Wednesday, March 09, 2022
S & P INDEX: Crossing The Point Where A Short-Term Correction Morphs Into A Longer-Term Down-Trend
Market Extra
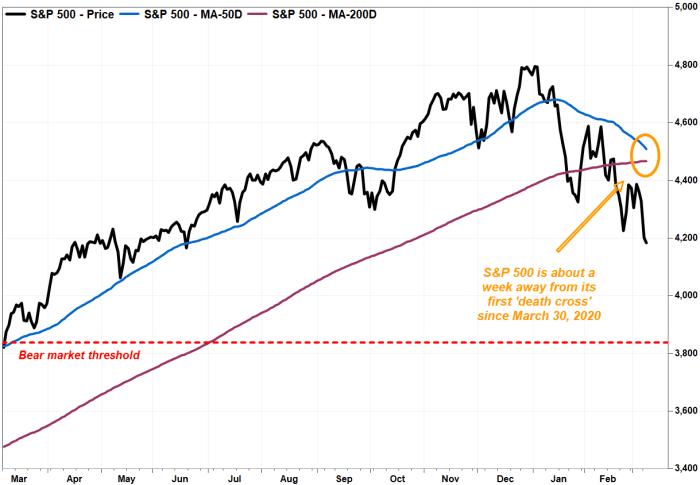
A death cross for the S&P 500 is nearing as inflation fears, Russia’s Ukraine offensive rattles stock-market investors
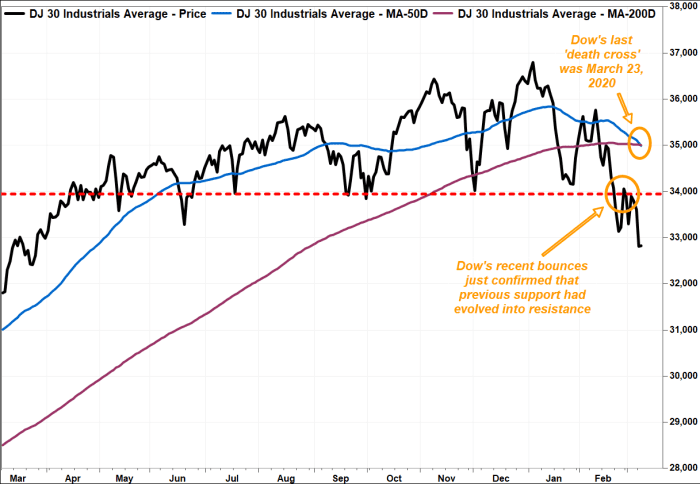
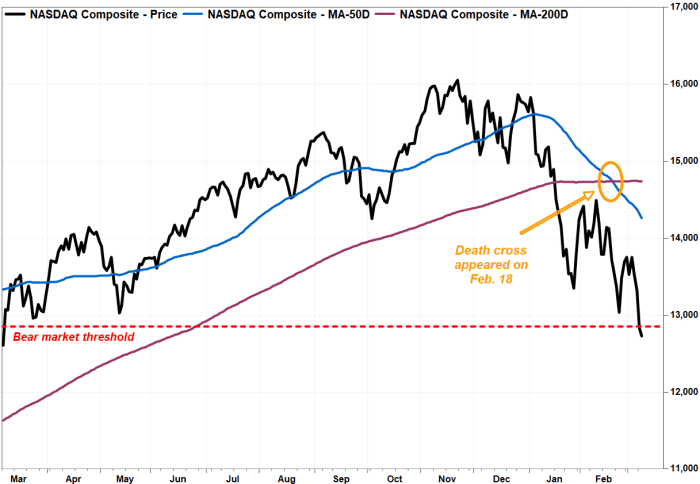
The Dow and Nasdaq Composite have already produced death cross patterns
The S&P 500 index is closing in on a death cross, an ominous chart pattern that underscores the downtrend suffered in an asset.
A death cross appears when the 50-day moving average crosses below the 200-day moving average, an event that many chart watchers view as marking the spot a shorter-term correction morphs into a longer-term downtrend.
At last check, the S&P 500 index SPX,
The approach of a death cross for the broad-market benchmark comes as the Dow Jones Industrial Average DJIA,
A number of other assets have seen death crosses materialize, including the technology-laden Nasdaq Composite Index COMP,
The last time the S&P 500 registered a death cross was nearly two years ago on March 30, 2020, at the height of the pandemic-induced selling. The DJIA saw its death cross materialize at what is widely viewed as stock’s bear-market bottom on March 23, 2020.
It is worth noting that such crosses aren’t necessarily good market-timing indicators, however, as they are well telegraphed, but they can help put a selloff in historical perspective, technicians say.
The decline in the broader market was taking hold, with safe-haven assets, including gold GC00,
See: More than a quarter of Nasdaq-100 stocks are in bear markets—Wall Street sees a buying opportunity
Crude-oil futures CL.1,
The geopolitical tensions combined with fears that the U.S. central bank, and other global monetary policy makers, may need to lift interest rates to combat swelling inflationary pressures, was contributing to the market’s bearish overall tone.
On Monday, the Nasdaq Composite finished in a bear market, falling by 20% from its Nov. 19 peak and the Dow industrials notched its first correction, a decline of at least 10% (but no greater than 20%) in over two years."
— Tomi Kilgore contributed to this article
MUSTANG PANDA: Gone Phishing with Refreshed Lures Targeting European Diplomats
Chinese phishing actors consistently targeting EU diplomats

- March 9, 2022
- 02:02 AM
"The China-aligned group tracked as TA416 (aka Mustang Panda) has been consistently targeting European diplomats since August 2020, with the most recent activity involving refreshed lures to coincide with the Russian invasion of Ukraine.
According to a new report by Proofpoint, TA416 spearheads cyber-espionage operations against the EU, consistently focusing on this long-term role without reaping opportunistic gains.
By keeping their tools and tactics essentially unchanged since 2020 and only refreshing their phishing themes and peripheral components, TA416 has made attribution simple for the analysts.
Timeline of activity
Starting in August 2020, the phishing actors impersonated EU-based organizations to target governments in the continent.

The malicious emails used a DropBox URL to deliver a variant of the PlugX malware, which was previously deployed in attacks against Australian organizations.
In November 2021, TA416 added hidden image trackers on emails to validate message openings and follow a more targeted approach in their campaign.
On January 17, 2022, Proofpoint noticed new delivery attempts involving ZIP files that were custom-named to match the target’s interests.
A change in tactic also occurred at this point, as the ZIP files weren’t fetched from a cloud hosting service but instead leveraged a dropper malware executable.
The four components downloaded this way were the PlugX malware, its loader, the DLL search order hijacker (process loader), and a PDF decoy file.
Finally, on February 28, 2022, the Chinese threat actors were spotted using a compromised diplomat’s address to target other top-ranking officials of NATO countries with lures involving the Russian invasion of Ukraine.
The compromised person worked in refugee and migrant services, an area that was recently targeted by Belarusian hackers as well.
Superficial changes
While the tactics, malware drop, installation, and loading methods remain constant across campaigns, Mustang Panda puts some effort into regularly changing the components used.
“The group uses different legitimate PE files to initiate side-loading, as well as a variety of PlugX DLL loaders including the PotPlayer and DocCon versions,” elaborates the Proofpoint report.
“TA416 also uses different variants of the final PlugX payload in which the communication routines are observed to be different when closely analyzed.”
However, too many elements form a common ground between 2020, 2021, and 2022 campaigns, as reflected in the following table.
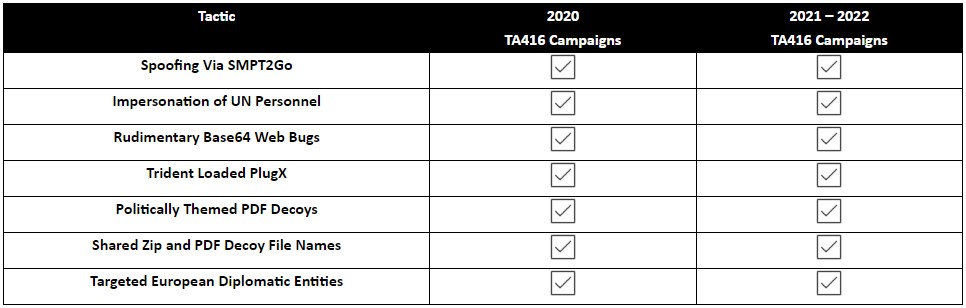
As Proofpoint’s report underlines in conclusion, these superficial variations will continue unabated, especially now that a fresh set of indicators of compromise has been published, so vigilance and good email security practices are advised to all potential targets.
Related Articles:
Google: Russia, China, Belarus state hackers target Ukraine, Europe
Emotet growing slowly but steadily since November resurgence
Google: Chinese hackers target Gmail users affiliated with US govt
Adafruit discloses data leak from ex-employee's GitHub repo
Russia-Ukraine war exploited as lure for malware distribution
ARIZONA DEMO-CRAZY: Gerrymandering Sets Up A 2-Way Far-Right Fringe-Femme Fatale Smackdown
Wendy Rogers refuses to condemn white nationalist leader after GOP senator challenges her
"A day after the Arizona Senate voted to censure Flagstaff Republican Wendy Rogers for comments she made at a white nationalist conference and a string of inflammatory social media posts, another one of her colleagues challenged her to condemn those she had praised in a fiery speech on the Senate floor.
“I contend that this is unbecoming rhetoric, it is inappropriate rhetoric,” Sen. Kelly Townsend, R-Mesa, said on the Senate floor Wednesday. . .
“I received ugly blowback from people on my side,” Townsend said. “Like being in a piranha tank — but I’m not afraid of the piranha tank anymore.”
Townsend herself is no stranger to controversy. In 2019, Townsend toured the border with the extremist group AZ Patriots whose leader walked around the Arizona State Capitol with a “kekistan” flag, a white nationalist symbol used to troll liberal events.
And last year, Townsend compared vaccine supporters to Nazis and sharing an image of needles in the shape of a swastika on social media. When the Anti-Defamation League sharply criticized her rhetoric, Townsend rebuked the 108-year-old Jewish organization. “Learn your history,” she retorted."
-
Flash News: Ukraine Intercepts Russian Kh-59 Cruise Missile Using US VAMPIRE Air Defense System Mounted on Boat. Ukrainian forces have made ...