‘Heist of the century’: US bitcoin case tests ability to crack down on cybercrime
Case may be first time government has brought a case not on the basis of an alleged theft, but on the couple’s alleged efforts to conceal their identities

". . .According to the government’s Statement of Facts, the stolen bitcoin was “layered” and “chain-hopped” through a series of virtual wallets to the “darknet market AlphaBay” and then back, and finally on to accounts where it was converted into fiat currency, gift cards and precious metals and withdrawn as cash from bitcoin ATMs.
What may be more fascinating is that the couple at the center of what US prosecutors have described as the largest financial seizure in the history of the Department of Justice were able to utilize so little of the stolen cryptocurrency.
Authorities said more than 80% of the stolen currency remained untouched in accounts associated with the couple and money-laundering allegations against them identify only small sums, including the purchase of a $500 Walmart gift card and gift cards for Uber, Hotels.com and PlayStation. [...]
It may also test the bounds of believability as more and more colorful – and downright bizarre – details emerge of the couple at the heart of the saga which seems to lie at an unlikely nexus between the cryptocurrency, rap, self-help advice and New York eccentricity.
The couple targeted in the sting, Ilya “Dutch” Lichtenstein and Heather Morgan, a self-described “badass money maker”, were charged with conspiracy to commit money laundering and conspiracy to defraud the United States. They are currently on $5m and $3m bail, respectively, but held in custody after a judge in Washington granted an emergency request by the government to keep them detained. . ."
RELATED CONTENT
Dirty laundry —
$3.6 billion bitcoin seizure shows how hard it is to launder cryptocurrency
A “laundry list” of technical measures to cover wrongdoers' tracks didn’t work.

"On Tuesday, Ilya Lichtenstein and Heather Morgan were arrested in New York and accused of laundering a record $4.5 billion worth of stolen cryptocurrency. In the 24 hours immediately afterward, the cybersecurity world ruthlessly mocked their operational security screwups: Lichtenstein allegedly stored many of the private keys controlling those funds in a cloud-storage wallet that made them easy to seize, and Morgan flaunted her “self-made” wealth in a series of cringe-inducing rap videos on YouTube and Forbes columns.
But those gaffes have obscured the remarkable number of multi-layered technical measures that prosecutors say the couple did use to try to dead-end the trail for anyone following their money. Even more remarkable, perhaps, is that federal agents, led by IRS Criminal Investigations, managed to defeat those alleged attempts at financial anonymity on the way to recouping $3.6 billion of stolen cryptocurrency. In doing so, they demonstrated just how advanced cryptocurrency tracing has become—potentially even for coins once believed to be practically untraceable.

“What was amazing about this case is the laundry list of obfuscation techniques [Lichtenstein and Morgan allegedly] used,” says Ari Redbord, the head of legal and government affairs for TRM Labs, a cryptocurrency tracing and forensics firm. Redbord points to the couple's alleged use of "chain-hopping"—transferring funds from one cryptocurrency to another to make them more difficult to follow—including exchanging bitcoins for "privacy coins" like monero and dash, both designed to foil blockchain analysis. Court documents say the couple also allegedly moved their money through the Alphabay dark web market—the biggest of its kind at the time—in an attempt to stymie detectives.
Yet investigators seem to have found paths through all of those obstacles. "It just shows that law enforcement is not going to give up on these cases, and they’ll investigate funds for four or five years until they can follow them to a destination they can get information on," Redbord says.
GET MORE CURIOUS Hmmm...In July 2017, however—six months after the IRS says Lichtenstein moved a portion of the Bitfinex coins into AlphaBay wallets—the FBI, DEA, and Thai police arrested AlphaBay's administrator and seized its server in a data center in Lithuania. That server seizure isn't mentioned in the IRS's statement of facts
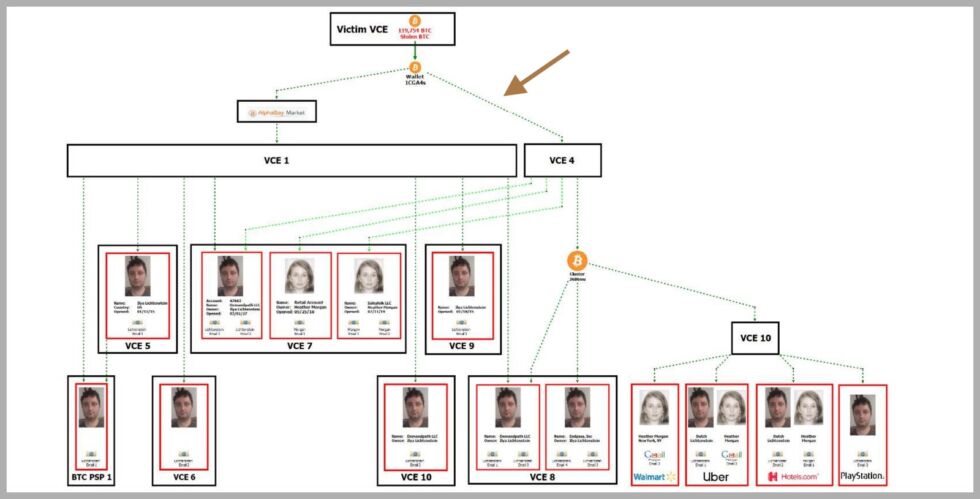
"In a 20-page "statement of facts" published alongside the Justice Department's criminal complaint against Lichtenstein and Morgan on Tuesday, IRS-CI detailed the winding and tangled routes the couple allegedly took to launder a portion of the nearly 120,000 bitcoins stolen from the cryptocurrency exchange Bitfinex in 2016. Most of those coins were moved from Bitfinex's addresses on the Bitcoin blockchain to a wallet the IRS labeled 1CGa4s, allegedly controlled by Lichtenstein. Federal investigators eventually found keys for that wallet in one of Lichtenstein's cloud storage accounts, along with logins for numerous cryptocurrency exchanges he had used.
But to get to the point of identifying Lichstenstein—along with his wife, Morgan—and locating that cloud account, IRS-CI followed two branching paths taken by 25,000 bitcoins that moved from the 1CGa4s wallet across Bitcoin's blockchain. One of those branches went into a collection of wallets hosted on AlphaBay's dark web market, designed to be impenetrable to law enforcement investigators. The other appears to have been converted into monero, a cryptocurrency designed to obfuscate the trails of funds within its blockchain by mixing up the payments of multiple monero users—both real transactions and artificially generated ones—and concealing their value. Yet somehow, the IRS says it identified Lichtenstein and Morgan by tracing both those branches of funds to a collection of cryptocurrency exchange accounts in their names, as well as in the names of three companies they owned, known as Demandpath, Endpass, and Salesfolk.
The IRS hasn't entirely spelled out how its investigators defeated those two distinct obfuscation techniques. But clues in the court document—and analysis of the case by other blockchain analysis experts—suggest some likely theories. . .
>
The IRS's explanation doesn't mention at what point the money in Lichtenstein's bitcoin wallet was converted into the monero that later appeared in those two exchange accounts. Nor, more importantly, does it say how investigators continued to follow the cryptocurrency despite Monero's features designed to thwart that tracing—a feat of crypto-tracing that has never before been documented in a criminal case.
It's possible that the IRS investigators didn't actually trace monero to draw that link, points out Matt Green, a cryptographer at Johns Hopkins University and one of the cocreators of the privacy-focused cryptocurrency zcash. They may have found other evidence of the connection in one of the defendant's records, just as they found other incriminating files in Lichtenstein's cloud storage account, though no such evidence is mentioned in the IRS's statement of facts. . .IRS Criminal Investigations declined to comment on the Bitfinex case beyond the public documents it has released, and Chainalysis declined to say whether it had been part of the investigation—much less whether it had helped the IRS to trace monero. . ."
========================================================================


No comments:
Post a Comment