CISA: GPS software bug may cause unexpected behavior this Sunday

"The Network Time Protocol (NTP) has been critical in ensuring time is accurately kept for various systems businesses and organizations rely on. Authentication mechanisms such as Time-based One-Time Password (TOTP) and Kerberos also rely heavily on time. As such, should there be a severe mismatch in time, users would not be able to authenticate and gain access to systems." - SANS ISC
The bug is set to trigger this Sunday, on October 24th, and the implications are somewhat unpredictable as it could cause systems to become unresponsive or unavailable.
On October 24, 2021, all Network Time Protocol (NTP) servers using GPSD versions 3.20 through 3.22 are going to jump back 1024 weeks in time, to March 3, 2002.
The vulnerable versions were released between December 31, 2019, and January 8, 2021, so the affected GPS devices constitute a significant portion of those deployed out there at the moment.
The problem could be severe, but it’s somewhat of a Y2K bug, so nobody can be sure about whether or not the devices will actually encounter functional or service reliability issues.
CISA urges the affected owners and operators to update to GPSD version 3.23, released on August 8, 2021, or newer, to avoid all chances of facing problems.
CURRENT ACTIVIY: On October 24, 2021, Network Time Protocol servers using bugged GPSD versions 3.20-3.22 may rollback the date 1,024 weeks—to March 2002—which may cause systems and services to become unavailable or unresponsive. Learn more: https://t.co/hlpdQviDJm pic.twitter.com/rlZMu1QGoj
— Cybersecurity and Infrastructure Security Agency (@CISAgov) October 22, 2021
Groove ransomware calls on all extortion gangs to attack US interests
Over the weekend, BleepingComputer reported that the REvil ransomware operation shut down again after an unknown third party hijacked their dark web domains.
As part of this shutdown, a known REvil operator claimed that the unknown party was "looking" for them by modifying configuration files, so that the threat actor would be tricked into going to a site operated by the unknown entity. . .Yesterday, Reuters reported that REvil's takedown resulted from an international law enforcement operation that included support from the FBI.
The blog post also warns ransomware operations not to target Chinese companies, as the gangs would need to use the country as a safe haven if Russia takes a stronger stance on cybercrime operating inside its country.
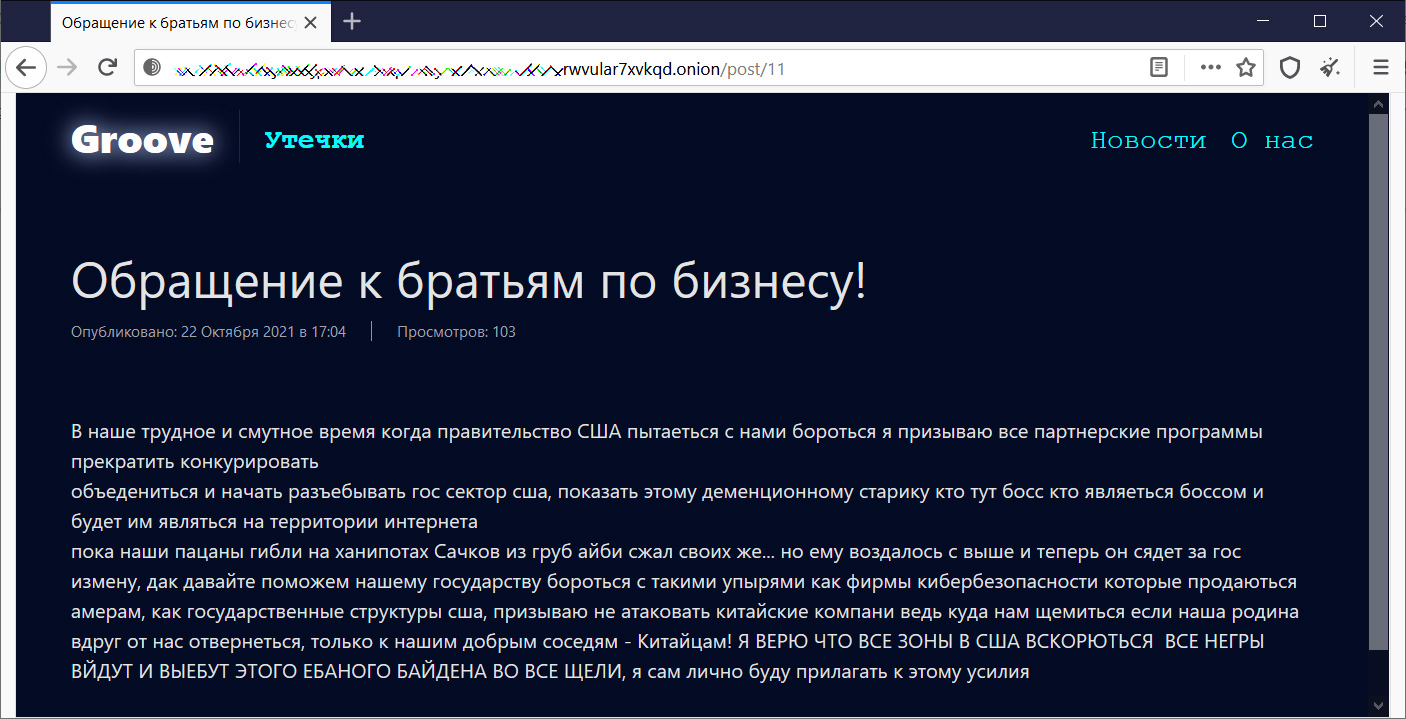
The whole translated message, with some censoring of inappropriate words, can be read below.
"In our difficult and troubled time when the US government is trying to fight us, I call on all partner programs to stop competing,
unite and start xxcking up the US public sector, show this old man who is the boss here who is the boss and will be on the Internet
while our boys were dying on honeypots, the nets from rude aibi squeezed their own... but he was rewarded with higher and now he will go to jail for treason, so let's help our state fight against such ghouls as cybersecurity firms that are sold to amers, like US government agencies, I urge not to attack Chinese companies, because where do we pinch if our homeland suddenly turns away from us, only to our good neighbors - the Chinese! I BELIEVE THAT ALL ZONES IN THE USA WILL BE OPENED, ALL xxOES WILL COME OUT AND xxCK THIS xxCKING BIDEN IN ALL THE CRACKS, I myself will personally make efforts to do this" - Groove ransomware.
The calling of attacks on US interests correlates with other information shared with BleepingComputer this week by a threat intelligence researcher for a Dutch bank.
In July 2021, a threat actor known as 'Orange' launched the RAMP hacking forum after shutting down and splitting from the original Babuk Ransomware operation.
As Orange still controlled Babuk's Tor site, he used it to launch the hacking forum where he acted as an admin. Orange is also believed to be one of the representatives of the Groove ransomware operation.
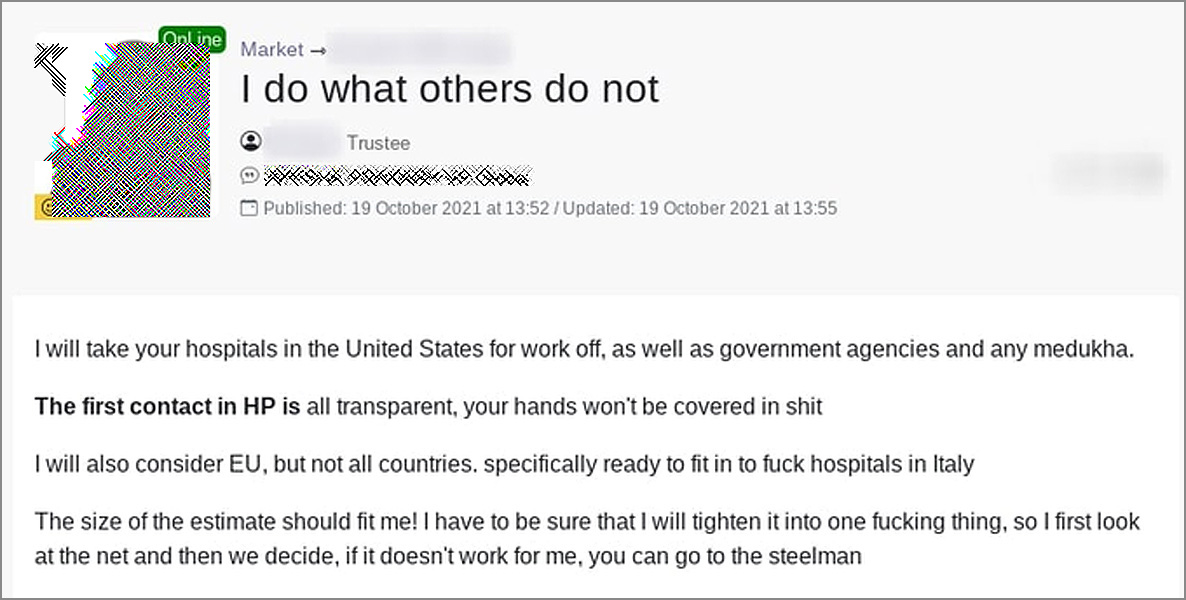
Recently, Orange stepped down as the forum's admin to pursue a new operation but did not provide any further information on what was being planned. . .
However, a later post indicates that the threat actor is likely starting a new ransomware operation as he began actively pursuing the purchase of network access to US hospitals and government agencies, as shown in the forum post below.
READ MORE:
Groove ransomware calls on all extortion gangs to attack US interests
-
Popular NPM library hijacked to install password-stealers, miners
Hackers hijacked the popular UA-Parser-JS NPM library, with millions of downloads a week, to infect Linux and Windows devices with cryptominers and password-stealing trojans in a supply-chain attack.
- October 23, 2021
- 12:51 PM
 0
0
-
Hacker sells the data for millions of Moscow drivers for $800
Hackers are selling a stolen database containing 50 million records of Moscow driver data on an underground forum for only $800.
- October 23, 2021
- 11:12 AM
 0
0
-
FTC: ISPs collect and monetize far more user data than you’d think
The Federal Trade Commission (FTC) found that six largest internet service providers (ISPs) in the U.S. collect and share customers' personal data without providing them with info on how it's used or meaningful ways to control this process.
- October 23, 2021
- 10:00 AM
 0
0
-
This bundle helps you prepare for 12 CompTIA certifications
The 2021 Complete CompTIA Certification Prep Super Bundle helps you pass all the most valuable exams, with 16 courses providing full prep. The training is worth $4,400, but you can get it today for only $69.
- October 23, 2021
- 08:36 AM
 0
0
-
The Week in Ransomware - October 22nd 2021 - Striking back
Between law enforcement operations, REvil's second shut down, and ransomware gangs' response to the hacking of their servers, it has been quite the week.
- October 22, 2021
- 05:47 PM
 0
0
-
SCUF Gaming store hacked to steal credit card info of 32,000 customers
SCUF Gaming International, a leading manufacturer of custom PC and console controllers, is notifying customers that its website was hacked in February to plant a malicious script used to steal their credit card information.
- October 22, 2021
- 02:26 PM
 0
0
-
DarkSide ransomware rushes to cash out $7 million in Bitcoin
Almost $7 million worth of Bitcoin in a wallet controlled by DarkSide ransomware operators has been moved in what looks like a money laundering rollercoaster.
- October 22, 2021
- 02:02 PM
 0
0
-
Groove ransomware calls on all extortion gangs to attack US interests
The Groove ransomware gang is calling on other extortion groups to attack US interests after law enforcement took down REvil's infrastructure last week.
- October 22, 2021
- 11:48 AM
 4
4
-
Microsoft: WizardUpdate Mac malware adds new evasion tactics
Microsoft says it found new variants of macOS malware known as WizardUpdate (also tracked as UpdateAgent or Vigram), updated to use new evasion and persistence tactics.
- October 22, 2021
- 11:14 AM
 0
0
-
Google cuts Play Store dev fees to 15% for all subscriptions
Google announced that they are dropping the 30% flat service fee for in-app purchases or app sales to 15% starting January 1, 2022.
- October 22, 2021
- 10:36 AM
 0
0
-
Italian celebs' data exposed in ransomware attack on SIAE
The Italian data protection authority Garante per la Protezione dei Dati Personali (GPDP) has announced an investigation into a data breach of the country's copyright protection agency.
- October 22, 2021
- 10:06 AM
 0
0
-
Microsoft Teams adds end-to-end encryption for one-to-one calls
Microsoft has announced the public preview roll-out of end-to-end encryption (E2EE) support for one-to-one Microsoft Teams calls.
- October 22, 2021
- 09:29 AM
 0
0
-
CISA: GPS software bug may cause unexpected behavior this Sunday
The Cybersecurity and Infrastructure Security Agency (CISA) warned that GPS deices might experience issues over the weekend because of a timing bug impacting Network Time Protocol (NTP) servers running the GPS Daemon (GPSD) software.
- October 22, 2021
- 08:37 AM
 0
0
-
Microsoft: Windows 11 printing issues fixed in the KB5006746 update
Microsoft has fixed multiple known issues impacting printing on Windows 11 with the release of the optional KB5006746 cumulative update preview on Thursday.
- October 22, 2021
- 07:56 AM
 1
1
-
This bundle helps you master data analysis in only 9 hours
The Complete 2022 Big Data Analysis Bundle provides the ultimate crash course, with nine hours of beginner-friendly video tutorials. The training is worth $944 in total, but you can get it today for only $75.
- October 22, 2021
- 07:12 AM
 0
0
-
Massive campaign uses YouTube to push password-stealing malware
Widespread malware campaigns are creating YouTube videos to distribute password-stealing trojans to unsuspecting viewers.
- October 21, 2021
- 05:10 PM
 0
0
-
Evil Corp demands $40 million in new Macaw ransomware attacks
Evil Corp has launched a new ransomware called Macaw Locker to evade US sanctions that prevent victims from making ransom payments.
- October 21, 2021
- 03:07 PM
 0
0


















No comments:
Post a Comment