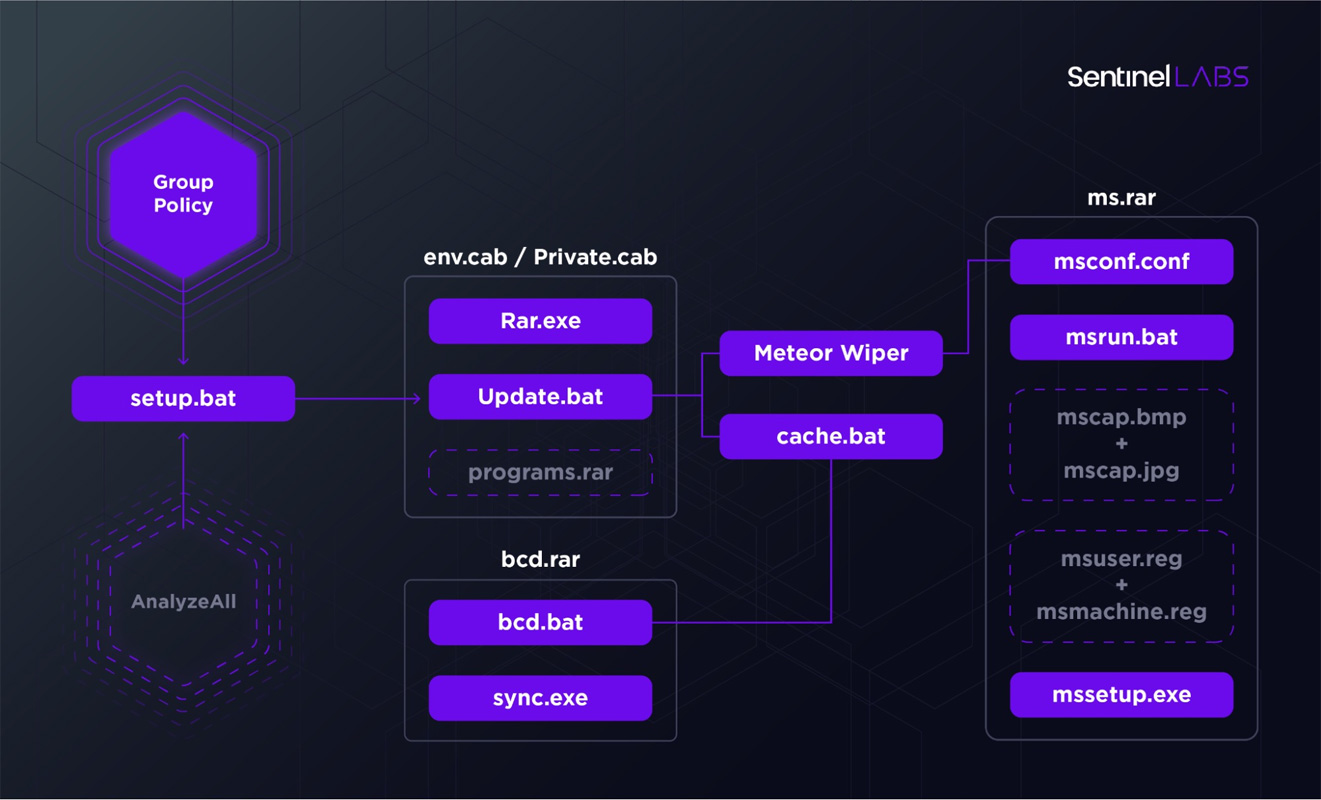
Ancient Gilgamesh tablet seized from Hobby Lobby by US authorities
The craft store had acquired the 3,600-year-old artefact for its Bible museum, but court says it had been smuggled and should be returned to Iraq

Hobby Lobby Forfeits Rare Gilgamesh Tablet Smuggled From Iraq
The arts and crafts chain is once again under scrutiny for its collecting practices
Known as the “Gilgamesh Dream Tablet,” the artifact is inscribed in the Akkadian language and details a dream sequence from the ancient epic, according to Agence France-Presse (AFP). It is around 3,500 years old and originated in modern-day Iraq.
Hobby Lobby's Illegal Antiquities Shed Light On A Lost, Looted Ancient City In Iraq

Ancient artifacts seized from Hobby Lobby are shown at a May 2 event returning the artifacts to Iraq in Washington, D.C. The seized artifacts include cuneiform tablets from the little-known ancient city of Irisagrig. Win McNamee/Getty Images
Archaeologist Eckart Frahm didn't have much time to determine where the 4,000-year-old clay tablets had come from. Homeland Security officials had given him just 2 1/2 days in a dimly lit New York warehouse to pore over the cuneiform inscriptions etched into the fragile, ancient pieces and report back.
"They were not in great shape. They had infestations of salt in them, so it's not that I could say I had been able to read everything," says the Yale University professor. "My main goal was to provide a general assessment from when and where did these tablets actually originate."
Frahm determined the tablets at the center of a federal case against the Oklahoma-based Hobby Lobby arts and crafts chain were from a place few had ever heard of — an ancient Sumerian city called Irisagrig.
"You could argue that this is a lost city because this place has never been properly excavated and you don't even know exactly where it is," Frahm tells NPR.
But looters know. The roughly 250 tablets Frahm examined in 2016 were among 5,500 objects, including ancient cylinder seals and clay seal impressions known as bullae, smuggled into the U.S. starting in 2010. Shipped from the United Arab Emirates and Israel without declaring their true Iraqi origin, some of them were marked "ceramic tiles" or "clay tiles (sample)."
They'd been purchased by Hobby Lobby for $1.6 million.
In a settlement last year with the Justice Department, Hobby Lobby agreed to forfeit the objects and paid a $3 million fine. In May, about 3,800 objects were handed back to the Iraqi government at a ceremony at its Washington, D.C., embassy, and will be returned to Iraq later this year.
Last November, Hobby Lobby president Steve Green, the son of the craft store chain's founder David Green, opened a Museum of the Bible in Washington, D.C., which contains another $201 million worth of ancient artifacts tied to Hobby Lobby. . .
Those tablets marked the first time archaeologists were known to have seen the name Irisagrig. According to one of the cuneiform tablets, it took four days to tow boats upstream from Umma, a better-known ancient Sumerian city, giving Molina a rough probable location of the lost city in the south of the country.
Umma itself is one of the most heavily looted of all known ancient sites in Iraq. Thieves dug hundreds of holes into the tells — the mounds under which the ancient city is buried — after security collapsed following the 2003 U.S. invasion.

The remains of thousands of other ancient towns and cities likely exist under other mounds, archaeologists believe.
 "Don't forget, even if we take only ancient Iraq, it's 3,000 years — so they didn't live in just one or two cities," says Lamia al-Gailani, a British-Iraqi archaeologist with the Iraq Museum in Baghdad and the University of London's School of Oriental and African Studies. . .
"Don't forget, even if we take only ancient Iraq, it's 3,000 years — so they didn't live in just one or two cities," says Lamia al-Gailani, a British-Iraqi archaeologist with the Iraq Museum in Baghdad and the University of London's School of Oriental and African Studies. . .
> Frahm says apart from the Irisagrig archive, the Hobby Lobby artifacts that are being returned to Iraq also include tablets dating from about 2500 BCE (an alternative to "B.C." commonly used by scholars to denote "before the common era") with incantations to the gods, Babylonian letters from between 1900 and 1700 BCE and hymns from several hundred years BCE.
Frahm describes the incantations as some of the most important pieces in the collection. The tablets, about 300 years older than the Irisagrig tablets, invoke three Mesopotamian gods. He says another text from the first millennium BCE is written in both Babylonian and Emesal, a dialect of Sumerian he says was originally a language used only by women.