Colonial Pipeline cyberattack shuts down pipeline that supplies 45% of East Coast's fuel
The attack highlights how ransomware and other cyberattacks are increasingly a threat to real-world infrastructure
-----------------------------------------------------------------------------------------------------------------------------
More > 3 hours ago
Cyberattack Forces a Shutdown of a Top U.S. Pipeline Operator
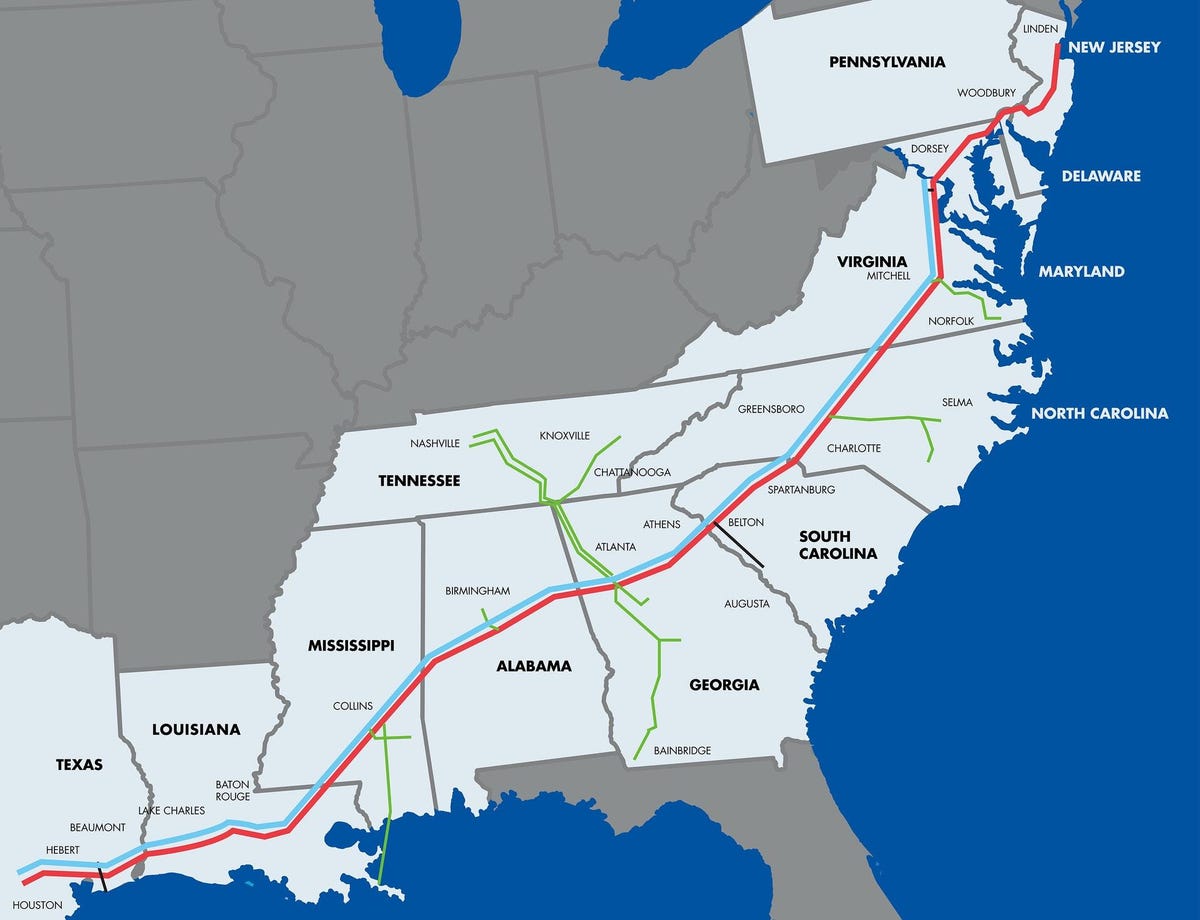
The operator of the system, Colonial Pipeline, said it had shut down its 5,500 miles of pipeline, which takes refined gasoline and jet fuel along the East Coast.
A cyberattack forced the shutdown of one of the largest pipelines in the United States, in what appeared to be a significant attempt to disrupt vulnerable energy infrastructure. The pipeline carries refined gasoline and jet fuel up the East Coast from Texas to New York.
The operator of the system, Colonial Pipeline, said in a statement late Friday that it had shut down its 5,500 miles of pipeline, which it says carries 45 percent of the East Coast’s fuel supplies, in an effort to contain the breach on its computer networks. . .It said it had contacted law enforcement and other federal agencies. The F.B.I. leads such investigations, but critical infrastructure is the responsibility of the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency.
> The breach comes just months after two major attacks on American computer networks — the SolarWinds intrusion by Russia’s main intelligence service, and another against a Microsoft email service that has been attributed to Chinese hackers — that have illustrated the vulnerability of the networks on which the government and corporations rely.
While both of those attacks appeared aimed, at least initially, on the theft of emails and other data, the nature of the intrusions created “back doors” that experts say could ultimately enable attacks on physical infrastructure. So far, neither effort is thought to have led to anything other than data theft.
-------------------------------------------------------------------------------------------------------------------------------
More
cyber attack
temporarily ...


No comments:
Post a Comment