Monday, April 05, 2021
REMOTE / In-Person-Or-Not WFH > Mesa City Council Study Session Mon 04.05.2021
The official description from the city's webpage:
"Each year, the city's budget is developed in conjunction with residents, the Mayor and City Council, City Manager and City Employees. The result is a budget that closely matches the community's highest priorities each fiscal year."
| File #: | 21-0352 |
| Type: | Presentation | Status: | Agenda Ready |
| In control: | City Council Study Session |
| On agenda: | 4/5/2021 |
| Title: | Hear a presentation, discuss, and provide direction on the Police Department budget. |
| Attachments: | 1. Presentation |
- It forecasts city-wide revenues, expenditures and fund balances
- It conducts special projects
- It administers the City's performance excellence, which provides process improvement, performance management and strategic planning services to city organizations.
____________________________________________________________________
PRESENTATIONS AND REPORTS: Go here >
https://www.mesaaz.gov/city-hall/office-of-management-budget/presentations-reports
| File #: | 21-0352 |
| Type: | Presentation | Status: | Agenda Ready |
| In control: | City Council Study Session |
| On agenda: | 4/5/2021 |
| Title: | Hear a presentation, discuss, and provide direction on the Police Department budget. |
| Attachments: | 1. Presentation |
Office of Management & Budget
What is the City’s budget process?
Anyone see where citizens are involved)
Delve into the City’s 12 step budget cycle, see how the budget is managed, and understand budget limitations and requirements
(Might be nice if this was updated from last year 2017, but then again they've been busy)
_________________________________________________________________________
Sunday, April 04, 2021
FED FORESIGHT FAILURE: "Advanced Persistent Threats" > Cybersecurity and Infrastructure Security
Feds say hackers are likely exploiting critical Fortinet VPN vulnerabilities
Exploits allow hackers to log into VPNs and then access other network resources.
 APT actors may use these vulnerabilities or other common exploitation techniques to gain initial access to multiple government, commercial, and technology services,” the agencies said Friday in a joint advisory. “Gaining initial access pre-positions the APT actors to conduct future attacks.” APT is short for advanced persistent threat, a term used to describe well-organized and well-funded hacking groups, many backed by nation states.
APT actors may use these vulnerabilities or other common exploitation techniques to gain initial access to multiple government, commercial, and technology services,” the agencies said Friday in a joint advisory. “Gaining initial access pre-positions the APT actors to conduct future attacks.” APT is short for advanced persistent threat, a term used to describe well-organized and well-funded hacking groups, many backed by nation states.CISA, FBI warn of hacking threat against Fortinet product
- By Justin Katz
- Apr 02, 2021

The Cybersecurity and Infrastructure Security Agency and the FBI on Friday issued a new advisory warning that an advanced persistent threat actor is using old vulnerabilities in enterprise software from Fortinet to gain access to government and industry networks.
"The APT actors may be using any or all of these CVEs to gain access to networks across multiple critical infrastructure sectors to gain access to key networks as pre-positioning for follow-on data exfiltration or data encryption attacks," according to the advisory

According to an alert issued Friday by the FBI and CISA, cyberattackers are scanning devices on ports 4443, 8443 and 10443, looking for unpatched Fortinet security implementations. Specifically, APTs are exploiting CVE-2018-13379, CVE-2019-5591 and CVE-2020-12812.
“It is likely that the APT actors are scanning for these vulnerabilities to gain access to multiple government, commercial and technology services networks,” according to the alert. “APT actors have historically exploited critical vulnerabilities to conduct distributed denial-of-service (DDoS) attacks, ransomware attacks, structured query language (SQL) injection attacks, spear-phishing campaigns, website defacements, and disinformation campaigns.”
The bugs are popular with cyberattackers in general, due to Fortinet’s widespread footprint, researchers noted.
“CVE-2018-13379 is a critical vulnerability in the Fortinet FortiOS SSL VPN that has been favored by cybercriminals since exploit details became public in August 2019,” Satnam Narang, staff research engineer at Tenable, said via email. “In fact, Tenable’s 2020 Threat Landscape Retrospective placed it in our Top 5 Vulnerabilities of 2020 because we see threat actors continue to leverage it in the wild, well over a year after it was first disclosed.”
The FBI and CISA didn’t specify which APTs are mounting the recent activity.
Initial Compromise & Recon
Once exploited, the attackers are moving laterally and carrying out reconnaissance on targets, according to officials.
“The APT actors may be using any or all of these CVEs to gain access to networks across multiple critical-infrastructure sectors to gain access to key networks as pre-positioning for follow-on data exfiltration or data encryption attacks,” the warning explained. “APT actors may use other CVEs or common exploitation techniques—such as spear-phishing—to gain access to critical infrastructure networks to pre-position for follow-on attacks.”
The joint cybersecurity advisory from the FBI and CISA follows last year’s flurry of advisories from U.S. agencies about APT groups using unpatched vulnerabilities to target federal agencies and commercial organizations. . .
More >
Hackers Setup Fake Cyber Security Firm To Target Security Researchers
Google’s Threat Analysis Group (TAG), a Google security team specialized in hunting advanced persistent threat (APT) groups, on Wednesday shared that a North Korean government-backed campaign is targeting cybersecurity researchers with malware via social media.
For those unaware, in January 2021, TAG had disclosed a hacking campaign, targeting security researchers working on vulnerability research and development across different organizations. On March 17th, the same actors behind those attacks set up a new website for a fake company called “SecuriElite” as well as associated Twitter and LinkedIn accounts.
The new website claims that it is an “offensive security company located in Turkey that offers pentests, software security assessments and exploits”.
As per the experts, this website has a link to their PGP public key at the bottom of the page like the previous websites set up by the actor. The PGP key hosted on the attacker’s blog acted as the lure for unsuspecting researchers in January attacks to visit the site “where a browser exploit was waiting to be triggered”.
The attacker’s latest batch of social media profiles continues the trend of posing as fellow security researchers interested in exploitation and offensive security. In total, Google has identified eight Twitter accounts and seven LinkedIn profiles.
The threat actors used multiple platforms to communicate with potential targets, including Twitter, LinkedIn, Telegram, Discord, Keybase and email to communicate with the researchers and build trust, only to deploy a Windows backdoor through a trojanized Visual Studio Project.
Following the discovery, Google reported all identified social media profiles to the platforms to allow them to take appropriate action, after which all of them were suspended.
The accounts seemed to be owned by vulnerability researchers and human resources personnel at various security firms including Trend Macro (a fake name inspired by Trend Micro), while some posed as the Chief Executive Officer and employees at the fictitious Turkish company.
Currently, the new attacker website is not serving any malicious content to deliver malware; however, Google has added the website’s URL to Google Safebrowsing as a precaution to prevent accidental visits by the users.
Following TAG’s disclosure in January 2021, security researchers from South Korean cybersecurity firm ENKI successfully identified these actors using an Internet Explorer 0-day. Based on their activity, TAG researchers believe that these actors are dangerous and likely have more 0-days.
“We encourage anyone who discovers a Chrome vulnerability to report that activity through the Chrome Vulnerabilities Rewards Program submission process,” concluded Adam Weidemann from TAG in the blog post.
Saturday, April 03, 2021
HINDSIGHT 2020 IS EVERYTHING: Q1 January-March 2021 Economic Reporter Newsletter
First Quarter 2021
Welcoming 2021 by recognizing the challenges and celebrating the successes of 2020
"As we enter 2021, I want to extend a sincere thank you to our clients, partners, and community members for your grit and dedication to navigate through 2020.
BLOGGER INSERT: The full economic effects of the COVID-19 pandemic cannot be quantified in the GDP estimate for the fourth quarter of 2020 because the impacts are generally embedded in source data and cannot be separately identified.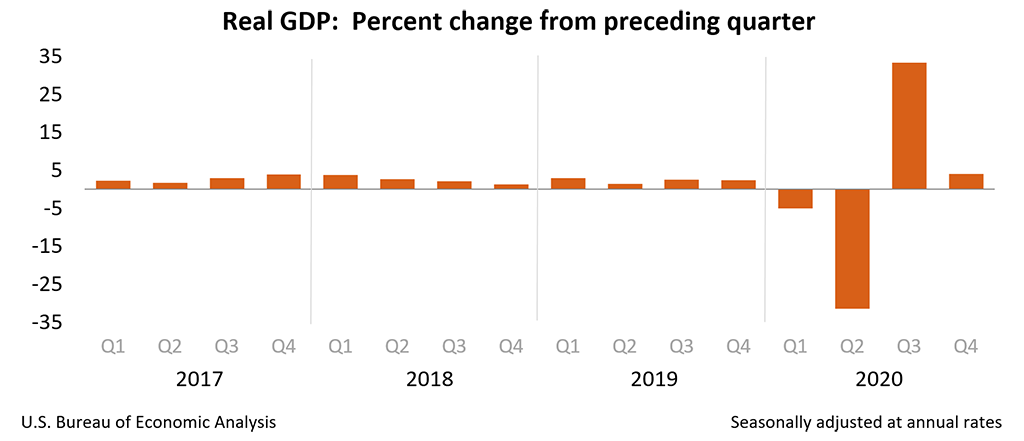
"While it was a challenging year, it was also a rewarding one. Like many organizations, we had to pivot, modify, and adapt. Through the pandemic, I am pleased to note that we maximized technology, developed new ways to stay connected and do business, plus we became stronger and more resilient. Survival has been difficult for many businesses and will continue to be for the next few months. However, I believe it is important to pause and recognize the success and achievements we have realized during the last year.
Mesa's Office of Economic Development works to diversify the economy by attracting and expanding companies that create high-quality jobs and generate capital investment in Mesa. Key project highlights from 2020 had a significant impact on the community and will continue to play a vital part in Mesa's growth.
____________________________________________________________________________
BLOGGER INSERT: The City of Mesa's Economic Development Advisory meets once a month. The Agendas and Approved Minutes are far more informative than what is published in the Reporter Newsletter that is featured here. . .https://www.mesaaz.gov/government/advisory-boards-committees/economic-development-advisory-board
Economic Development Advisory Board Minutes and Agendas | |||||||||||||||||||||||||||||||||||||||||||||||||||
| Search Minutes & Agendas | |||||||||||||||||||||||||||||||||||||||||||||||||||
| Economic Development Advisory Board Home | |||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||
_________________________________________________________________________
Here are a few we would like to celebrate:
> High tech manufacturing expansion is also good for the environment
Commercial Metals Co., known as CMC Steel, manufactures concrete reinforcing bar, rebar, and steel t-posts produced almost entirely from recycled scrap metal. The recycler plans to construct a new facility adjacent to its existing state-of-the-art micro-mill and will provide 185 high-quality jobs within the community.
> Amazon leased the recently built Longbow Gateway One (3115 N Higley Road) speculative industrial building (by The Opus Group) located in Falcon District. The almost 150,000 square foot building is now home to Amazon's Mesa delivery station. Located at the southeast corner of Higley and Longbow Parkway, Amazon will create full-time and part-time jobs and will allow the region's residents to receive their packages faster than ever.
The fully-leased building recently sold to New York-based Lexin Capital for $36 million, further illustrating the strength of the Mesa's industrial sector.
>
Boeing expands in the Falcon District
In October, Boeing started construction of a new one-story fabrication center of approximately 155,000 square located on +/- 21.5 acres of vacant land within the western part of the existing Boeing campus at the northeast corner of Greenfield and McDowell Roads. Building on its 35+ year history in Mesa, the Boeing Company now employs more than 4,500 people and manufactures the Apache Longbow helicopter in Mesa. . .
> Mesa continues to attract medical device manufacturing and operations
Dexcom Inc., a leader in continuous glucose monitoring (CGM) for patients with diabetes, selected the Landing 202 as its home for their additional expansion. The 486,000 square foot facility adds to their existing portfolio that is three times the size of their west Mesa location that started three years ago. . .The Mesa locations employ more than 1,000 employees currently.
> Mesa, AZ Asian District adds international destination retailer
In the first quarter of 2020, the new brand "Mesa, AZ Asian District" launched and shortly after came the announcement of an international retailer.H Mart, an upscale Asian-American supermarket chain, opened its first location in Arizona. The adaptive reuse of the 63,000 square foot former Albertsons at Main and Dobson became H Mart's home. The supermarket chain has more than 40,000 items featuring a wide variety of Asian, Hispanic, American foods and related products.
> Award-winning year for Mesa Office of Economic Development
> For a list of the awards and the categories, click here https://mesanow.org/news/public/article/2676
> Additionally, the City of Mesa's Office of Economic Development was awarded a Golden Prospector Award from the Arizona Association for Economic Development (AAED) in the category of Multimedia Promotion for its work on Mesa's Asian District Brand Launch. The branding initiative was a partnership between community stakeholders and the economic development team to define and promote the Mesa, AZ Asian District as a vibrant, inclusive, day-night community that embraces all cultures attracting businesses, residents, and visitors from across the region.
Along with the accomplishments mentioned above, several other elected officials, partners, and community members contributed to the City of Mesa's success. I look forward to working with our existing and new partners in 2021 to build an even better Mesa.
As always, if you have any questions or comments, please email me at William.jabjiniak@mesaaz.gov
------------------------------------------------------------------------------------------------------------------------------
Falcon Field Airport (FFZ) welcomes new FBO and private jet terminal
In December, Falcon Field Airport welcomed Avflight Corporation’s private jet terminal and fixed based operator (FBO). The new FBO at Falcon Field Airport is Avflight's 23rd location in the United States.
“The addition of Avflight Mesa provides a strong presence for the Avflight Network in a thriving southwestern U.S. market,” said Garrett Hain, Avflight’s vice president of finance. “This strategic acquisition will connect Avflight’s loyal customer base to major businesses, entertainment, and tourism in the greater Phoenix region. We are proud to bring Avflight’s expertise and passion for aviation to FFZ to serve as a premier gateway to this vibrant community.”
With an eye toward expansion, Avflight ultimately plans to move its operation to a new FBO facility across the field in May. The development, already under construction, includes a 5,000 square foot office and 11,000 square foot hangar with the potential for a total of 60,000 square feet of hangar space to accommodate a growing customer base at the Mesa airport.
The new state-of-the-art FBO facility will have a modern aesthetic typical of the Avflight brand and include pilot and passenger lounges, snooze rooms, showers, a kitchen, flight planning room, and conference room. The new FBO facility will allow for direct access from road to ramp with ample parking space for added convenience.
Conveniently located within the Phoenix Metropolitan Area, Avflight Mesa is approximately 30 minutes to Scottsdale and Phoenix, and about 20 minutes to Tempe and downtown Mesa. The FBO also provides the closest fly-in option for the Chicago Cubs’ training facility—Sloan Park—and area attractions and major corporations.
(article: https://www.aviationpros.com)
Visit Mesa launches new
Fresh Foodie Trail GeoTour
Visit Mesa launched the new Fresh Foodie Trail GeoTour with Geocaching HQ, offering up a fun, family-friendly socially distant activity in the destination. The new GeoTour is aimed at promoting the East Valley agritourism attractions that are popular experiences this time of year. The new tour will lead geocachers to the farm stops on the award-winning Fresh Foodie Trail and lucky treasure hunters can collect a series of limited-edition stickers along the way. Guests that find all 10 geocaches will earn a digital souvenir through Geocaching.com . . .
Visit Mesa releases new
2021 Mesa Life Visitors Guide
2021 Mesa Life visitors guide made possible with support from the City of Mesa. The guide will be actively distributed throughout the year at Phoenix-Mesa Gateway Airport and Phoenix Sky Harbor International Airport, Falcon Field, and Mesa hotels, area attractions. The complimentary travel planning guide is also available online for download and mail order. . .Suggested itineraries, an updated 2021 Events Calendar, and a complete business directory to Visit Mesa partners are also included in the 64-page resource. For more information and to order a copy, head to www.VisitMesa.com.
------------------------------------------------------------------------------------------------------------------------------
RELATED CONTENT The crisis that university towns face is just one facet of a looming economic catastrophe for America’s cities: Over the next three years, U.S. municipalities could suffer a $360 billion loss, the National League of Cities estimates
. The Recession Is About to Slam Cities. Not Just the Blue-State Ones.
BEA News: Gross Domestic Product by State and Personal Income by State, 3rd Quarter 2025
BEA News: Gross Domestic Product by State and Personal Income by S...

-
Flash News: Ukraine Intercepts Russian Kh-59 Cruise Missile Using US VAMPIRE Air Defense System Mounted on Boat. Ukrainian forces have made ...