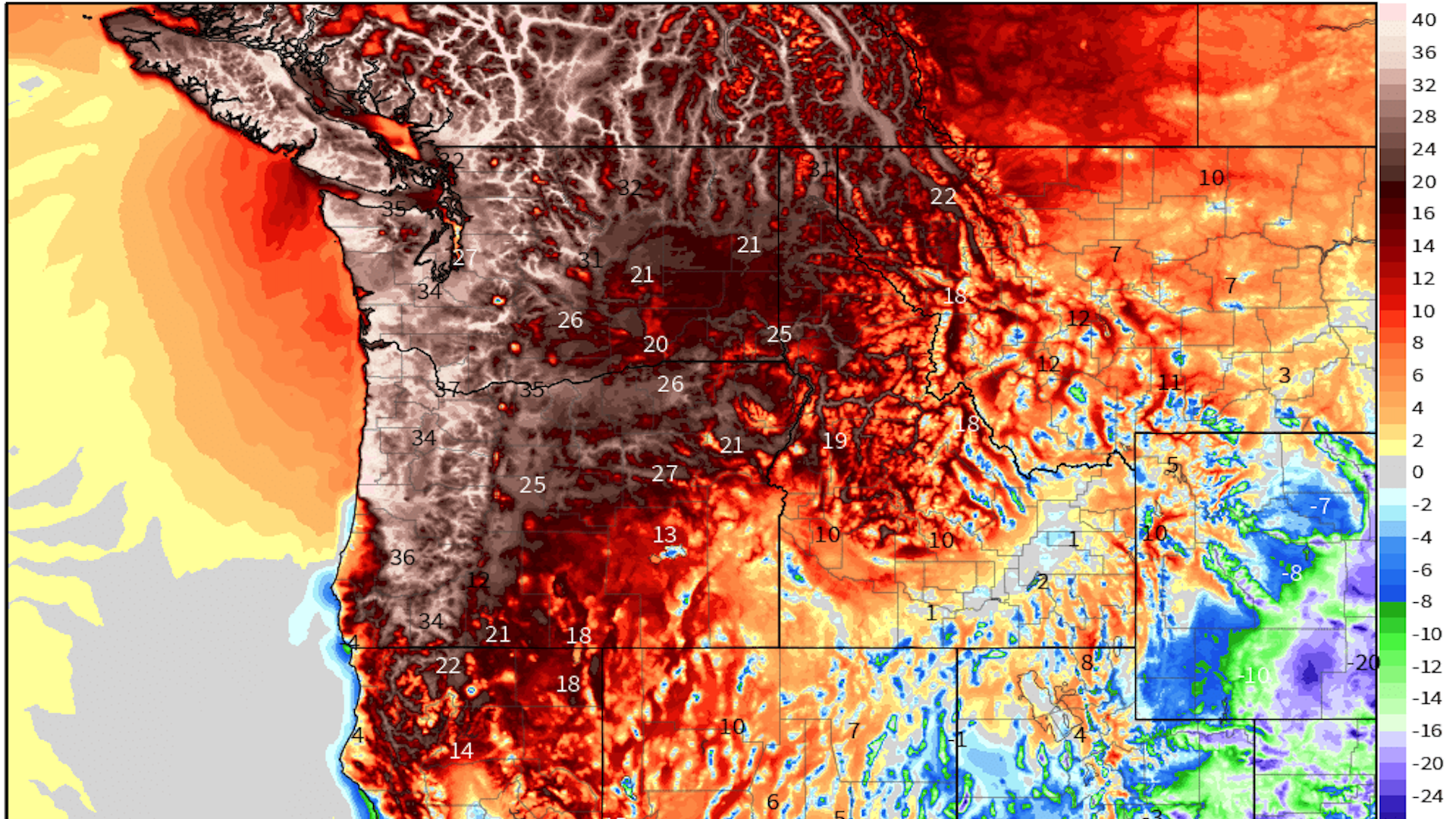
Pacific Northwest heat wave reaches astonishing peak on Monday
"The extraordinary heat wave that's stifling the Pacific Northwest reached its peak in many areas on Monday. Seattle smashed its all-time high-temperature record, set just the day before, by 4°F.
_____________________________________________________________________________
BIG WHOOP! In Arizona it's sometimes 5-10 or 15 degrees hotter than 'normal'
_____________________________________________________________________________
Why it matters: After two days of oppressive heat and little relief at night, the extreme weather event, boosted by global warming, is moving into a more dangerous phase.
- Heat illness tends to spike the longer heat waves last, and extreme heat is the No. 1 weather-related killer each year in the U.S.
Driving the news: A highly unusual weather pattern that statistically has less than a 1-in-several-thousand-year chance of occurring is in place over the Pacific Northwest, with a record-strong high-pressure area aloft — colloquially known as a "heat dome" — sitting over Washington state and British Columbia.
- This heat dome is yielding temperatures 25–50°F above average across multiple states and British Columbia.
- This heat, combined with a worsening drought, is raising the risk of wildfires across multiple Western states, with some large blazes erupting in California Sunday and Monday.
- It is also causing power demand to spike at a time when hydropower resources are lower than usual.
- The heat was so severe Monday that pavement buckled across the Seattle and Portland metro areas.
By the numbers: All of Oregon, Washington and Idaho, plus portions of California, Montana and Nevada, are under excessive heat watches and warnings.
- Portland, Oregon, set an all-time high temperature of 112°F on Sunday, and eclipsed that on Monday, with a high of 115°F.
- In Seattle, the temperature reached 104°F on Sunday, which broke the existing all-time record. It exceeded this on Monday, reaching 108°F.
- Before this weekend, Seattle had never had back-to-back 100-degree days, and only saw three such days on record. But now, the century mark was exceeded three days in a row.
- A preliminary state record of 118°F was tied in Dallesport, Washington.
- Canada is also seeing extreme heat, with the country's June high-temperature record tied on Saturday and smashed on Sunday at Lytton in British Columbia by nearly 3°F, with a high of 116°F. This was broken again Monday, with the same location recording 117.5°F.
Of note: To put this into perspective, this means that a location in British Columbia, not known as an extremely hot province in June, equaled Las Vegas' all-time hottest temperature.
- Mountain areas in the Northwest have been extremely warm with freezing levels located above the peak of Mount Rainier at times. This is resulting in rapidly melting snow and ice, from the peaks of Oregon to the mountains of British Columbia.
How it works: There are three main reasons the Pacific Northwest is so hot. The first is tied to the heat dome itself, which causes air to sink, or compress, warming as it does so and keeping skies clear. The second has to do with the location of the heat dome.
- The feature is parked to the north-northeast of the region, at the same time as an upper-level low-pressure area lurks offshore.
- Due to the clockwise flow of air around the high pressure, easterly winds are blowing from high-to-low elevation areas, adding even more compressional cooling.
The third fact is climate change. Studies have shown that severe heat events such as this one are now on average about 3–5°F hotter than they would be without the many decades of emissions of greenhouse gases from fossil fuel burning, deforestation and other human activities.
- However, this understates climate change's influence, researchers told Axios, as warming is also thought to be altering weather patterns in a way that makes strong heat domes more common and prolonged.
- Climate scientists warn that this event demonstrates how climate change plus natural weather variability are pushing society beyond our ability to cope.
What they're saying: "We have made trillions of small adaptations to optimize our society for the historical range of temperature, precipitation, etc., that we have experienced," Andrew Dessler, a climate researcher at Texas A&M University, told Axios via email.
- "As the climate changes, that range is no longer the relevant one, and the mismatch between what we are adapted for and what we actually experience can generate huge negative impacts that seem to suddenly appear out of nowhere — even though we've been predicting them for literally decades," he said.
IN THE PUBLIC INTEREST: Crossing-Over The Electronic Frontier Into The 'Brave New World' of Total Surveillance
[VISUAL] The Overlapping Infrastructure of Urban Surveillance, and How to Fix It

Between the increasing capabilities of local and state police, the creep of federal law enforcement into domestic policing, the use of aerial surveillance such as spy planes and drones, and mounting cooperation between private technology companies and the government, it can be hard to understand and visualize what all this overlapping surveillance can mean for your daily life. We often think of these problems as siloed issues. Local police deploy automated license plate readers or acoustic gunshot detection. Federal authorities monitor you when you travel internationally.
But if you could take a cross-section of the average city block, you would see the ways that the built environment of surveillance—its physical presence in, over, and under our cities—makes this an entwined problem that must be combatted through entwined solutions.
Thus, we decided to create a graphic to show how—from overhead to underground—these technologies and legal authorities overlap, how they disproportionately impact the lives of marginalized communities, and the tools we have at our disposal to halt or mitigate their harms.

Going from Top to Bottom:
1. Satellite Surveillance:
Satellite photography has been a reality since the 1950s, and at any given moment there are over 5,000 satellites in orbit over the Earth—some of which have advanced photographic capabilities. While many are intended for scientific purposes, some satellites are used for reconnaissance by intelligence agencies and militaries. There are certainly some satellites that may identify a building or a car from its roof, but it’s unlikely that we could ever reach the point where pictures taken from a satellite would be clear enough or could even be the correct angle to run through face recognition technology or through an automated license plate reader.
Satellites can also enable surveillance by allowing governments to intercept or listen in on data transmitted internationally.
2. Internet Traffic Surveillance
Government surveillance of internet traffic can happen in many ways. Through programs like PRISM and XKEYSCORE, the U.S. National Security Agency (NSA) can monitor emails as they move across the internet, browser and search history, and even keystrokes as they happen in real time. Much of this information can come directly from the internet and telecommunications companies that consumers use, through agreements between these companies and government agencies (like the one the NSA shares with AT&T) or through warrants or orders granted by a judge, including those that preside over the Foriegn Intelligence Surveillance Court (FISC).
Internet surveillance isn’t just the domain of the NSA and international intelligence organizations; local law enforcement are just as likely to approach big companies in an attempt to get information about how some people use the internet. In one 2020 case, police sent a search warrant to Google to see who had searched the address of an arson victim to try to identify a suspect. Using the IP addresses Google furnished of users who conducted that search, police identified a suspect and arrested him for the arson.
How can we protect our internet use? FISA reform is one big one. Part of the problem is also transparency: in many instances it's hard to even know what is happening behind the veil of secrecy that shrouds the American surveillance system.

3. Cellular Communications (Tower) Surveillance
Cell phone towers receive information from our cell phones almost constantly, such as the device’s location, metadata like calls made and the duration of each call, and the content of unencrypted calls and text messages. This information, which is maintained by telecom companies, can be acquired by police and governments with a warrant. Using encrypted communication apps, such as Signal, or leaving your cell phone at home when attending political demonstrations are some ways to prevent this kind of surveillance.

4. Drones
Police departments and other local public safety agencies have been acquiring and deploying drones at a rapid rate. This is in addition to federal drones used both overseas and at home for surveillance and offensive purposes. Whether at the border or in the largest U.S. cities, law enforcement claim drones are an effective method for situational awareness or for use in situations too dangerous for an officer to approach. The ability for officers to use a drone in order to keep their distance was one of the major reasons police departments around the country justified the purchase of drones as a method of fighting the COVID-19 pandemic.
However, drones, like other pieces of surveillance equipment, are prone to “mission creep”: the situations in which police deploy certain technologies often far overreach their intended purpose and use. This is why drones used by U.S. Customs and Border Protection, whose function is supposedly to monitor the U.S. border, were used to surveil protests against police violence in over 15 cities in the summer of 2020, many hundreds of miles from the border.
It’s not only drones that are in the skies above you spying on protests and people as they go about their daily lives. Spy planes, like those provided by the company Persistent Surveillance Systems, can be seen buzzing above cities in the United States. Some cities, however, like Baltimore and St. Louis, have recently pulled the plug on these invasive programs.
Drones flying over your city could be at the behest of local police or federal agencies, but as of this moment, there are very few laws restricting when and where police can use drones or how they can acquire them. Community Control Over Police Surveillance, or CCOPS ordinances, are one such way residents of a city can prevent their police from acquiring drones or restrict how and when police can use them. The Fourth Circuit court of appeals has also called warrantless use of aerial surveillance a violation of the Fourth Amendment.

5. Social Media Surveillance
Federal, local, and state governments all conduct social media surveillance in a number of different ways—from sending police to infiltrate political or protest-organizing Facebook groups, to the mass collection and monitoring of hashtags or geolocated posts done by AI aggregators.
There are few laws governing law enforcement use of social media monitoring. Legislation can curb mass surveillance of our public thoughts and interactions on social media by requiring police to have reasonable suspicion before conducting social media surveillance on individuals, groups, or hashtags. Also, police should be barred from using phony accounts to sneak into closed-access social media groups, absent a warrant.

6. Cameras
Surveillance cameras, either public or private, are ubiquitous in most cities. Although there is no definitive proof that surveillance cameras reduce crime, cities, business districts, and neighborhood associations continue to establish more cameras, and equip those cameras with increasingly invasive capabilities.
Face recognition technology (FRT), which over a dozen cities across the United States have banned government agencies from using, is one such invasive technology. FRT can use any image—taken in real-time or after-the-fact—and compare it to pre-existing databases that contain driver’s license photos, mugshots, or pre-existing CCTV camera footage. FRT has a long history of misidentifying people of color and trans* and nonbinary people, even leading to wrongful arrests and police harassment. Other developing technology, such as more advanced video analytics, can allow users to search footage accumulated from hundreds of cameras by things as specific as “pink backpack” or “green hair.”
Networked surveillance cameras can harm communities by allowing police, or quasi-governmental entities like business improvement districts, by recording how people live their lives, who they communicate with, what protests they attend, and what doctors or lawyers they visit. One way to lessen the harm surveillance cameras can cause in local neighborhoods is through CCOPS measures that can regulate their use. Communities can also band together to join more than a dozen cities around the country that have banned government use of FRT and other biometrics.
TELL congress: END federal use of face surveillance

7. Surveillance of Cell Phones
Cell phone surveillance can happen in a number of ways, based on text messages, call metadata, geolocation, and other information collected, stored, and disseminated by your cell phone every day. Government agencies at all levels, from local police to international intelligence agencies, have preferred methods of conducting surveillance on cell phones.
For instance, local and federal law enforcement have been known to deploy devices known as Cell-Site Simulators or “stingrays,” which mimic cell phone towers your phone automatically connects to in order to harvest information from your phone like identifying numbers, call metadata, the content of unencrypted text messages, and internet usage.
Several recent reports revealed that the U.S. government purchases commercially available data obtained from apps people downloaded to their phones. One report identified the Department of Defense’s purchase of sensitive user data, including location data, from a third-party databroker of information obtained through apps targeted at Muslims, including a prayer app with nearly 100 million downloads. Although the government would normally need a warrant to acquire this type of sensitive data, purchasing the data commercially allows them to evade constitutional constraints.
One way to prevent this kind of surveillance from continuing would be to pass the Fourth is Not For Sale Act, which would ban the government from purchasing personal data that would otherwise require a warrant. Indiscriminate and warrantless government use of stingrays is also currently being contested in several cities and states and a group of U.S. Senators and Representatives have also introduced legislation to ban their use without a warrant. CCOPS ordinances have proven a useful way to prevent police from acquiring or using Cell-Site Simulators.

8. Automated License Plate Readers
Automated license plate readers (ALPRs) are high-speed, computer-controlled camera systems that are typically mounted on street poles, streetlights, highway overpasses, mobile trailers, or attached to police squad cars. ALPRs automatically capture all license plate numbers that come into view, along with the location, date, and time of the scan. The data, which includes photographs of the vehicle and sometimes its driver and passengers, is then uploaded to a central server.
Taken in the aggregate, ALPR data can paint an intimate portrait of a driver’s life and even chill First Amendment protected activity. ALPR technology can be used to target drivers who visit sensitive places such as health centers, immigration clinics, gun shops, union halls, protests, or centers of worship.
ALPRs can also be inaccurate. In Colorado, police recently pulled a Black family out of their car at gunpoint after an ALPR misidentified their vehicle as one that had been reported stolen. Too often, technologies like ALPRs and face recognition are used not as an investigative lead to be followed up and corroborated, but as something police rely on as a definitive accounting of who should be arrested.
Lawmakers should better regulate this technology by limiting “hotlists” to only cars that have been confirmed stolen, rather than vehicles labeled as “suspicious”, and to limit retention of ALPR scans of cars that are not hotlisted.

9. Acoustic Gunshot Detection
Cities across the country are increasingly installing sophisticated listening devices on street lights and the sides of buildings intended to detect the sound of gunshots. Acoustic gunshot detection, like the technology sold by popular company ShotSpotter, detects loud noises, triangulates where those noises came from, and sends the audio to a team of experts who are expected to determine if the sound was a gunshot, fireworks, or some other noise.
Recent reports have shown that the number of false reports generated by acoustic gunshot detection may be much higher than previously thought. This can create dangerous situations for pedestrians as police arrive at a scene armed and expecting to encounter someone with a gun.
Even though aimed at picking up gunshots, this technology also captures human voices, at least some of the time. In at least two criminal cases, the People v. Johnson (CA) and Commonwealth v. Denison (MA), prosecutors sought to introduce as evidence audio of voices recorded on an acoustic gunshot detection system. In Johnson, the court allowed this. In Denison, the court did not, ruling that a recording of “oral communication” is prohibited “interception” under the Massachusetts Wiretap Act.
While the accuracy of the technology remains a problem, one way to mitigate its harm is for activists and policymakers to work to ban police and prosecutors from using voice recordings collected by gunshot detection technology as evidence in court.
10. Internet-Connected Security Cameras
Popular consumer surveillance cameras like Amazon’s Ring doorbell camera are slowly becoming omnipresent surveillance networks in the country. Unlike traditional surveillance cameras which may back up to a local drive in the possession of the user, the fact that users of internet connected security cameras do not store their own footage makes that footage more easily accessible to police. Often police can bypass users altogether by presenting a warrant directly to the company.
These cameras are ubiquitous but there are ways we can help blunt their impact on our society. Opting in to encrypt your Amazon Ring footage and opting out of seeing police footage requests on the Neighbors app are two ways to ensure police have to bring a warrant to you, rather than Amazon, if they think your camera may have witnessed a crime.
11. Electronic Monitoring
Electronic monitoring is a form of digital incarceration, often in the form of a wrist bracelet or ankle “shackle” that can monitor a subject’s location, and sometimes their blood alcohol level.
Monitors are commonly used as a condition of pretrial release, or post-conviction supervision, like probation or parole. They are sometimes used as a mechanism for reducing jail and prison populations. Electronic monitoring has also been used to track juveniles, immigrants awaiting civil immigration proceedings, and adults in drug rehabilitation programs.
Not only does electronic monitoring impose excessive surveillance on people returning home from incarceration, but it also hinders their ability to successfully transition back into the community. Additionally, there is no concrete evidence that electronic monitoring reduces crime rates or recidivism.
12. Police GPS Tracking
One common method that police attempt to track people suspected of criminal activity is GPS monitors placed underneath a person’s vehicle. Before the 2012 U.S. Supreme Court decision in United States v Jones, which ruled that a GPS monitor on a car constituted a search under the Fourth Amendment, and the 2013 Katzin decision in the Third Circuit which ruled, once and for all, that police need a warrant in order to install a GPS device, police often used these devices with few restrictions.
However, recent court filings indicate that law enforcement believes that warrantless use of GPS tracking devices at the border is fair game. EFF currently has a pending Freedom of Information Act lawsuit to uncover CBP’s and U.S. Immigration and Customs Enforcement’s (ICE) policies, procedures, and training materials on the use of GPS tracking devices.
13. International Internet Traffic Surveillance
Running under ground and under the oceans are thousands of miles of fiber optic cable that transmit online communications between countries. Originating as telegraph wires running under the ocean, these highways for international digital communication are now a hotbed of surveillance by state actors looking to surveil chatter abroad and at home. The Associated Press reported in 2005 that the U.S. Navy had sent submarines with technicians to help tap into the “backbone of the internet.” These cables make landfall at coastal cities and towns called “landing areas” like Jacksonville, Florida and Myrtle Beach, South Carolina and towns just outside of major cities like New York, Los Angeles, San Diego, Boston, and Miami.
How do we stop the United States government from tapping into the internet’s main arteries? Section 702 of the Foreign Intelligence Surveillance Act allows for the collection and use of digital communications of people abroad, but often scoops up communications of U.S. persons when they talk to friends or family in other countries. EFF continues to fight Section 702 in the court in hopes of securing communications that travel through these essential cables.
TELL congress: END federal use of face surveillance
-
Flash News: Ukraine Intercepts Russian Kh-59 Cruise Missile Using US VAMPIRE Air Defense System Mounted on Boat. Ukrainian forces have made ...





