Vulnerabilities in billions of Wi-Fi devices let hackers bypass firewalls
FragAttacks let hackers inject malicious code or commands into encrypted Wi-Fi traffic.
"One of the things that makes Wi-Fi work is its ability to break big chunks of data into smaller chunks and combine smaller chunks into bigger chunks, depending on the needs of the network at any given moment. These mundane network plumbing features, it turns out, have been harboring vulnerabilities that can be exploited to send users to malicious websites or exploit or tamper with network-connected devices, newly published research shows.
In all, researcher Mathy Vanhoef found a dozen vulnerabilities, either in the Wi-Fi specification or in the way the specification has been implemented in huge numbers of devices. Vanhoef has dubbed the vulnerabilities FragAttacks, short for fragmentation and aggregation attacks, because they all involve frame fragmentation or frame aggregation. Broadly speaking, they allow people within radio range to inject frames of their choice into networks protected by WPA-based encryption.
Bad news
Assessing the impact of the vulnerabilities isn’t straightforward. FragAttacks allow data to be injected into Wi-Fi traffic, but they don’t make it possible to exfiltrate anything out. That means FragAttacks can’t be used to read passwords or other sensitive information the way a previous Wi-Fi attack of Vanhoef, called Krack, did. But it turns out that the vulnerabilities—some that have been part of Wi-Fi since its release in 1997—can be exploited to inflict other kinds of damage, particularly if paired with other types of hacks.
“It's never good to have someone able to drop packets into your network or target your devices on the network,” Mike Kershaw, a Wi-Fi security expert and developer of the open source Kismet wireless sniffer and IDS, wrote in an email. “In some regards, these are no worse than using an unencrypted access point at a coffee shop—someone can do the same to you there, trivially—but because they can happen on networks you'd otherwise think are secure and might have configured as a trusted network, it's certainly bad news.”
>>Rogue DNS injection
One of the most severe vulnerabilities in the FragAttacks suite resides in the Wi-Fi specification itself. Tracked as CVE-2020-24588, the flaw can be exploited in a way that forces Wi-Fi devices to use a rogue DNS server, which in turn can deliver users to malicious websites rather than the ones they intended. From there, hackers can read and modify any unencrypted traffic. Rogue DNS servers also allow hackers to perform DNS rebinding attacks, in which malicious websites manipulate a browser to attack other devices connected to the same network.
The rogue DNS server is introduced when an attacker injects an ICMPv6 Router Advertisement into Wi-Fi traffic. Routers typically issue these announcements so other devices on the network can locate them. The injected advertisement instructs all devices to use a DNS specified by the attacker for lookups of both IPv6 and IPv4 addresses.
An exploit demoed in a video Vanhoef published shows the attacker luring the target to a website that stashes the router advertisement in an image.
Here's a visual overview:
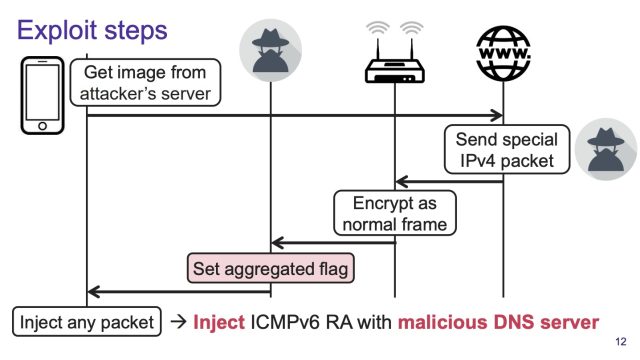
In an email, Vanhoef explained, saying, “The IPv6 router advertisement is put in the payload (i.e. data portion) of the TCP packet. This data is by default passed on to the application that created the TCP connection. In the demo, that would be the browser, which is expecting an image. This means that by default, the client won't process the IPv6 router advertisement but instead process the TCP payload as application data.”
Vanhoef said that it’s possible to perform the attack without user interaction when the target’s access point is vulnerable to CVE-2021-26139, one of the 12 vulnerabilities that make up the FragAttacks package. The security flaw stems from a kernel flaw in NetBSD 7.1 that causes Wi-Fi access points to forward Extensible Authentication Protocol (AP) over LAN frames to other devices even when the sender has not yet authenticated to the AP.
It’s safe to skip ahead, but for those curious about the specific software bug and the reason the video demo uses a malicious image, Vanhoef explained:
More ..............................................................................................................................................


No comments:
Post a Comment