Sunday, November 21, 2021
BLEEPING COMPUTER: Release of Mostly New Ransomware Research... Week of Nov 19 2021
Emotet botnet comeback orchestrated by Conti ransomware gang
The Emotet botnet is back by popular demand, resurrected by its former operator, who was convinced by members of the Conti ransomware gang
READ MORE
The Week in Ransomware - November 19th 2021 - Targeting Conti
November 13th 2021
dnwls0719 found a new ransomware that appends the .dst extension and expects users to use IRC over Tor to negotiate.
November 14th 2021
The US Department of Education and Department of Homeland Security (DHS) were urged this week to more aggressively strengthen cybersecurity protections at K-12 schools across the nation to keep up with a massive wave of attacks.
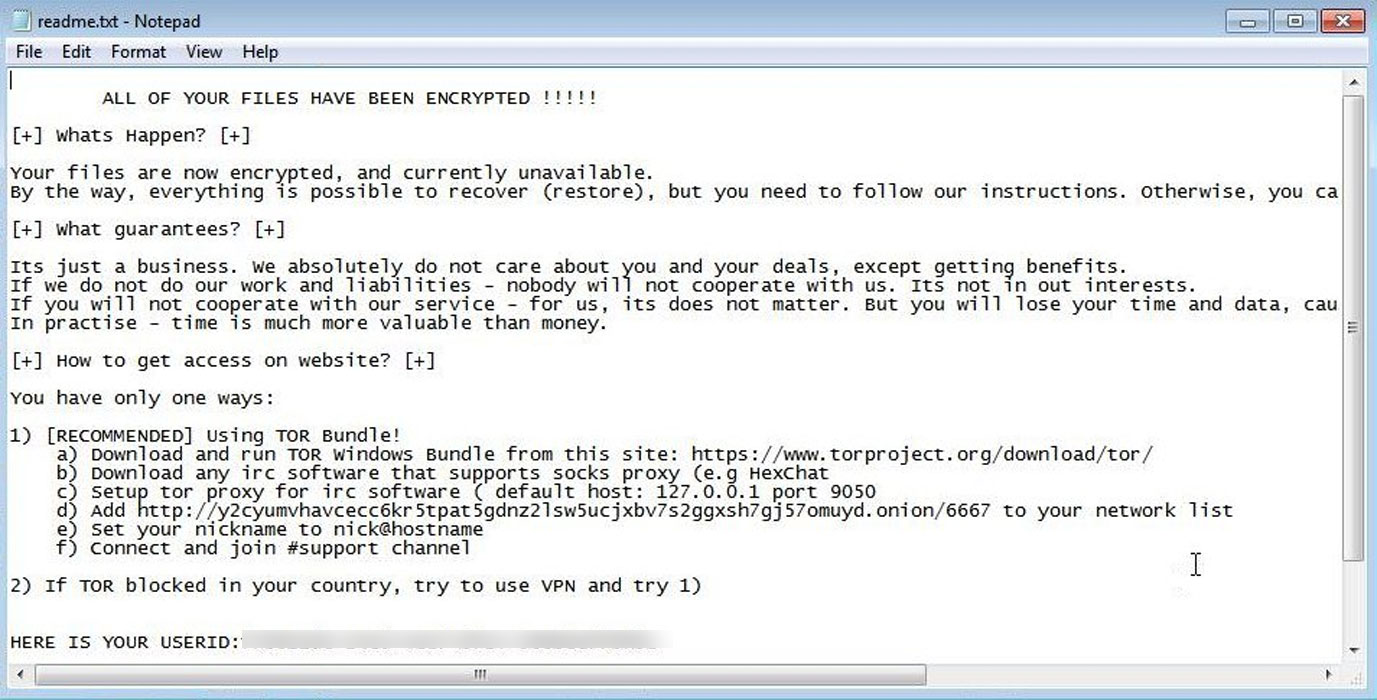
Amigo-A found a new ransomware in our forums called RansomNow that drops the HELP - README TO UNLOCK FILES.txt ransom note and does not append a new extension.
November 15th 2021
A new hacker group named Moses Staff has recently claimed responsibility for numerous attacks against Israeli entities, which appear politically motivated as they do not make any ransom payment demands.
PCrisk found a new STOP ransomware variant that appends the .futm extension.
November 16th 2021
Cryptomixers have always been at the epicenter of cybercrime activity, allowing hackers to "clean" cryptocurrency stolen from victims and making it hard for law enforcement to track them.
A new wave of attacks starting late last week has hacked close to 300 WordPress sites to display fake encryption notices, trying to trick the site owners into paying 0.1 bitcoin for restoration.
Many of the people on the FBI's cyber most wanted list are Russian. While some allegedly work for the government earning a normal salary, others are accused of making a fortune from ransomware attacks and online theft. If they left Russia they'd be arrested - but at home they appear to be given free rein.
Today, Carolyn B. Maloney, Chairwoman of the Committee on Oversight and Reform, released a supplemental memo providing new insights into how the high-profile ransomware attacks on CNA Financial Corporation (CNA), Colonial Pipeline Company (Colonial), and JBS Foods USA (JBS) unfolded, and how legislation and policies responses may be developed to counter the threat of ransomware.
dnwls0719 found a new ransomware that appends the .chichi extension.
PCrisk found a new STOP ransomware variant that appends the .utjg extension.
November 17th 2021
??? There's some unusual activity brewing on Russian-speaking cybercrime forums, where hackers appear to be reaching out to Chinese counterparts for collaboration
November 18th 2021
PRODAFT Threat Intelligence (PTI) Team has obtained valuable insights on the inner workings of the Conti ransomware group. The PTI team accessed Conti’s infrastructure and identified the real IP addresses of the servers in question. This report provides unprecedented detail into the way the Conti ransomware gang works, how they select their targets, how many targets they’ve breached, and more.
A new ransomware group called Memento takes the unusual approach of locking files inside password-protected archives after their encryption method kept being detected by security software.
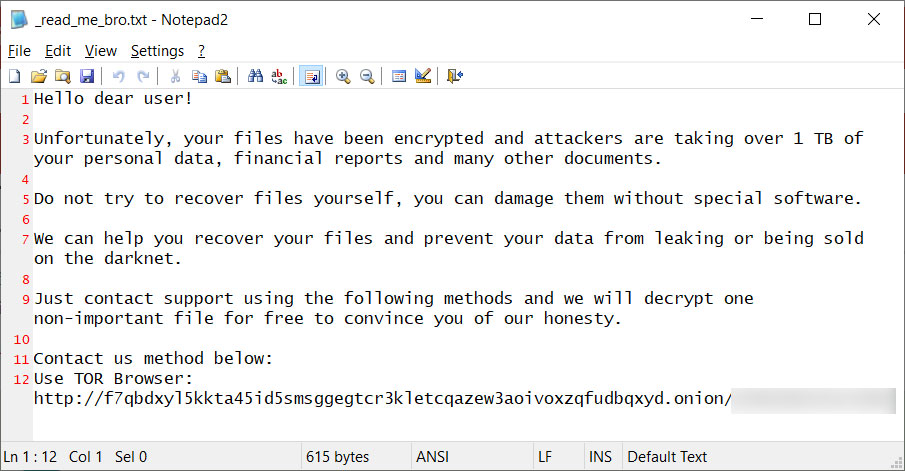
S!Ri found a new HelloKitty ransomware variant that appends the .boombye extension and drops a ransom note named _read_me_bro.txt.
November 19th 2021
US federal bank regulatory agencies have approved a new rule ordering banks to notify their primary federal regulators of significant computer-security incidents within 36 hours. . ."
Saturday, November 20, 2021
Hedge Fund Bilionaire Ken Griffin - the CEO and founder of Citadel - Outbid A collective of crypto enthusiasts, calling themselves ConstitutionDAO
It turns out the way to beat the collective will of the internet’s cryptocurrency fans is to have way, way more money than them. Ken Griffin, the CEO and founder of Citadel, has revealed himself as the winner of last night’s $43.2 million auction for a rare copy of the US Constitution.
A collective of crypto enthusiasts, calling themselves ConstitutionDAO, managed to raise $47 million in about a week’s time in a quixotic attempt to win the document themselves and put it on display to the public for free.
A hedge fund billionaire outbid crypto investors for a rare copy of the US Constitution
/cdn.vox-cdn.com/uploads/chorus_image/image/70167732/530884400.0.jpg)
The document sold for $43 million on Thursday night
WE ALL JUST GOT PUNKED IN KENOSHA RITTENHOUSE TRIAL: Toxic Deadly Use-of-Force White-On-White Attacks at A Black Lives Matter Protest
Verdict aside, the embarrassing Rittenhouse trial should be a warning

"No matter how liberal activists try to paint it, the jury served justice in the Kyle Rittenhouse murder trial, though the state’s conduct and pundits’ painting of events made the entire ordeal a warning for where we are headed. The Rittenhouse trial, irrelevant of its outcome, was an embarrassment for the Wisconsin and US justice system as a whole. It’s telling that, while this case involved two dead victims, Anthony Huber and Joseph Rosenbaum, and an 18-year-old on trial for his life, two other characters became lightning rods for controversy and attention. > Lead prosecutor Thomas Binger spent the better part of the Kenosha trial confusing Rittenhouse, Judge Bruce Schroeder, and anyone else that bothered listening to him. His arguments in the case fell apart quickly and faced heavy scrutiny from both the judge and activists, as almost nothing he said appeared to have any basis either in law or the Constitution While questioning Rittenhouse on the stand, Binger pulled an homage to former Fox News host Bill O’Reilly post-Columbine shooting, and went on a tear against video games, attempting to paint Rittenhouse as some first-person-shooter-obsessed incel, looking for death in Kenosha, Wisconsin in August of 2020 during a Black Lives Matter protest that had already turned violent. The video-game argument didn’t work, so Binger then employed two very questionable tactics: First, he tried arguing that, because Rittenhouse had an AR-15 semi-automatic rifle in his possession, he arrived in Kenosha with the intent of causing harm, which is something the young man has denied, saying he was there with a medical kit to assist people who might need help. Binger attempted to further this argument in his closing remarks by claiming that “you lose the right to self-defense when you’re the one who brought the gun.” Shocked Second Amendment activists rightly pointed out that this thinking completely undermined the very idea of self-defense. _____________________________________________________________________________________The only way such a theory could have held any weight was if Rittenhouse had been the primary aggressor. But witness statements have backed up his recollection of events: a videographer testified that the defendant was attacked first, while Gaige Grosskreutz – one of the three who was shot, though he survived – admitted to pointing a gun at Rittenhouse before Rittenhouse pointed his gun at him. Prior to Rittenhouse firing, he was being chased by Grosskeutz, Huber, and Rosenbaum, who were attempting to get his weapon. [...] Binger’s arguments had no legal basis because they were merely half-hearted attempts to try to bring sense to the Twitter debates that filtered Rittenhouse’s actions and somehow determined he was a racist, intent on hunting down righteous liberal protesters. _____________________________________________________________________________________> Judge Bruce Schroeder was also the subject of heavy criticism during the trial, though the basis for it seemed to be similar to that received by Rittenhouse, with critics mostly spider-webbing negative theories derived from nonsense such as the ringtone to his phone being Lee Greenwood’s ‘God Bless the USA’.
DNS TUNNELING AND OTHER EVASIVE TECHNIQUES: A Disturbing Trend That Attackers Are Becoming Stealthier Encroaching In Open Source Software
Intro: from ArsTechnica
Malware downloaded from PyPI 41,000 times was surprisingly stealthy
Malware infiltrating open source repositories is getting more sophisticated.

"PyPI—the open source repository that both large and small organizations use to download code libraries—was hosting 11 malicious packages that were downloaded more than 41,000 times in one of the latest reported such incidents threatening the software supply chain.
JFrog, a security firm that monitors PyPI and other repositories for malware, said the packages are notable for the lengths its developers took to camouflage their malicious code from network detection. Those lengths include a novel mechanism that uses what’s known as a reverse shell to proxy communications with control servers through the Fastly content distribution network. Another technique is DNS tunneling, something that JFrog said it had never seen before in malicious software uploaded to PyPI.
A powerful vector
“Package managers are a growing and powerful vector for the unintentional installation of malicious code, and as we discovered with these 11 new PyPI packages, attackers are getting more sophisticated in their approach, Shachar Menashe, senior director of JFrog research, wrote in an email. “The advanced evasion techniques used in these malware packages, such as novel exfiltration or even DNS tunneling (the first we’ve seen in packages uploaded to PyPI) signal a disturbing trend that attackers are becoming stealthier in their attacks on open source software.”
The researchers said that PyPI quickly removed all malicious packages once JFrog reported them.
> Use of open source repositories to push malware dates back to at least 2016, when a college student uploaded malicious packages to PyPI, RubyGems, and npm. He gave the packages names that were similar to widely used packages already submitted by other users.
> Over a span of several months, his imposter code was executed more than 45,000 times on more than 17,000 separate domains, and more than half the time, his code was given all-powerful administrative rights. Two of the affected domains ended in .mil, an indication that people inside the US military may have run his script.
In July, JFrog found malicious PyPI packages, downloaded more than 30,000 times, that carried out a range of nefarious activities, including stealing credit card data and injecting malicious code on infected machines.
Earlier this year, a researcher developed a new type of supply chain attack that can have serious consequences. The so-called “dependency confusion attacks” work by uploading malicious packages to public code repositories and giving them names that are identical to legitimate packages stored in the internal repository of Microsoft, Apple, or another large software developer. Developers’ software-management apps often favor external code libraries over internal ones, so they download and use the malicious package rather than the trusted one.
From attacker to victim via Fastly
Now, these types of attacks are getting harder to detect.
> The biggest advance in subterfuge the researchers found was in two packages, one called “importantpackage” (or alternatively “important-package”) and the other called “10Cent10” (or “10Cent11”). The packages use the Fastly CDN to disguise communications between the infected machine and a control server.
The malicious code hiding in the packages causes an HTTPS request to be sent to pypi.python.org in a way that’s indistinguishable from a legitimate request to PyPI. The requests eventually are rerouted by Fastly as an HTTP request to the control server psec.forward.io.global.prod.fastly.net. The server then sends replies through the same setup, allowing for two-way communication. Fastly makes it easy for people to register their domains with the service. In many cases, registration can even be done anonymously.
JFrog researchers Andrey Polkovnychenko and Menashe explained:
The PyPI infrastructure is hosted on the Fastly CDN. This hosting uses the Varnish transparent HTTP proxy to cache the communication between clients and the backend. The traffic first goes into a TLS terminator for decryption, so the Varnish proxy can inspect the contents of the HTTP packet. The proxy analyzes the HTTP headers from the user’s request and redirects the request to the corresponding backend according to the
Hostheader. The process then repeats itself in the reverse direction, allowing the malware to imitate duplex communication with PyPI.As a result, the command-and-control (C2) session is encrypted and signed with a legitimate server certificate, making it indistinguishable from communicating with legitimate PyPI resources.
DNS tunneling, the other advanced evasion technique the researchers found, works using a DNS channel—normally reserved for mapping domain names to IP addresses—to send communications between an infected computer and a control server. DNS tunneling isn’t new, but the researchers said it’s the first time they have seen the technique used in malware uploaded to PyPI.
The growing sophistication of the malicious code being sneaked into PyPI, and presumably other repositories, is an indication that its use in spreading malware is likely to continue. Developers who rely on public repositories should take extra care to ensure there are no typos or stray letters in the package name they’re downloading
-
Flash News: Ukraine Intercepts Russian Kh-59 Cruise Missile Using US VAMPIRE Air Defense System Mounted on Boat. Ukrainian forces have made ...