IT security researchers from Ruhr-Universität Bochum (RUB) and the Niederrhein University of Applied Sciences have discovered 14 new types of 'XS-Leak' cross-site leak attacks against modern web browsers, including Google Chrome, Microsoft Edge, Safari, and Mozilla Firefox.
These types of side-channel attacks are called 'XS-Leaks,' and allow attacks to bypass the 'same-origin' policy in web browsers so that a malicious website can steal info in the background from a trusted website where the user enters information.
"The principle of an XS-Leak is to use such side-channels available on the web to reveal sensitive information about users, such as their data in other web applications, details about their local environment, or internal networks they are connected to," explains the XS-Leaks wiki.
For example, an XS-Leak attack could help a background site siphon the email inbox contents from an active tab used for accessing webmail.
Cross-site leaks aren't new, but as the researchers point out, not all of them have been identified and classified as XS-Leaks, and their root cause remains unclear.
Their research aims to systematically search for new XS-Leaks, evaluate potential mitigations, and generally gain a better understanding of how they work.
Finding new XS-Leaks
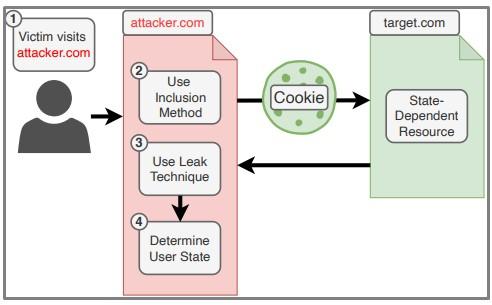
The researchers first identified three characteristics of cross-site leaks and evaluated all inclusion methods and leak techniques for a large set of web browsers.
The three main ingredients of all XS-Leaks are inclusion methods, leak techniques, and detectable differences.
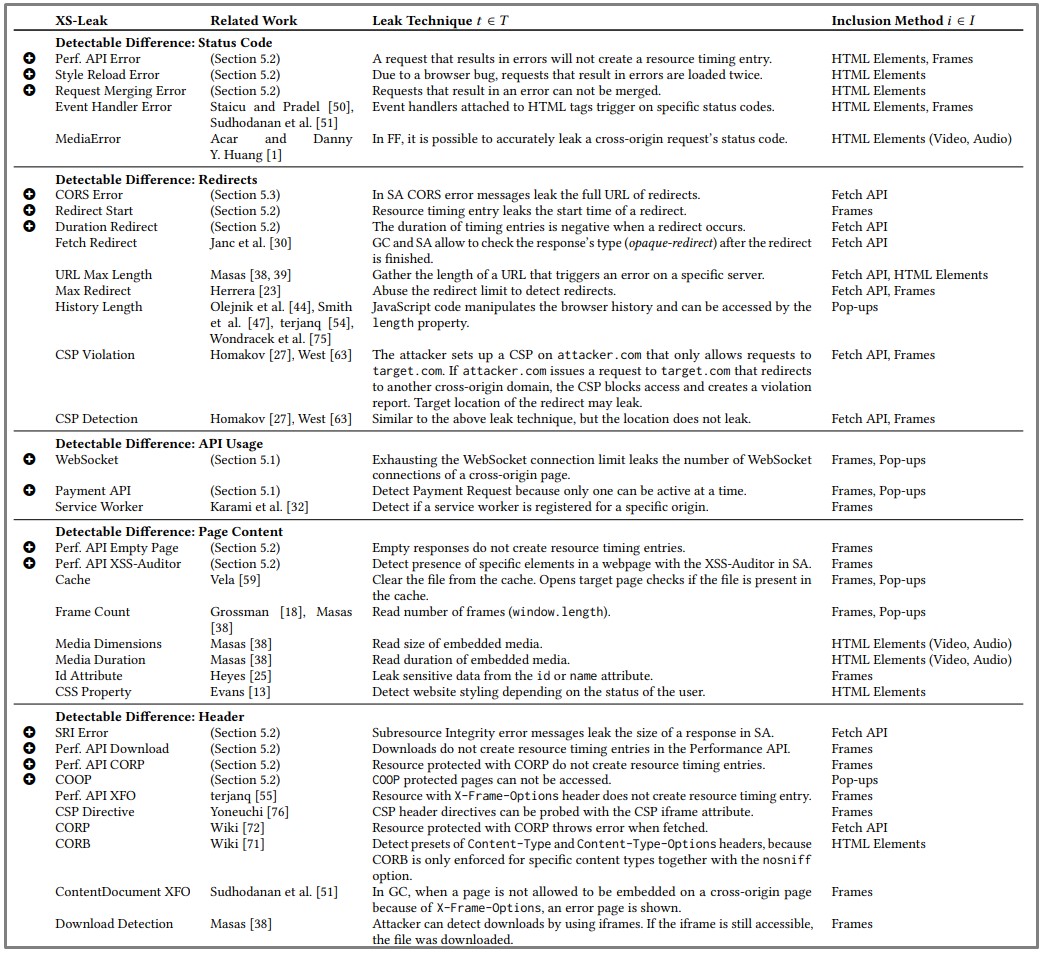
After creating a model based on the above, the researchers found 34 XS-Leaks, 14 of which were novel (marked with a plus sign below).
Next, they tested the 34 XS-Leaks against 56 combinations of browsers and operating systems to determine how vulnerable each of them was.
Then they built a web application named XSinator, consisting of three components:
- A testing site that acts as the attacker page, implementing known and novel X-Leaks
- A vulnerable web app that simulates the behavior of a state-dependent resource.
- A database containing all previous test results.
You can visit the XSinator page yourself and run the test to see how well your web browser and OS fare against the 34 X-Leaks.
You can find a full list of XS-leaks that various browsers are vulnerable to below:
How to defend against X-Leaks
Mitigating or addressing the risks that arise from these side-channel attacks need to be resolved by browser developers.
Researchers suggest denying all event handler messages, minimizing error message occurrences, applying global limit restrictions, and creating a new history property when redirection occurs.