Intro: Well in hindsight, at least we know now months after the fact. . .the malware initializes by performing several data decoding steps and eventually establishes a session to Google Drive, using hard-coded OAuth2 credentials.

"Researchers have discovered a previously unknown macOS malware variant called GIMMICK, which is believed to be a custom tool used by a Chinese espionage threat actor known as 'Storm Cloud.'
> The malware was discovered by researchers at Volexity, who retrieved it from the RAM of a MacBook Pro running macOS 11.6 (Big Sur), which was compromised in a late 2021 cyberespionage campaign.
The exposure of custom malware used by sophisticated threat actors isn't common. Those groups operate very carefully, leaving a minimal trace and wiping remnants of the malware to keep their tools secret and evade IoC-based detection.
However, sometimes even the most advanced cybercriminals slip up and leave behind malware that can then be dissected by security researchers, as is the case with GIMMICK.
Dissecting the GIMMICK malware
GIMMICK is a multi-platform malware written in Objective C (macOS), or .NET and Delphi (Windows).
All variants use the same C2 architecture, file paths, behavioral patterns, and heavily abuse Google Drive services, so it's tracked as one tool despite the code differences.
GIMMICK is launched either directly by the user or as a daemon on the system and installs itself as a binary file named 'PLIST,' usually mimicking a heavily used application on the target machine.
Next, the malware initializes by performing several data decoding steps and eventually establishes a session to Google Drive, using hard-coded OAuth2 credentials.
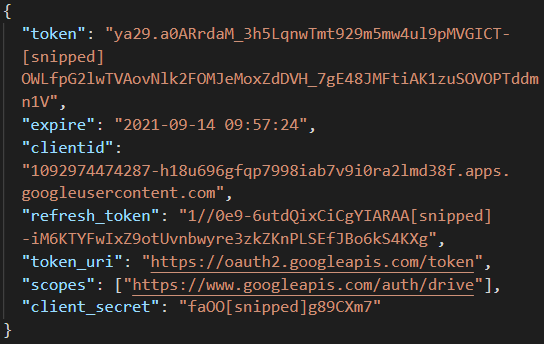
(Volexity)
After initialization, GIMMICK loads three malware components, namely DriveManager, FileManager, and GCDTimerManager, with the first being responsible for the below actions:
- Manage the Google Drive and proxy sessions.
- Maintain a local map of the Google Drive directory hierarchy in memory.
- Manage locks for synchronizing tasks on the Google Drive session.
- Handle download and upload tasks to and from the Google Drive session.
Each infected system’s hardware UUID is used as an identifier for the Google Drive directory that corresponds to it.
FileManager manages the local directory where C2 information and command tasks are stored, and the GCDTimerManager undertakes the management of the various GCD objects.
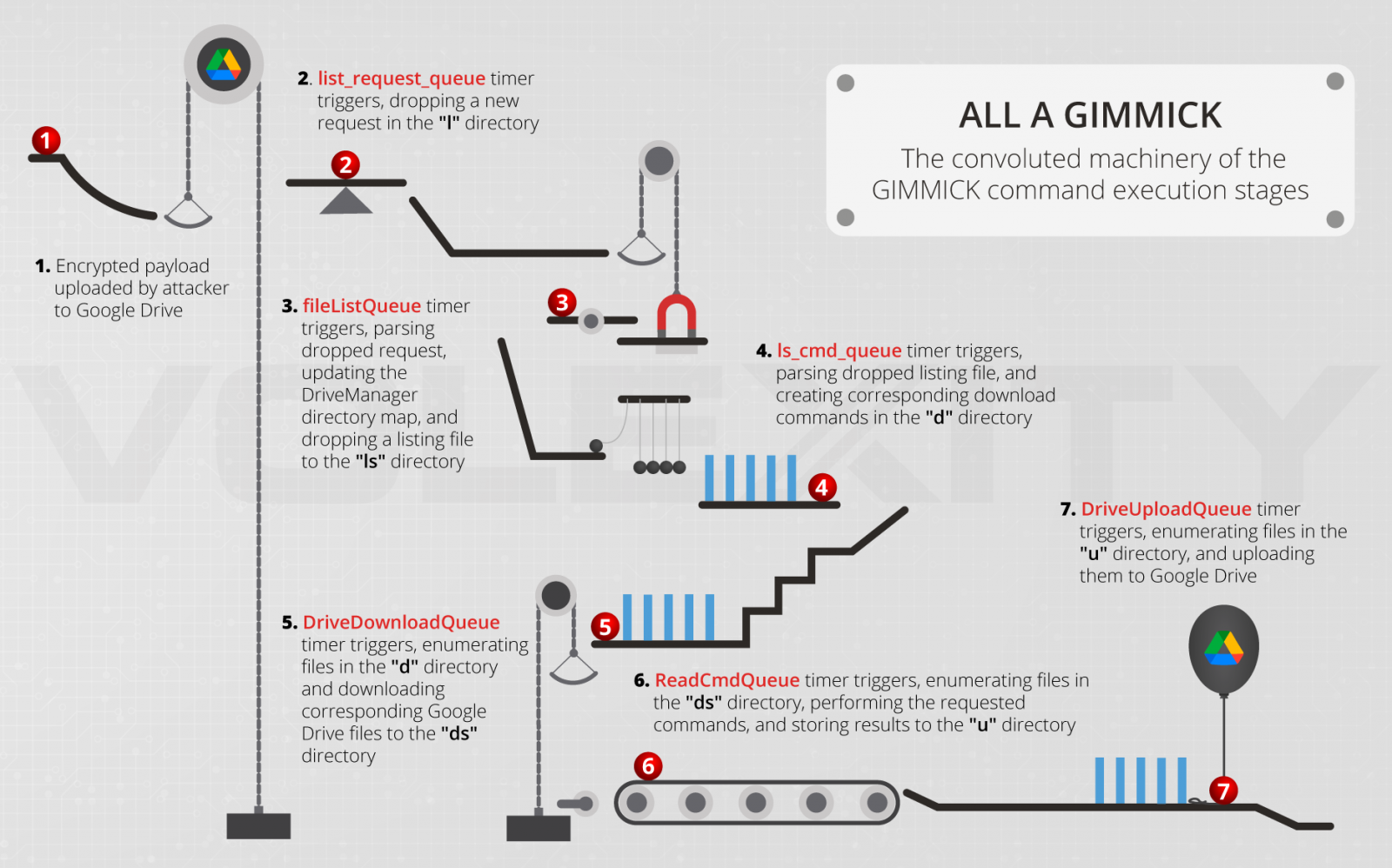
The commands supported by GIMMICK, which arrive on the system in AES-encrypted form, are the following:
- Transmit base system information
- Upload file to C2
- Download file to client
- Execute a shell command and write output to C2
- Set client Google Drive timer interval
- Set client timer interval for client info heartbeat message
- Overwrite client work period information
“Due to the asynchronous nature of the malware operation, command execution requires a staged approach. Though the individual steps occur asynchronously, every command follows the same.” explains Volexity in its technical report
It is this asynchronous design that makes GIMMICK so robust and at the same time complex, so porting it on a new platform, macOS in this case, is a feat that underscores Storm Cloud’s skills and resources.
Volexity notes that the possibility of Storm Cloud buying the malware from a third-party developer and using it exclusively shouldn't be ruled out.
Protect against GIMMICK
Apple has also rolled out new protections to all supported macOS versions with new signatures for XProtect and MRT, which should be able to block and remove the malware since March 17, 2022. To ensure you have received these signatures, follow Apple's support page instructions.
READ MORE DETAILS Go Here >> https://www.bleepingcomputer.com/news/security/custom-macos-malware-of-chinese-hackers-storm-cloud-exposed/
Related Articles:
Hackers exploit new WPS Office flaw to breach betting firms
Google: Chinese state hackers target Ukraine’s government
Microsoft: Ukraine hit with FoxBlade malware hours before invasion
Chinese cyberspies target govts with their ‘most advanced’ backdoor
FritzFrog botnet grows 10x, hits healthcare, edu, and govt systems
/cdn.vox-cdn.com/uploads/chorus_image/image/70661994/Screen_Shot_2022_03_23_at_8.38.33_AM.0.png)
:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/23339657/apple_id.jpg)



