Chinese hackers breach US critical infrastructure in stealthy attacks
- May 24, 2023
- 04:43 PM
- 0

'Microsoft says a Chinese cyberespionage group it tracks as Volt Typhoon has been targeting critical infrastructure organizations across the United States, including Guam, since at least mid-2021.
Their victims span a wide range of critical sectors, including government, maritime, communications, manufacturing, information technology, utilities, transportation, construction, and education.
"Microsoft assesses with moderate confidence that this Volt Typhoon campaign is pursuing development of capabilities that could disrupt critical communications infrastructure between the United States and Asia region during future crises," the Microsoft Threat Intelligence team said.
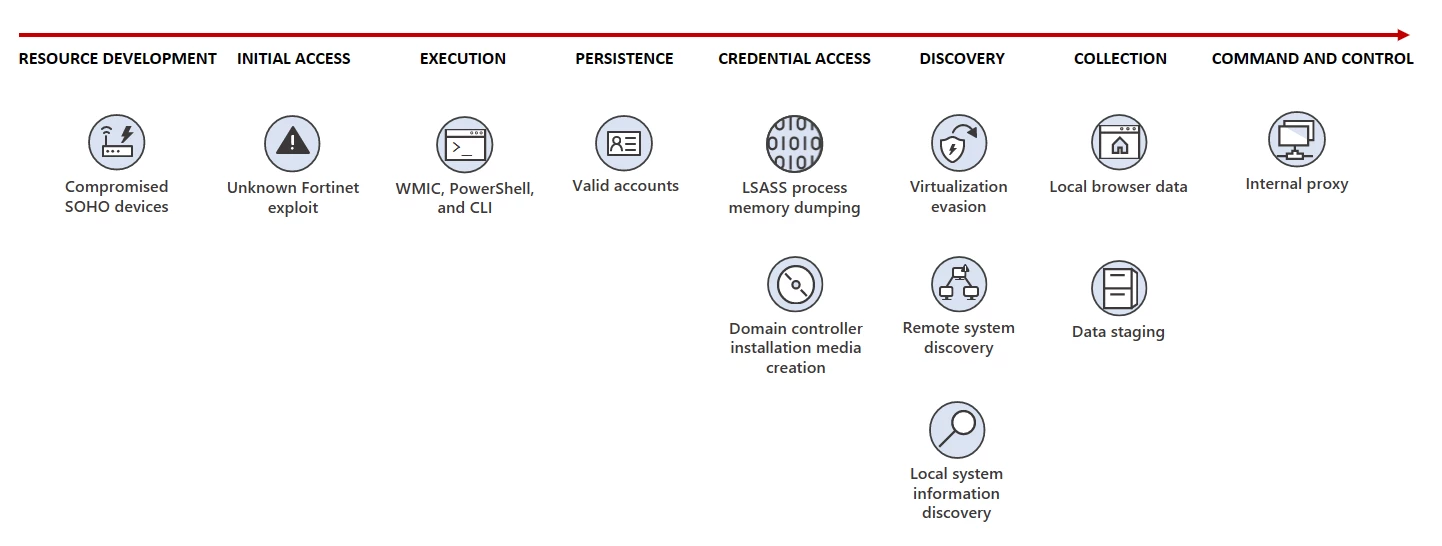
- The initial attack vector is the compromise of Internet-exposed Fortinet FortiGuard devices by exploiting an unknown zero-day vulnerability.
- After breaching the targets' networks, they launch what Microsoft describes as "living-off-the-land" attacks with hands-on-keyboard activity and living-off-the-land binaries (LOLBins) such as PowerShell, Certutil, Netsh, and the Windows Management Instrumentation Command-line (WMIC).
- However, they were also seen using open-source tools like Fast Reverse Proxy (frp), the Mimikatz credential-stealing tool, and the Impacket networking framework, according to a joint advisory published today by the FBI, NSA, CISA, and cybersecurity agencies from Australia, New Zealand, the United Kingdom, and Canada.
- To ensure that their malicious activity blends with legitimate network traffic to evade detection, Volt Typhoon employs compromised small office and home office (SOHO) network equipment from ASUS, Cisco, D-Link, Netgear, FatPipe, and Zyxel, such as routers, firewalls, and VPN appliances.
- Leveraging the privileged access obtained after compromising the Fortinet devices allows the state hackers to dump credentials through the Local Security Authority Subsystem Service (LSASS).
The stolen credentials allow them to deploy Awen-based web shells for data exfiltration and persistence on the hacked systems.
As Mandiant Intelligence Chief Analyst John Hultquist told BleepingComputer, these intrusions into US critical infrastructure orgs are likely part of a concerted effort to provide China with access in the event of a future conflict between the two countries.
"There are a variety of reasons actors target critical infrastructure, but a persistent focus on these sectors may indicate preparation for disruptive or destructive cyberattack," Hultquist said.
"States conduct long-term intrusions into critical infrastructure to prepare for possible conflict, because it may simply be too late to gain access when conflict arises. Similar contingency intrusions are regularly conducted by states.
"Over the last decade, Russia has targeted a variety of critical infrastructure sectors in operations that we do not believe were designed for immediate effect. China has done the same in the past, targeting the oil and gas sector. These operations are aggressive and potentially dangerous, but they don't necessarily indicate attacks are looming."
In line with its standard procedures for addressing nation-state actor activity, Microsoft says it proactively reached out to all customers that were either targeted or compromised in these attacks to provide them with the information required to secure their networks from future hacking attempts."
Volt Typhoon targets US critical infrastructure with living-off-the-land techniques
Microsoft has uncovered stealthy and targeted malicious activity focused on post-compromise credential access and network system discovery aimed at critical infrastructure organizations in the United States. The attack is carried out by Volt Typhoon, a state-sponsored actor based in China that typically focuses on espionage and information gathering. Microsoft assesses with moderate confidence that this Volt Typhoon campaign is pursuing development of capabilities that could disrupt critical communications infrastructure between the United States and Asia region during future crises.
Microsoft says critical U.S. infrastructure targeted by Chinese hackers
Microsoft warned on Wednesday that it has uncovered “stealthy and targeted malicious activity” by a state-sponsored actor in China aimed at disrupting “critical infrastructure organizations” in the United States.
The Redmond, Wash.-based tech giant said in a security blog post that the “Volt Typhoon” campaign has been active since mid-2021. Targeted organizations in Guam and elsewhere in the U.S. include communications, manufacturing, utility, transportation, construction, maritime, government, information technology, and education sectors.
Microsoft said Volt Typhoon “could disrupt critical communications infrastructure between the United States and Asia region during future crises.” The company added that behavior it has observed suggests hackers intend to perform espionage and maintain access without being detected for as long as possible.
The New York Times reported that the attack set off alarms because Guam, with its Pacific ports and vast American air base, would be a centerpiece of any American military response to an invasion or blockade of Taiwan. U.S. “tabletop” exercises which map out what a Chinese invasion might look like, envision China moving initially to cut off American communications and slow the ability to respond
The blog post offers extensive details about what the campaign is targeting, how it works and its tactics for achieving and maintaining unauthorized access to target networks. It says the campaign achieves initial access to targeted organizations through an internet-facing cybersecurity suite called Fortinet FortiGuard.
Microsoft recommends that those affected by Volt Typhoon should close or change credentials for all compromised accounts.
Microsoft says China-sponsored hackers targeted infrastructure
US tech giant says attacks targeted communications and other infrastructure in Guam and elsewhere.
Taipei, Taiwan – Microsoft and the “Five Eyes” network of Western intelligence partners have accused Chinese state-sponsored hackers of carrying out attacks against critical infrastructure in the United States.
Volt Typhoon, a Chinese state-sponsored hacking group linked to espionage activities in the past, was behind the attacks, which used techniques that could be used in other countries besides the US, spy and cybersecurity agencies from Australia, Canada, New Zealand, the United Kingdom and the US said on Thursday.
Microsoft said in a separate statement that the campaign had been active since mid-2021 and had targeted the manufacturing, utility, transportation, construction, maritime, government, information technology and education sectors in Guam and elsewhere in the US.
The tech giant said it had “moderate confidence” the attack was intent on disrupting “critical communications infrastructure between the United States and Asia region during future crises”.
Such a crisis would likely include an attack or blockade targeting Taiwan, an island democracy of 23 million people, which is claimed by China and is the focus of much of Beijing’s military activity.
Beijing has pledged to “reunify” with Taiwan by 2049 and has not ruled out the use of force.
The US is treaty-bound to help Taiwan defend itself and its military bases in Guam, a US territory in the western Pacific, and elsewhere in Asia would likely play a key role during any political or military crisis.
In a joint advisory, Western intelligence and cybersecurity agencies outlined ways to identify the cyber-campaign and protect infrastructure from attacks.
“Private sector partners have identified that this activity affects networks across US critical infrastructure sectors and the authoring agencies believe the actor could apply the same techniques against these and other sectors worldwide,” the statement said.
Microsoft said the Volt Typhoon campaign relies on “living off the land” attacks – or file-less malware that uses a target’s existing programs to carry out attacks rather than installing files itself – and “hands-on-keyboard” activity. The tech giant said Volt Typhoon blends in with normal network activity by routing data through office and home networking equipment like routers, firewalls and VPNs, making the activity extremely difficult to detect.'
A Chinese state-sponsored group has hacked into critical American infrastructure, including in the U.S. territory of Guam, Microsoft and the "Five Eyes" intelligence alliance warns.
Why it matters: Guam is home to three American military bases and the western Pacific island would play an important strategic role should the U.S. need to respond to any potential Chinese military attack on or blockade of Taiwan.
- The likely aim of the operation is to "disrupt critical communications infrastructure between the United States and Asia region during future crises," per a blog post Wednesday by Microsoft, which detected the hacking.
Driving the news: The U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued a joint advisory with its "Five Eyes" partner agencies in the U.K., Canada, Australia and New Zealand warning that the "Volt Typhoon" hackers posed a threat to all five allied countries following a "recently discovered cluster of activity."
- Microsoft said in its blog post that the "state-sponsored actor based in China ... typically focuses on espionage and information gathering."
- Detecting "and mitigating this attack could be challenging," Microsoft said.
State of play: "Volt Typhoon has been active since mid-2021 and has targeted critical infrastructure organizations in Guam and elsewhere in the United States," per Microsoft.
- "In this campaign, the affected organizations span the communications, manufacturing,
- utility, transportation, construction, maritime, government, information technology, and education sectors. Observed behavior suggests that the threat actor intends to perform espionage and maintain access without being detected for as long as possible."
- The Australian Signals Directorate’s Australian Cyber Security Centre noted that a key strategy of Volty Typhoon, known as "living off the land," used "built-in network administration tools to perform their objectives," allowing the group "to evade detection by blending in with normal Windows system and network activities."
Mitigation and protection guidance
Mitigating risk from adversaries like Volt Typhoon that rely on valid accounts and living-off-the-land binaries (LOLBins) is particularly challenging. Detecting activity that uses normal sign-in channels and system binaries requires behavioral monitoring. Remediation requires closing or changing credentials for compromised accounts.
What to do now if you’re affected
- Close or change credentials for all compromised accounts. Depending on the level of collection activity, many accounts may be affected. Identify LSASS dumping and domain controller installation media creation to identify affected accounts.
- Examine the activity of compromised accounts for any malicious actions or exposed data.
Defending against this campaign
- Mitigate the risk of compromised valid accounts by enforcing strong multi-factor authentication (MFA) policies using hardware security keys or Microsoft Authenticator. Passwordless sign-in, password expiration rules, and deactivating unused accounts can also help mitigate risk from this access
- method.
- Reduce the attack surface. Microsoft customers can turn on the following attack surface reduction rules to block or audit some observed activity associated with this threat:
- Block credential stealing from the Windows local security authority subsystem (lsass.exe).Block process creations originating from PSExec and WMI commands. Some organizations may experience compatibility issues with this rule on certain server systems but should deploy it to other systems to prevent lateral movement originating from PsExec and WMI.
- Block execution of potentially obfuscated scripts.
- Harden the LSASS process by enabling Protective Process Light (PPL) for LSASS on Windows 11 devices. New, enterprise-joined Windows 11 (22H2 update) installs have this feature enabled by default. In addition, enable Windows Defender Credential Guard, which is also turned on by default for organizations using the Enterprise edition of Windows 11.
- Turn on cloud-delivered protection in Microsoft Defender Antivirus to cover rapidly evolving attacker tools, techniques, and behaviors such as those exhibited by Volt Typhoon.
- Run endpoint detection and response (EDR) in block mode so that Microsoft Defender for Endpoint can block malicious artifacts, even when your non-Microsoft antivirus does not detect the threat, or when Microsoft Defender Antivirus is running in passive mode. EDR in block mode works behind the scenes to remediate malicious artifacts that are detected post-compromise.




No comments:
Post a Comment