Tuesday, December 21, 2021
NO STOPPING HACKING GONE WILD...More 'Threat Actors' emerge from The Cyber Sphere
Looks like that is a SIGN OF OUR TIME
New stealthy DarkWatchman malware hides in the Windows Registry
A new malware named 'DarkWatchman' has emerged in the cybercrime underground, and it's a lightweight and highly-capable JavaScript RAT (Remote Access Trojan) paired with a C# keylogger.
According to a technical report by researchers at Prevailion, the novel RAT is employed by Russian-speaking actors who target mainly Russian organizations.
The first signs of DarkWatchman's existence appeared in early November as the threat actor began distributing the malware through phishing emails with malicious ZIP attachments.
.png)
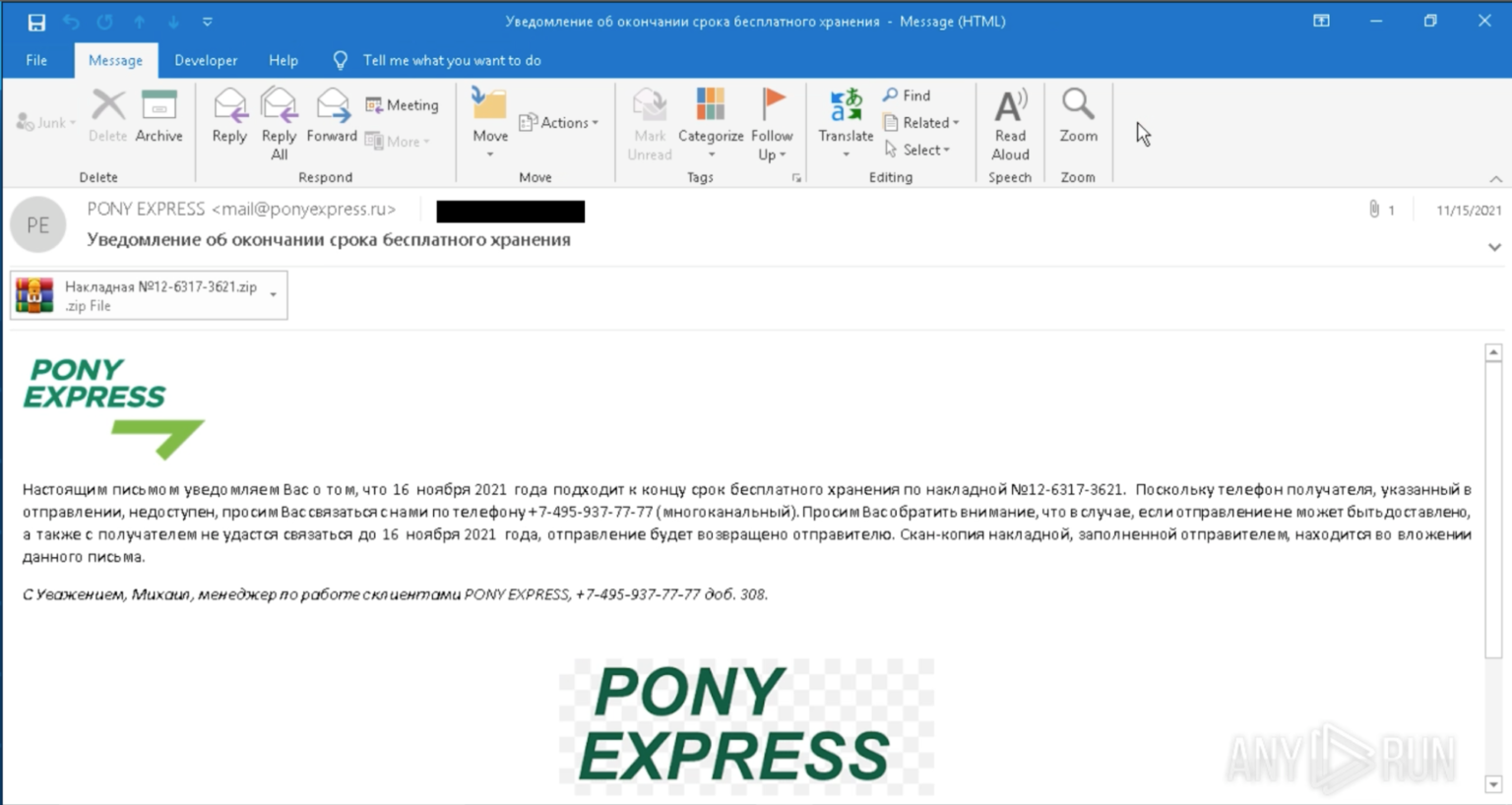
These ZIP file attachments contain an executable using an icon to impersonate a text document. This executable is a self-installing WinRAR archive that will install the RAT and keylogger.
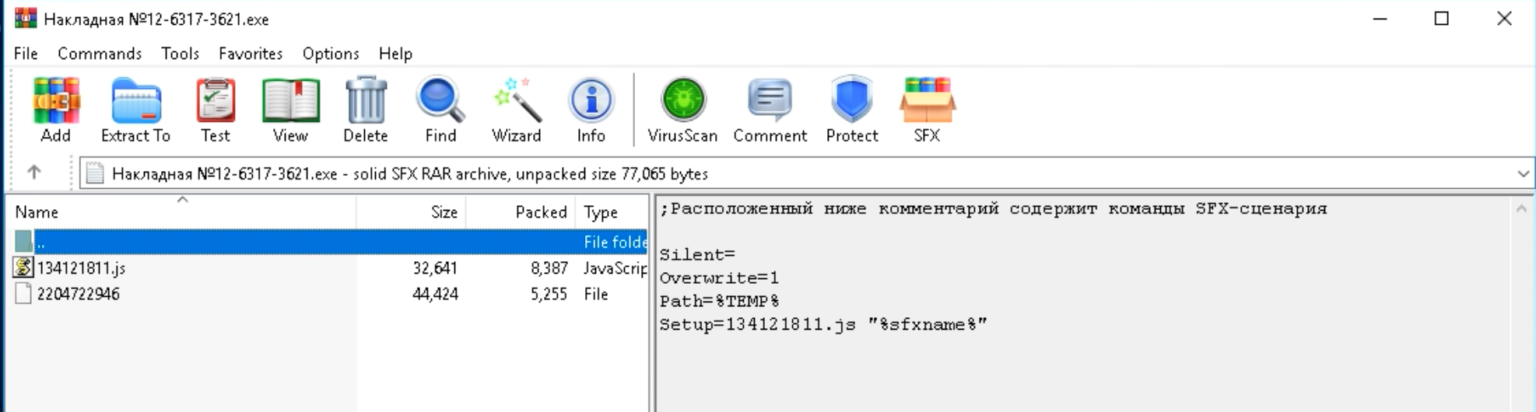
If opened, the user is shown a decoy popup message that reads "Unknown Format," but in reality, the payloads have been installed in the background.
A stealthy 'file-less' RAT
DarkWatchman is a very light malware, with the JavaScript RAT measuring just 32kb in size and the compiled only taking using 8.5kb of space.
It utilizes a large set of "living off the land" binaries, scripts, and libraries, and incorporates stealthy methods to transfer data between modules.
The fascinating aspect of DarkWatchman is its use of the Windows Registry fileless storage mechanism for the keylogger.
Instead of storing the keylogger on disk, a scheduled task is created to launch the DarkWatchman RAT every time the user logs into Windows.
Once launched, DarkWatchmen will execute a PowerShell script that compiles the keylogger using the .NET CSC.exe command and launches it into memory . . .
[...] DarkWatchman’s functional capabilities are the following:
- Execute EXE files (with or without the output returned)
- Load DLL files
- Execute commands on the command line
- Execute WSH commands
- Execute miscellaneous commands via WMI
- Execute PowerShell commands
- Evaluate JavaScript
- Upload files to the C2 server from the victim machine
- Remotely stop and uninstall the RAT and Keylogger
- Remotely update the C2 server address or call-home timeout
- Update the RAT and Keylogger remotely
- Set an autostart JavaScript to run on RAT startup
- A Domain Generation Algorithm (DGA) for C2 resiliency
- If the user has admin permissions, it deletes shadow copies using vssadmin.exe
The ransomware hypothesis
Prevailion theorizes that DarkWatchman may be tailored by/for ransomware groups that need to empower their less capable affiliates with a potent and stealthy tool.
The malware can load additional payloads remotely, so it could be used as a stealthy first-stage infection for subsequent ransomware deployment.
Since DarkWatchman can communicate to actor-controlled domains after the initial foothold, the ransomware operator could take over and deploy the ransomware or handle the file exfiltration directly.
This approach would degrade the affiliate's role to that of a network infiltrator and simultaneously make RaaS operations more clinical and efficient.
-
Fix your home Wi-Fi with this 4.3 Gbps mesh router, now just $245
The Gryphon AX WiFi Router takes advantage of the mesh approach. This powerful device delivers up to 4.3 Gbps on its own, and you can pair two together for even better coverage. Right now, it's 12% off MSRP at just $245.
- BleepingComputer Deals
- December 20, 2021
- 03:46 PM
 0
0
-
Microsoft warns of easy Windows domain takeover via Active Directory bugs
Microsoft warned customers today to patch two Active Directory domain service privilege escalation security flaws that, when combined, allow attackers to easily takeover Windows domains.
- Sergiu Gatlan
- December 20, 2021
- 02:51 PM
 3
3
-
Meta sues people behind Facebook and Instagram phishing
Meta (formerly known as Facebook) has filed a federal lawsuit in California court to disrupt phishing attacks targeting Facebook, Messenger, Instagram, and WhatsApp users.
- Sergiu Gatlan
- December 20, 2021
- 01:37 PM
 1
1
-
FBI: State hackers exploiting new Zoho zero-day since October
The Federal Bureau of Investigation (FBI) says a zero-day vulnerability in Zoho's ManageEngine Desktop Central has been under active exploitation by state-backed hacking groups (also known as APTs or advanced persistent threats) since at least October.
- Sergiu Gatlan
- December 20, 2021
- 01:06 PM
 0
0
-
UK govt shares 585 million passwords with Have I Been Pwned
The United Kingdom's National Crime Agency has contributed more than 585 million passwords to the Have I Been Pwned service that lets users check if their login information has leaked online.
- Ionut Ilascu
- December 20, 2021
- 12:49 PM
 0
0
-
Log4j vulnerability now used to install Dridex banking malware
Threat actors now exploit the critical Apache Log4j vulnerability named Log4Shell to infect vulnerable devices with the notorious Dridex banking trojan or Meterpreter.
- Lawrence Abrams
- December 20, 2021
- 11:33 AM
 0
0
-
T-Mobile says it blocked 21 billion scam calls this year
T-Mobile says it blocked 21 billion scam, spam, and unwanted robocalls this year through its free Scam Shield robocall and scam protection service, amounting to an average of 1.8 billion scam calls identified or blocked every month.
- Sergiu Gatlan
- December 20, 2021
- 10:46 AM
 0
0
-
This $40 bundle can help get you started in cybersecurity
The 2022 Masters in Cyber Security Certification Bundle helps you build the required résumé, with nine courses covering all the fundamentals. The included training is worth $1,800, but you can get it today for only $39.99.
- BleepingComputer Deals
- December 20, 2021
- 07:16 AM
 0
0
-
Phishing attacks impersonate Pfizer in fake requests for quotation
Threat actors are conducting a highly targeted phishing campaign impersonating Pfizer to steal business and financial information from victims.
- Bill Toulas
- December 20, 2021
- 06:00 AM
 0
0
Assange Faces Extradition...
The Prosecution of Julian Assange Absolutely Threatens Freedom of the Press
The Biden administration should abandon a course that could lead to the criminalization of whistleblowers and investigative journalism.
"The Constitution does not prohibit assaults on freedom of the press because the notoriously vain founders were fond of the printers, who in the first years of the Republic produced what President George Washington decried as “diabolical…outrages on common decency.”
Washington’s thin-skinned successor, John Adams, had one printer arrested for allegedly libeling the president “in a manner tending to excite sedition and opposition to the laws.” Adams signed the Alien and Sedition Acts, which made it a crime to “write, print, utter or publish…malicious writing or writings against the government of the United States, or either house of the Congress of the United States, or the President of the United States.” He then had one of his leading critics, Matthew Lyon, tried and jailed after the representative from Vermont derided the second president’s “ridiculous pomp.” Lyon, it was charged, was “a malicious and seditious person, and of a depraved mind and a wicked and diabolical disposition.” Thomas Jefferson, no stranger to scandal, was similarly uncharitable. He deplored “the putrid state into which our newspapers have passed and the malignity, the vulgarity, and mendacious spirit of those who write for them.”
In other words, the founders rebuked the print publishers of their day with language every bit as venomous as that employed by contemporary US officials when they speak of Julian Assange, the WikiLeaks publisher whom the Biden administration proposes to try on espionage charges stemming from the 2010 publication of evidence of “Collateral Murder” atrocities committed by the US military in Iraq and Afghanistan. . . 
[...] If we are serious about protecting the right of those who are widely acknowledged as journalists to track down and publish classified information about what governments do in our name but without our informed consent, then we must defend the right of more controversial printers and web publishers to obtain and distribute the same.
That understanding is supposed to infuse the public discourse about press freedom in the United States. But it only rarely does. Too frequently, prominent political and media voices go silent—or, at least, soft—when real fights over the First Amendment are being fought. It’s particularly concerning that there isn’t a louder outcry now, from across the political spectrum, regarding the prosecution of Assange. . .It is not necessary to make Assange a hero in order to oppose his prosecution. But it is necessary to reject a project of successive presidential administrations that will—if seen through to its conclusion—set a precedent for prosecuting journalists and publishers. . ."
John Nichols, the author of this article published article yesterday wraps up his logical argument saying: " I share the view of Ben Wizner, the director of the ACLU Speech, Privacy, and Technology Project, who recently explained:
The prosecution of Julian Assange poses a grave threat to press freedom. Bringing criminal charges against a publisher for the publication of truthful information establishes a dangerous precedent that can be used to target all news organizations that hold the government accountable by publishing its secrets. Any prosecution by the United States of Mr. Assange would be unprecedented and unconstitutional, and would open the door to criminal investigations of other news organizations. The government needs to immediately drop its charges against him.
Those of us who believe in the need for a robust and genuinely free press must recognize that IFJ General Secretary Anthony Bellanger was right when he declared: “President Joe Biden must end the years of politically motivated prosecution of Julian Assange by finally dropping the charges against him. The criminalization of whistleblowers and investigative journalists has no place in a democracy.”
========================================================================
RELATED CONTENT ON THIS BLOG --> Use the Searchbox
Monday, December 20, 2021
Intercept and Exfiltrate: NET EFFECT: Able to Compromise and Capture Any Passing Traffic
Backdoor gives hackers complete control over federal agency network
Avast researchers say the malware has ties to a previously seen espionage hack.

"A US federal agency has been hosting a backdoor that can provide total visibility into and complete control over the agency network, and the researchers who discovered it have been unable to engage with the administrators responsible, security firm Avast said on Thursday.
The US Commission on International Religious Freedom, associated with international rights, regularly communicates with other US agencies and international governmental and nongovernmental organizations. The security firm published a blog post after multiple attempts failed to report the findings directly and through channels the US government has in place. The post didn't name the agency, but a spokeswoman did in an email. Representatives from the commission didn't respond to an email seeking comment.
Members of Avast’s threat intelligence team wrote:
While we have no information on the impact of this attack or the actions taken by the attackers, based on our analysis of the files in question, we believe it’s reasonable to conclude that the attackers were able to intercept and possibly exfiltrate all local network traffic in this organization. This could include information exchanged with other US government agencies and other international governmental and nongovernmental organizations (NGOs) focused on international rights. We also have indications that the attackers could run code of their choosing in the operating system’s context on infected systems, giving them complete control.
Bypassing firewalls and network monitoring
The backdoor works by replacing a normal Windows file named oci.dll with two malicious ones—one early in the attack and the other later on. The first imposter file implements WinDivert, a legitimate tool for capturing, modifying, or dropping network packets sent to or from the Windows network stack. The file allows the attackers to download and run malicious code on the infected system. Avast suspects the main purpose of the downloader is to bypass firewalls and network monitoring.
At a later stage in the attack, the intruders replaced the fake oci.dll downloader with code that decrypts a malicious file named SecurityHealthServer.dll and loads it into memory. The functions and flow of this second fake DLL are almost identical to rcview40u.dll, a malicious file that was dropped in espionage-driven supply chain hacks that targeted South Korean organizations in 2018.
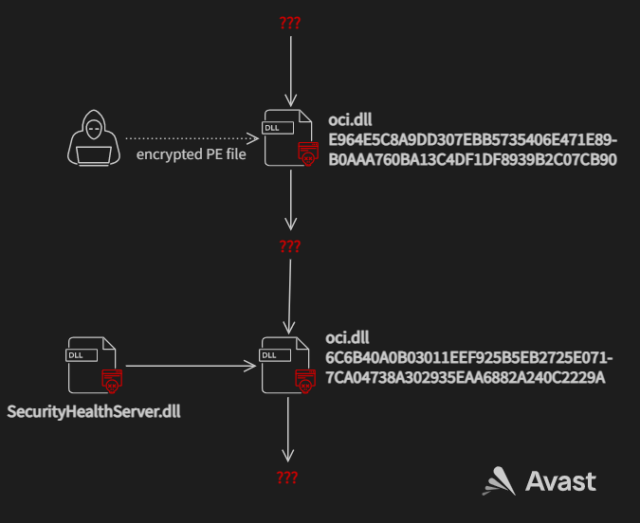
“Because of the similarities between this oci.dll and rcview40u.dll, we believe it is likely that the attacker had access to the source code of the three year-old rcview40u.dll,” Avast researchers wrote. “The newer oci.dll has minor changes like starting the decrypted file in a new thread instead of in a function call which is what rcview40u.dll does. oci.dll was also compiled for x86-64 architecture while rcview40u.dll was only compiled for x86 architecture.”
The net effect of the attack sequence is that the attackers were able to compromise the federal agency network in a way that allowed them to execute code with the same unfettered system rights as the OS and capture any traffic passing into or out of infected machines.
Because officials with the compromised agency didn’t engage with Avast researchers, they can’t be sure precisely what the attackers were doing inside the network. But the implications are clear.
“It is reasonable to presume that some form of data gathering and exfiltration of network traffic happened, but that is informed speculation,” the researchers wrote. “Further because this could have given total visibility of the network and complete control of an infected system it is further reasonable speculation that this could be the first step in a multi-stage attack to penetrate this, or other networks more deeply in a classic APT-type operation.”
GREGORY BOVINO: Nazi Cosplay Time in Mineeapolis...Trump's ICE Enforcer
UPDATE ON SUNDAY 25 JANUARY 2026 Top stories Federal agents fatally shoot Alex Pretti in Minneapolis Star Tribune Fact check: Video, witne...
-
Flash News: Ukraine Intercepts Russian Kh-59 Cruise Missile Using US VAMPIRE Air Defense System Mounted on Boat. Ukrainian forces have made ...