Like other ransomware operations, Akira will breach a corporate network and spread laterally to other devices. Once the threat actors gain Windows domain admin credentials, they will deploy the ransomware throughout the network.
Meet Akira — A new ransomware operation targeting the enterprise
- May 7, 2023
- 09:16 AM
- 0

The new Akira ransomware operation has slowly been building a list of victims as they breach corporate networks worldwide, encrypt files, and then demand million-dollar ransoms.
Launched in March 2023, Akira claims to have already conducted attacks on sixteen companies. These companies are in various industries, including education, finance, real estate, manufacturing, and consulting.
While another ransomware named Akira was released in 2017, it is not believed that these operations are related.
The Akira encryptor
A sample of the Akira ransomware was discovered by MalwareHunterTeam, who shared a sample with BleepingComputer so we could analyze it.
When executed, Akira will delete Windows Shadow Volume Copies on the device by running the following PowerShell command:
powershell.exe -Command "Get-WmiObject Win32_Shadowcopy | Remove-WmiObject"
The ransomware will then proceed to encrypt files that contain the following file extensions:
.accdb, .accde, .accdc, .accdt, .accdr, .adb, .accft, .adf, .ade, .arc, .adp, .alf, .ora, .btr, .ask, .cat, .bdf, .ckp, .cdb, .cpd, .cma, .dad, .dacpac, .daschema, .dadiagrams, .db-shm, .db-wal, .dbf, .dbc, .dbt, .dbs, .dbx, .dbv, .dct, .dcb, .ddl, .dcx, .dlis, .dsk, .dqy, .dtsx, .dsn, .eco, .dxl, .edb, .ecx, .exb, .epim, .fdb, .fcd, .fmp, .fic, .fmpsl, .fmp12, .fol, .fpt, .gdb, .frm, .gwi, .grdb, .his, .hdb, .idb, .itdb, .ihx, .jet, .itw, .kdb, .jtx, .kexic, .kexi, .lgc, .kexis, .maf, .lwx, .mar, .maq, .mav, .mas, .mdf, .mdb, .mrg, .mpd, .mwb, .mud, .ndf, .myd, .nrmlib, .nnt, .nsf, .nyf, .nwdb, .oqy, .odb, .owc, .orx, .pdb, .pan, .pnz, .pdm, .qvd, .qry, .rctd, .rbf, .rodx, .rod, .rsd, .rpd, .sbf, .sas7bdat, .sdb, .scx, .sdf, .sdc, .spq, .sis, .sqlite, .sql, .sqlitedb, .sqlite3, .temx, .tps, .tmd, .trm, .trc, .udl, .udb, .usr, .vpd, .vis, .wdb, .vvv, .wrk, .wmdb, .xld, .xdb, .abcddb, .xmlff, .abx, .abs, .adn, .accdw, .icg, .hjt, .kdb, .icr, .maw, .lut, .mdt, .mdn, .vhd, .vdi, .pvm, .vmdk, .vmsn, .vmem, .nvram, .vmsd, .raw, .vmx, .subvol, .qcow2, .vsv, .bin, .vmrs, .avhd, .avdx, .vhdx, .iso, .vmcxWhile encrypting, the encryptor will skip files found in the Recycle Bin, System Volume Information, Boot, ProgramData, and Windows folders. It will also avoid encrypting the Windows system files with .exe, .lnk, .dll, .msi, and .sys file extensions.
When encrypting files, the ransomware encrypts files and appends the .akira extension will be appended to the file's name.
For example, a file named 1.doc would be encrypted and renamed to 1.doc.akira, as shown in the encrypted folder below.
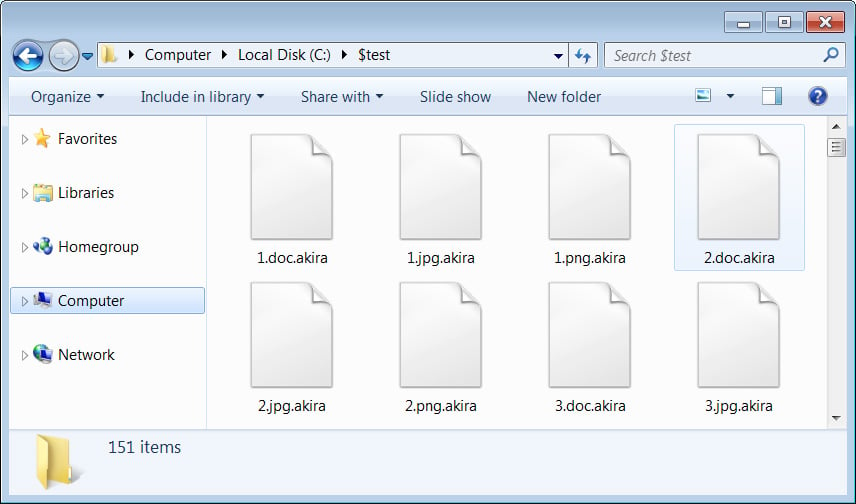
Source: BleepingComputer
> Akira also uses the Windows Restart Manager API to close processes or shut down Windows services that may be keeping a file open and preventing encryption.
Each computer folder will contain a ransom note named akira_readme.txt that includes information on what happened to a victim's files and links to the Akira data leak site and negotiation site.
"As for your data, if we fail to agree, we will try to sell personal information/trade secrets/databases/source codes - generally speaking, everything that has a value on the darkmarket - to multiple threat actors at ones. Then all of this will be published in our blog," threatens the Akira ransom note.
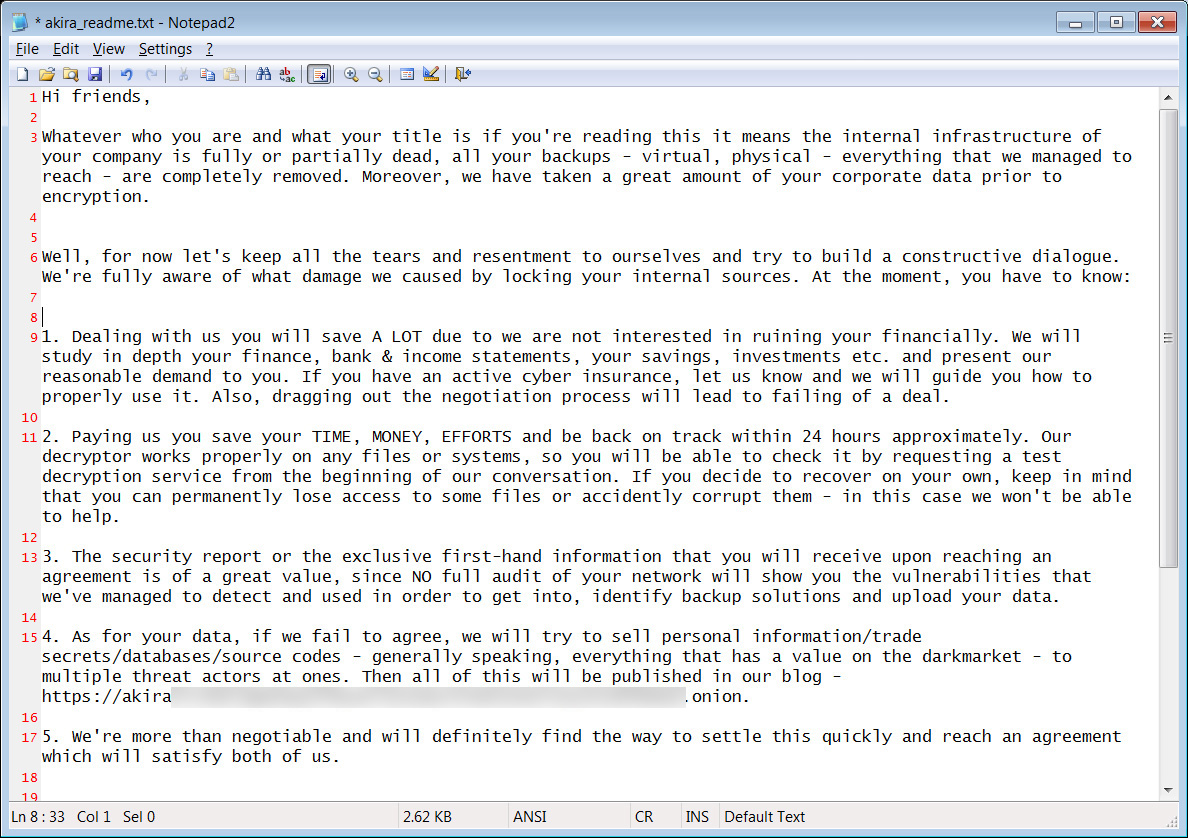
Source: BleepingComputer
Each victim has a unique negotiation password that is entered into the threat actor's Tor site. Unlike many other ransomware operations, this negotiation site just includes a chat system that the victim can use to negotiate with the ransomware gang.
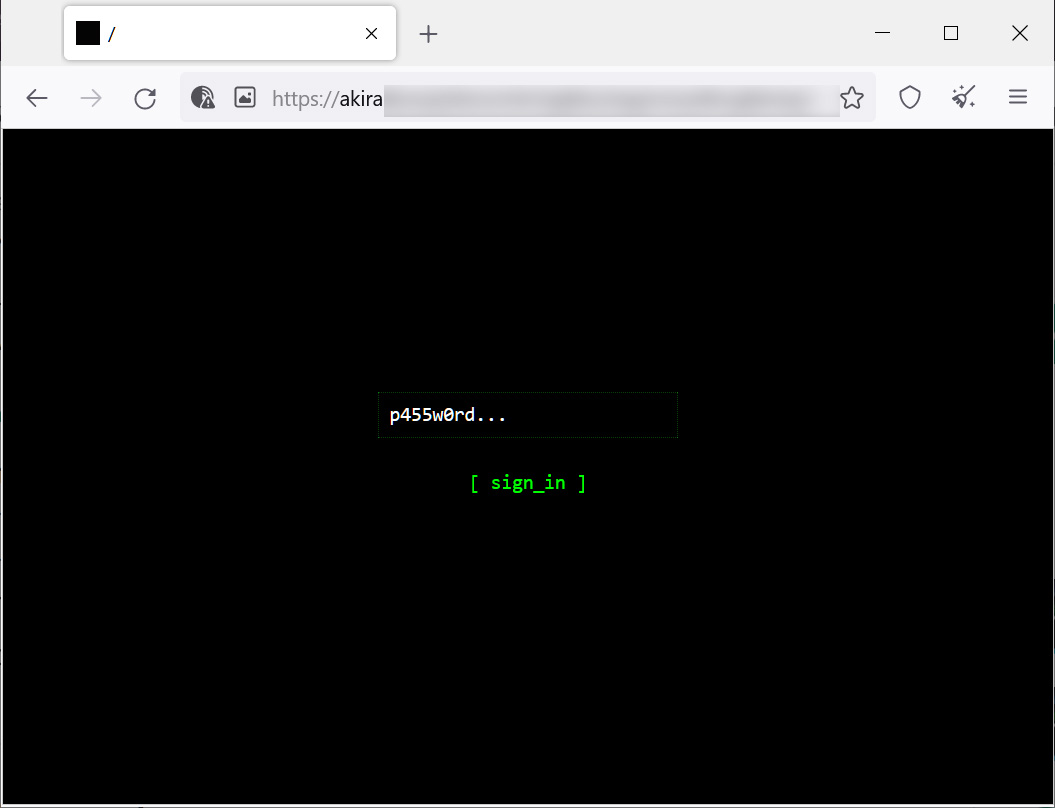
Source: BleepingComputer
Data leak site used to extort victims
Like other ransomware operations, Akira will breach a corporate network and spread laterally to other devices. Once the threat actors gain Windows domain admin credentials, they will deploy the ransomware throughout the network.
However, before encrypting files, the threat actors will steal corporate data for leverage in their extortion attempts, warning victims that it will be publicly released if a ransom is not paid.
The Akira gang put a lot of effort into their data leak site, giving it a retro look where visitors can navigate it by typing in commands, as shown below.
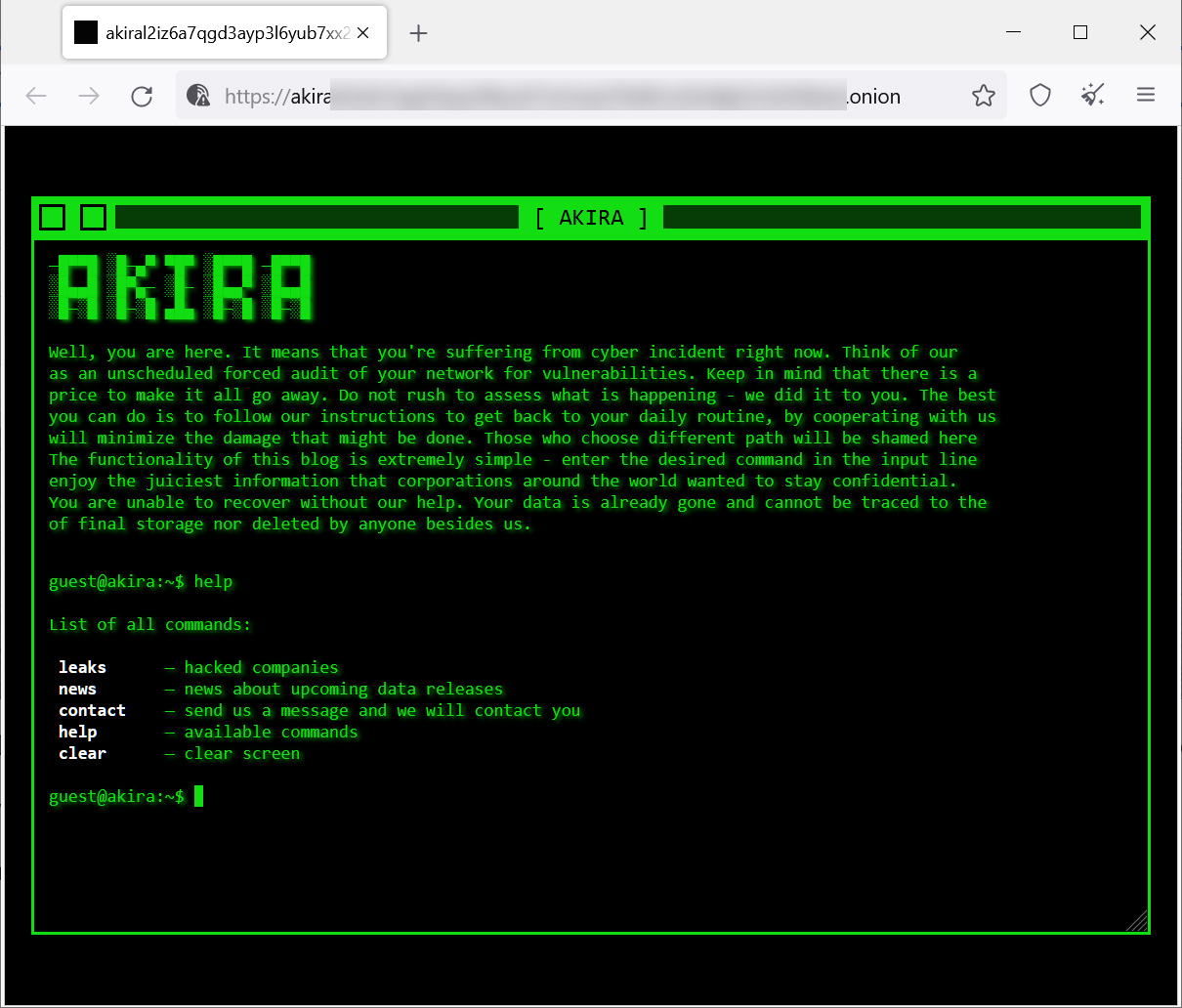
Source: BleepingComputer
At the time of this writing, Akira has leaked the data for four victims on their data leak site, with the size of the leaked data ranging from 5.9 GB for one company to 259 GB for another.
From negotiations seen by BleepingComputer, the ransomware gang demands ransoms ranging from a $200,000 to millions of dollars.
They are also willing to lower ransom demands for companies who do not need a decryptor, and just want to prevent the leaking of stolen data.
The ransomware is currently being analyzed for weaknesses, and BleepingComputer does not advise victims to pay the ransom until its determined if a free decryptor can recover files for free.
As first reported by PC Gamer, a custom CS:GO map named 'de_voyna' resembles the ruins of a Slavic city featuring a secret underground bunker that players can visit to access information about the war in Ukraine.
New CS:GO map bypasses Russia's censorship of Ukraine war news
Bill Toulas
- May 7, 2023
- 10:16 AM
- 0
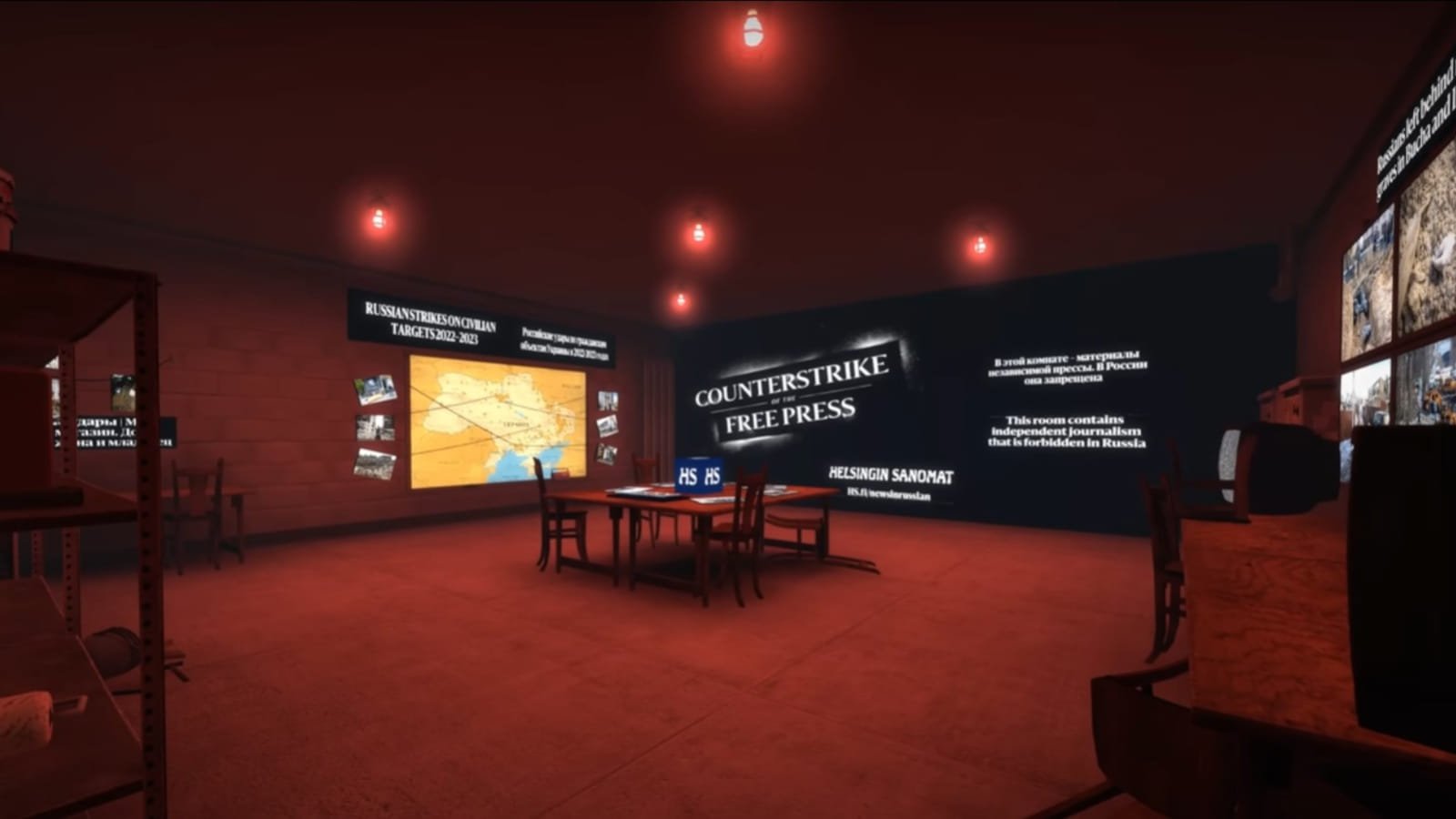
Finish newspaper Helsinin Sanomat has created a custom
As first reported by PC Gamer, a custom CS:GO map named 'de_voyna' resembles the ruins of a Slavic city featuring a secret underground bunker that players can visit to access information about the war in Ukraine.explicitly made to bypass Russian news censorship and smuggle information about the war in Ukraine to Russian players.
Starting in March 2022, following its invasion of Ukraine, Russia began blocking international news outlets to implement tighter controls over what news reaches the Russian audience regarding the ongoing war.
CS:GO is one of the most popular first-person shooter games in the world, being the most played game on Steam. CS:GO is particularly enjoyed by Russian players, who reportedly constitute roughly one-tenth of the title's total player base.
It has also escaped the Russian censorship machine so far, allowing users from the country to log in to CS:GO servers and enjoy their matches without limitation.
As first reported by PC Gamer, a custom CS:GO map named 'de_voyna' resembles the ruins of a Slavic city featuring a secret underground bunker that players can visit to access information about the war in Ukraine.
"On the surface, it seems like a normal Slavic city. However, there might be something hidden underneath," reads the description of the game map.
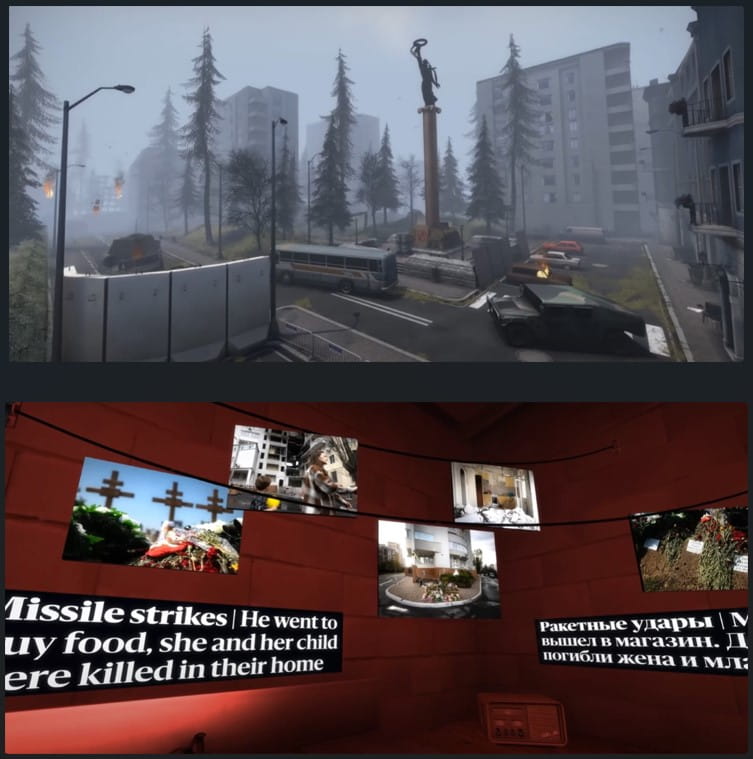
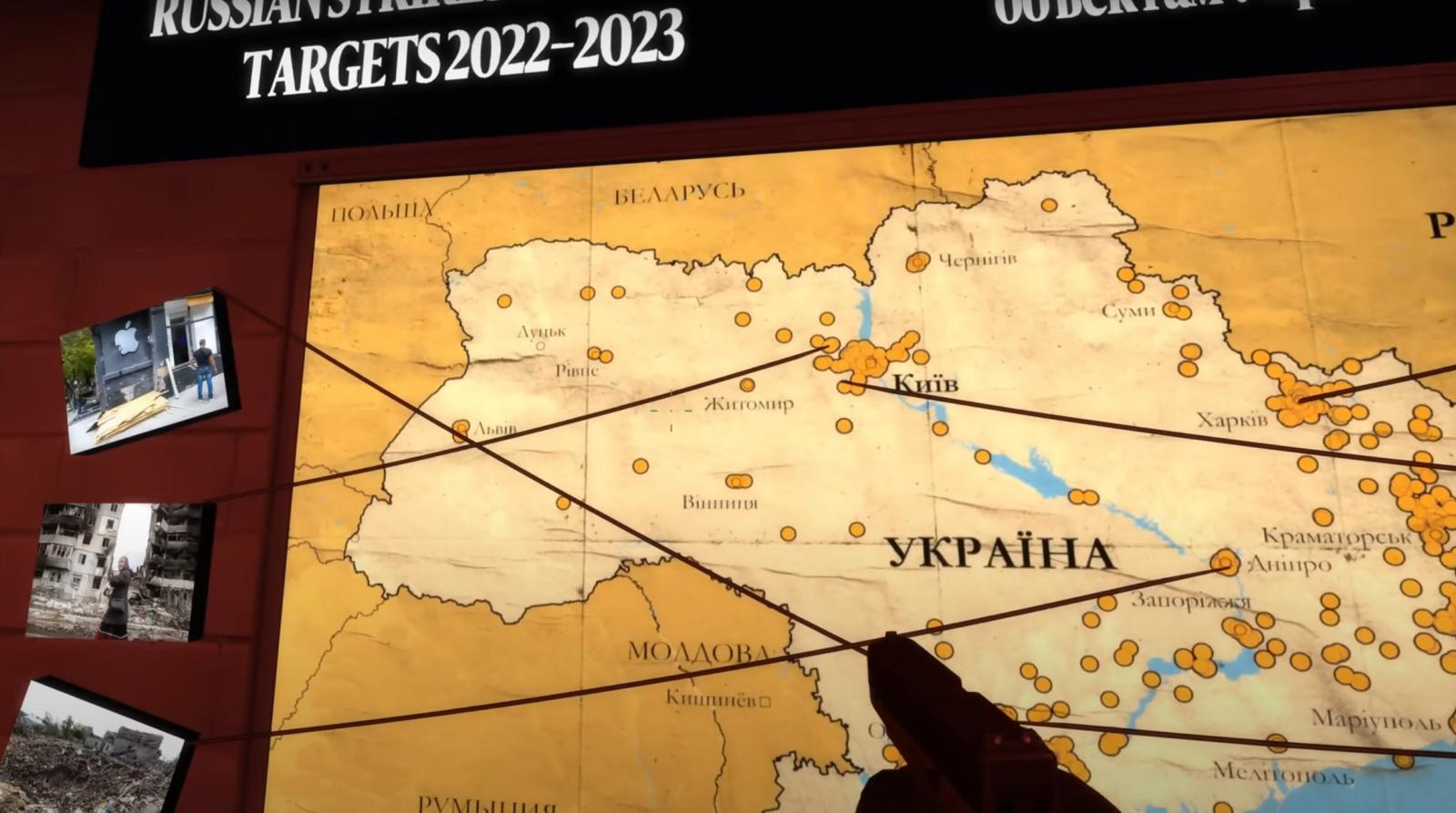
The underground room features a selection of key data about the war in both English and Russian.
This information includes Russian army death stats from reliable sources, details about missile strikes and other atrocities committed on civilians, images, and location of incidents.
"The purpose is to make Russians see that the terrors of war are happening in places that look very familiar to them," explains the newspaper on a dedicated page about the launch of the special CS:GO map.
The bunker is also accessible and made more apparent when the player dies on the 'de_voyna' map, as the secret room is highlighted during "fly view" mode and is hard to miss for those who don't know about its existence.
The map was released on May 3, 2023, coinciding with World Press Freedom Day, and it has just started gaining traction, with over 10,000 subscribers. But, unfortunately, the more popular it becomes, the higher the likelihood that Russian authorities will ban CS:GO.
Those interested in downloading 'de_voyna' on their CS:GO installation may do so either via the "Workshop Maps" section in-game or the Steam desktop or web application.
Helsinin Sanomat urges players from Western countries to play the map and try to get Russian players also to play it, which fulfills the primary purpose of its existence.
Last year, a similar project that aimed to "smuggle" information about the war in Ukraine to Russians used movie and game torrents to do it.
Named "Torrents of Truth," the initiative planted videos and text in pirated content archives that shared information on how to use VPNs to maintain anonymity from Russian ISPs and a list of reliable news sources.


