Watch: Paramount Cuts 1,600 More Jobs as Part of Plan to Save $3 Billion
Bloomberg Opinion
Listen, Watch and Catch Up
Most Active US Stocks
Bloomberg Film
Watch: Can't Look Away: The Case Against Social Media

Your News

Watch: Paramount Cuts 1,600 More Jobs as Part of Plan to Save $3 Billion





Watch: Can't Look Away: The Case Against Social Media

Choose up to 12 topics to see the latest stories on your homepage.
Recommended
Regions
Sectors













CISA ordered U.S. federal agencies today to patch a critical Samsung vulnerability that has been exploited in zero-day attacks to deploy LandFall spyware on devices running WhatsApp.
Tracked as CVE-2025-21042, this out-of-bounds write security flaw was discovered in Samsung's libimagecodec.quram.so library, allowing remote attackers to gain code execution on devices running Android 13 and later.
While Samsung patched it in April following a report from Meta and WhatsApp Security Teams, Palo Alto Networks' Unit 42 revealed last week that attackers had been exploiting it since at least July 2024 to deploy previously unknown LandFall spyware via malicious DNG images sent over WhatsApp.
Data from VirusTotal samples examined by Unit 42 researchers shows potential targets in Iraq, Iran, Turkey, and Morocco, while C2 domain infrastructure and registration patterns share similarities with those seen in Stealth Falcon operations, which originated from the United Arab Emirates.
Another clue is the use of the "Bridge Head" name for the malware loader component, a naming convention commonly seen in commercial spyware developed by NSO Group, Variston, Cytrox, and Quadream.
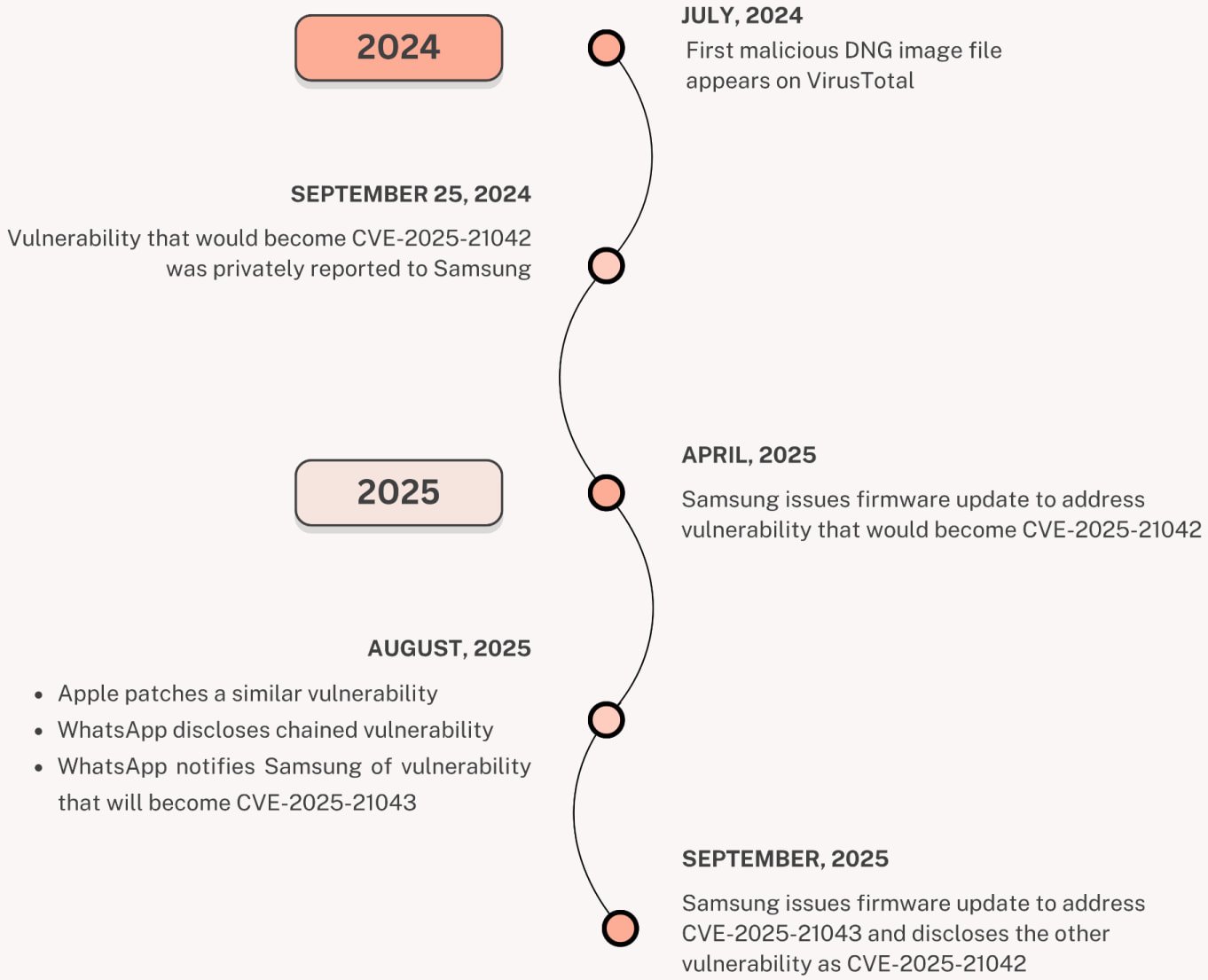

Samsung patches actively exploited zero-day reported by WhatsApp
New LandFall spyware exploited Samsung zero-day via WhatsApp messages
CISA confirms hackers exploited Oracle E-Business Suite SSRF flaw
CISA orders agencies to patch Cisco flaws exploited in zero-day attacks
CISA warns of critical CentOS Web Panel bug exploited in attacks
