Thursday, August 05, 2021
From The National Security Agency and CyberSecurity & Infrastructure Agency : Recommendations for strengthening the security of an organization’s Kubernetes system.
Insert copy from Bleeping Computer >
NSA and CISA share Kubernetes security recommendations

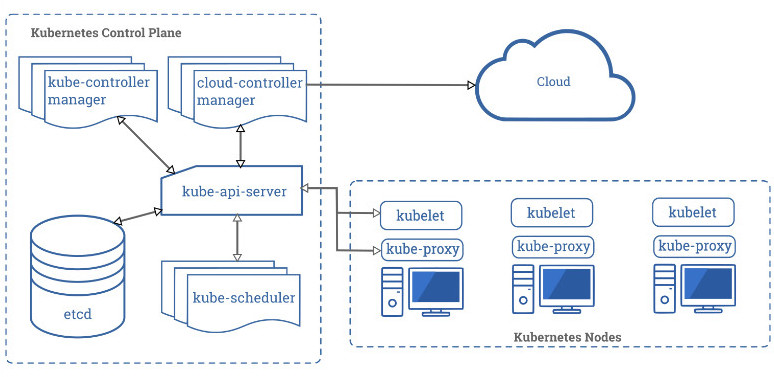
The National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) have published comprehensive recommendations for strengthening the security of an organization’s Kubernetes system.
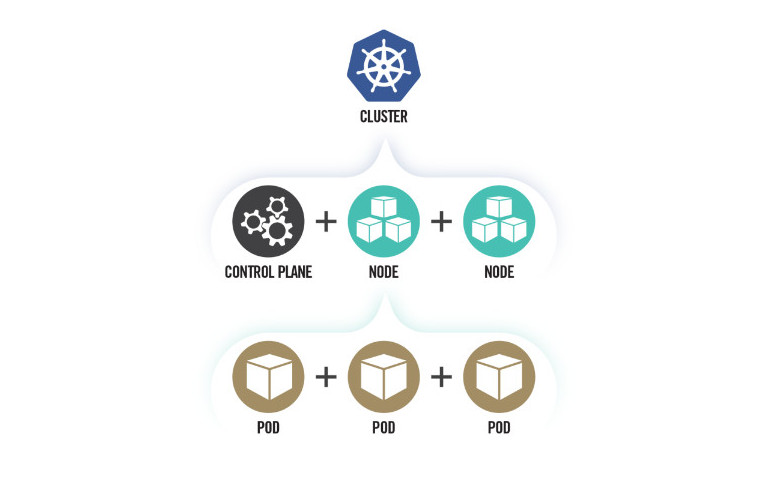
Kubernetes is a popular open-source solution for deploying, scaling, and managing containerized apps in the cloud, making it an attractive target for cyber attacks.
Hackers are constantly hitting Kubernetes environments, their motivation varying from stealing data, to cryptocurrency mining, to denial-of-service (DoS) that could act as a diversion for other operations.
To help companies make their Kubernetes environment more difficult to compromise, the NSA and CISA released a 52-page cybersecurity technical report that offers guidance for admins to manage Kubernetes securely.
The NSA says that the main three causes for a compromised Kubernetes environment are supply-chain attacks, malicious actors, and insider threats.
While administrators can’t prevent all three risks, they can harden the security of a Kubernetes cluster by avoiding common misconfigurations and applying mitigations to minimize security risks.
The agency notes that supply-chain attacks “are often challenging to mitigate,” adding that a malicious threat actor’s way in is typically exploiting a vulnerability or leveraging misconfigurations.
“Insider threats can be administrators, users, or cloud service providers. Insiders with special access to an organization’s Kubernetes infrastructure may be able to abuse these privileges” - the National Security Agency
In broad strokes, the defensive actions against this these threats is to scan containers and Pods for bugs and misconfigurations; use the least privileges to run run Pods and containers (unless higher permissions are needed), and use network separation, strong authentication, properly configured firewalls, and audit logs.
Admins should also review all Kubernetes settings regularly and ensure that the system benefits from the latest updates, patches, and available upgrades.
Titled “Kubernetes Hardening Guidance,” the document goes through each of the following security recommendations, with examples:
Kubernetes Pod security:
Use containers built to run applications as non-root users
- Where possible, run containers with immutable file systems
- Scan container images for possible vulnerabilities or misconfigurations
- Use a Pod Security Policy to enforce a minimum level of security including:
- Preventing privileged containers
- Denying container features frequently exploited to breakout, such as hostPID, hostIPC, hostNetwork, allowedHostPath
- Rejecting containers that execute as the root user or allow elevation to root
- Hardening applications against exploitation using security services such as SELinux, AppArmor, and seccomp
Network separation and hardening:
- Lock down access to control plane nodes using a firewall and role-based access control (RBAC)
- Further limit access to the Kubernetes etcd server
- Configure control plane components to use authenticated, encrypted communications using Transport Layer Security (TLS) certificates
- Set up network policies to isolate resources. Pods and services in different namespaces can still communicate with each other unless additional separation is enforced, such as network policies
- Place all credentials and sensitive information in Kubernetes Secrets rather than in configuration files. Encrypt Secrets using a strong encryption method
Authentication and authorization:
- Disable anonymous login (enabled by default)
- Use strong user authentication
- Create RBAC policies to limit administrator, user, and service account activity
Log auditing:
- Enable audit logging (disabled by default)
- Persist logs to ensure availability in the case of node, Pod, or container level failure
- Configure a metrics logger
Upgrading and application security practices:
- Immediately apply security patches and updates
- Perform periodic vulnerability scans and penetration tests
- Remove components from the environment when they are no longer needed
Read the full Kubernetes Hardening Guidance document [PDF] from the NSA and CISA.
Related Articles:
NSA: Russian GRU hackers use Kubernetes to run brute force attacks
CISA launches vulnerability disclosure platform for federal agencies
NSA shares guidance on how to secure your wireless devices
FBI reveals top targeted vulnerabilities of the last two years
Attackers deploy cryptominers on Kubernetes clusters via Argo Workflows
Statement by HUD Deputy Secretary Todman on the Department Efforts to Connect People to Emergency Rental Assistance and Prevent Evictions
Raising awareness >
Statement by HUD Deputy Secretary Todman on the Department Efforts to Connect People to Emergency Rental Assistance and Prevent Evictions
WASHINGTON – U.S. Department of Housing and Urban Development (HUD) Deputy Secretary Adrianne Todman on Wednesday issued the following statement following the Centers for Disease Control’s (CDC) order halting evictions in communities with high or substantial rates of COVID-19 transmission levels through October 3, 2021:
“Our Department calls on landlords and owners who do business with HUD to access the Emergency Rental Assistance Program and do everything they can to keep families housed during this historically difficult time. The Emergency Rental Assistance Program is available in every state and will help landlords and owners receive past due rent and allow tenants to remain in their homes.
“Secretary Fudge has given direction to HUD’s leadership to identify any and all of HUD’s authorities that will require landlords and owners who do business with HUD to prevent evictions, including accessing rent relief funds.
“HUD is doing our part to raise awareness about the availability of financial assistance to assist with past due and current rent costs and using every tool at our disposal to prevent evictions broadly. We have shared information on the Emergency Rental Assistance Program with public housing authorities, Tribes and Tribally-Designated Housing Entities, private landlords, tenants, and other stakeholders to help ease program implementation at the state and local level and encourage people to apply for assistance. Our goal is to support the Department of Treasury, who is the federal administrator of the Emergency Rental Assistance Program, and their grantees in getting this assistance to those who need it most as quickly as possible. HUD continues our work, as part of a whole of government approach, to protect the millions of families behind on their rent due to the economic realities of the pandemic.”
Background:
HUD has also taken the following actions to prevent evictions and inform communities of their responsibilities and rights:
- Extended its foreclosure-related eviction moratorium for families living in housing insured by the Federal Housing Administration through September 30, 2021. The Office of Public and Indian Housing also extended its moratorium for properties occupied by Native Americans and Native Hawaiians with mortgage loans guaranteed under the Section 184 Indian Home Loan Guarantee and Section 184A Native Hawaiian Housing Loan Guarantee programs. HUD is reviewing additional legal authorities provided to the Department that can be used to stop evictions for vulnerable families;
- Streamlined requirements to allow HUD-assisted households to quickly recertify their income if they have experienced a drop in income, ensuring that their housing remains stable;
- Made clear that federally-backed housing providers must provide 30 days’ notice prior to issuing a notice to vacate;
- Released extensive eviction prevention resources for public housing authorities, Tribes, and Tribally-Designated Housing Entities that highlight best practices to keep families housed and answer frequently asked questions;
- Issued guidance through HUD’s Office of Fair Housing and Equal Opportunity to protect against selective evictions toward protected classes such as race and national origin in violation of the Fair Housing Act—even when the eviction might otherwise have been lawful. This guidance also explains that the Act requires housing providers to make reasonable accommodations for tenants with disabilities, including exceptions or modifications to eviction policies and procedures that may be necessary because of tenants’ disabilities. HUD allocated $19.4 million to provide support to fair housing enforcement organizations to respond to fair housing inquires and complaints related to the pandemic;
- Released an inaugural Eviction Protection Grant Program that will fund $20 million for eviction protection and diversion services for low-income tenants at risk of or subject to eviction. More information on the Notice of Funding Opportunity can be found here;
- Supported HUD grantees and stakeholders to ensure the best use of the various relief resources, including the Emergency Rental Assistance Program, and HUD’s various Native American housing programs to prevent evictions and homelessness.
-
Flash News: Ukraine Intercepts Russian Kh-59 Cruise Missile Using US VAMPIRE Air Defense System Mounted on Boat. Ukrainian forces have made ...

