Saturday, March 26, 2022
Friday, March 25, 2022
RE-COLONIZING ARIZONA: "Pioneer Crossing" - Marking The Mormon Trail with Streets of Luxury Housing
top story spotlight
Ranching family’s project aims to preserve Mesa history
By Scott Shumaker, Tribune Staff Writer
"Streets of luxury housing are planned to replace century-old orange groves and pastures at the end of Val Vista Drive on the south banks of the Salt River in northeast Mesa over the next two to three years.
 While most of the orange groves will be lost, the four families that own the parcels hope years of planning and vetting potential developers will lead to a project that does justice to a historic slice of Mesa and opens it up to residents with public trails and trailheads.
While most of the orange groves will be lost, the four families that own the parcels hope years of planning and vetting potential developers will lead to a project that does justice to a historic slice of Mesa and opens it up to residents with public trails and trailheads.
JUSTICE??? 300 Latter-Day Saints arrived in indigenous lands and territories inhabited by more than 5,000 "Indians", staked out homesteads, claiming water-rights along The Salt River.
=======================================================================
The landowners in this part of Lehi have partnered with Blandford Homes to create an 85-acre planned area development called Pioneer Crossing, a reference to a historic crossing point on the Salt River close by.
SEE THIS RELATED CONTENT
Here in Mesa - and in Tempe and Phoenix and Scottsdale - there's documentation as well for what Frank Midvale called "The Pre-Historic Irrigation of the Salt River Valley" of earlier indigenous cultures that were established for centuries before anyone recorded their versions of that history when evidence of those who were here before was "discovered" and their settlements patterns were mapped.
< Here's a closer look from a Digital Geo Map 2003 uploaded by Richard A. Neely.
Major Hohokam Irrigation Systems in the Lower Salt River Valley
The link is below if you're interested in more details.
But let's note at this point, that it was the usual practice to bury the dead on higher ground above the irrigation canals close to settlements and housing patterns.
Finding artifacts or human remains is often the result of chance - or new construction.
Research Gate
INSERT: Post of this blog from July 2019
Digging-Deeper: Know Your Water + Water-Rights
Here in Arizona in what we now call The Salt River Valley, ancient indigenous cultures created a vast system of canal networks over the centuries before the arrival of new 'Pioneers'. They expanded the open canals to supply natural water resources, converted to private-ownership or municipal control to build vast fortunes for agricultural lands and ranches. After World War II those same lands were needed to create large tracts of housing for Suburban Sprawl and shopping centers and for new industries. Irrigation districts had to be created. Water usage increased. Groundwater had to be tapped into. Water and Wastewater Treatment Plants had to get built. Planning for the future, the city of Mesa once owned 11,400 acres in Pinal County called the Mesa Water Farm. That acreage - and the water-rights - were sold off to Saints Holding Company. . ."
========================================================================
Mesa City Council last week approved an assortment of zoning changes and plan amendments that have cleared the way for the development to proceed.
Councilmember Mark Freeman, who represents the district and worked with stakeholders and the landowners as they contemplated the development, said after the council meeting that the families involved had turned away a lot of offers from developers over the years before arriving at this plan.
He praised the project for blending in with the surrounding area, providing the public with trail access and preserving a piece of the area’s agricultural heritage.
In a January Planning & Zoning Board hearing, neighbors were generally supportive of the development as long as the city put in a new fire station to serve the additional houses. Freeman agreed that a station is needed and said he is working to put a fire station at 32nd and McDowell on the ballot for the next bond election.
One of the properties involved in the development is Tyler Farms, a 40-acre horse boarding ranch. Attorney Brian Campbell, a member of the Tyler family and their representative, said the land surrounding Pioneer Crossing is loaded with history. The plans for the PAD, he said, were built around a vision to protect and highlight its history.
The day after the Council vote March 8, Campbell showed the Mesa Tribune some of that history.
Standing on a hill overlooking the Salt River near Tyler Farms, Campbell pointed down the dry river toward a small white obelisk marking the Lehi Crossing. This spot was an important crossing on the Salt River used by traffic from Fort McDowell and pioneer families in the earliest days of Mesa. . .
Using historical documentation, the family believes the ranch is the site of the 1878 Mesa Company’s “river camp,” where the company camped while laying out the townsite of Mesa.
 > Between the 7th and 14th centuries they built and maintained these extensive irrigation networks along the lower Salt and middle Gila rivers that rivaled the complexity of those used in the ancient Near East, Egypt, and China. These were constructed using relatively simple excavation tools, without the benefit of advanced engineering technologies.
> Between the 7th and 14th centuries they built and maintained these extensive irrigation networks along the lower Salt and middle Gila rivers that rivaled the complexity of those used in the ancient Near East, Egypt, and China. These were constructed using relatively simple excavation tools, without the benefit of advanced engineering technologies.
CYBERCRIME MARKETPLACE HERE IN AMERICA
Intro:
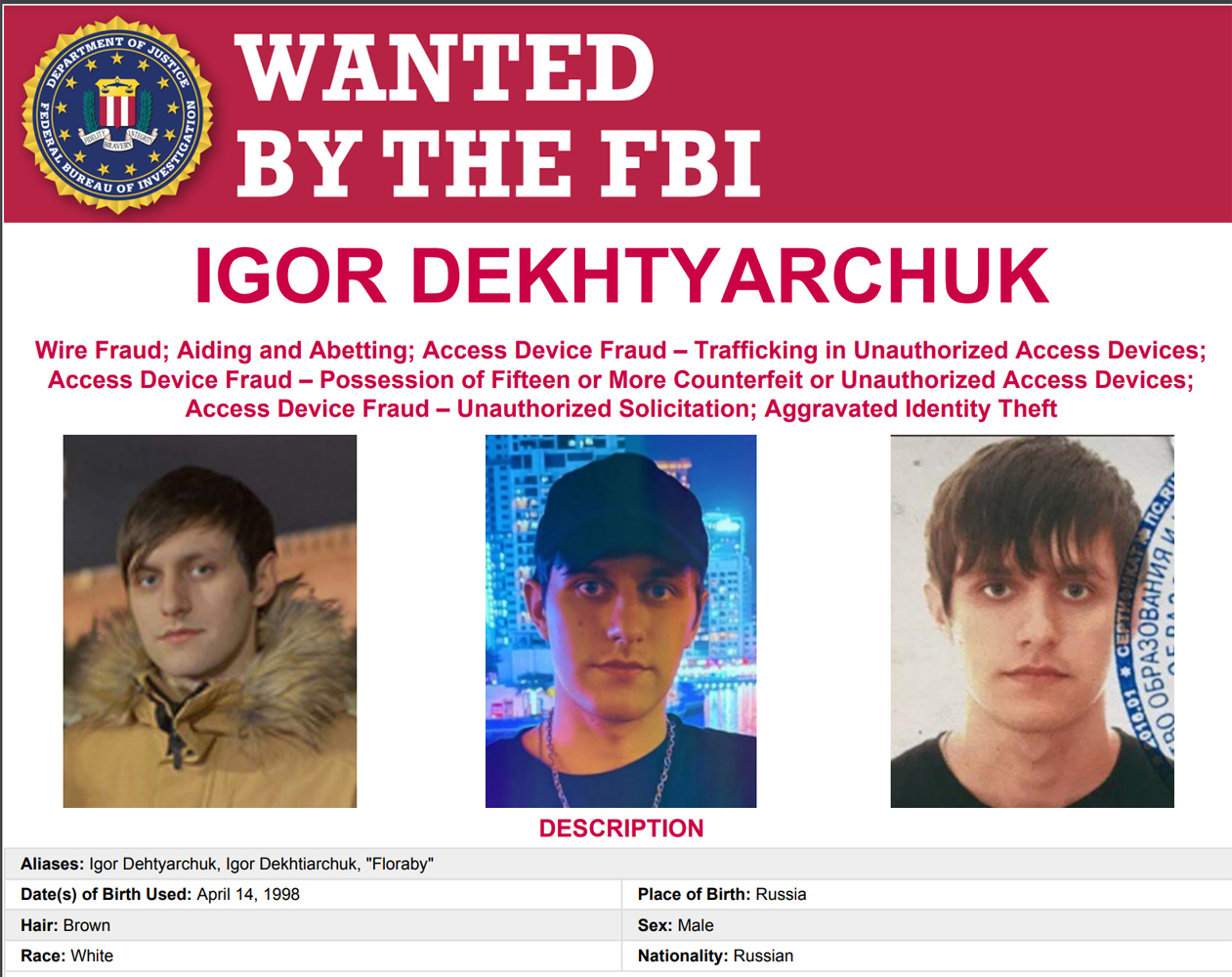
While the indictment did not reveal what cybercrime marketplace was created by Dekhtyarchuk, it did mention that he operated under the alias 'Floraby.'
Using KELA's cybersecurity intelligence service DARKBEAST, BleepingComputer was able to find a person named 'Floraby' promoting the BAYACC marketplace, which sold compromised credentials.
While the site appears to be down, you can see from archived snapshots that BAYACC sold accounts for various companies, including eBay, Amazon, SamsClub, and PayPal, with the prices advertised in Russian Rubles
A Russian national has been indicted by the US DOJ and added to the FBI's Cyber Most Wanted list for allegedly creating and managing a cybercrime marketplace.
Igor Dekhtyarchuk, a resident of Russia, was indicted in the Eastern District of Texas for running the cybercrime marketplace that sold credit cards, access to compromised devices or accounts, and personal information.
The indictment claims that Dekhtyarchuk launched the marketplace in May 2017 and began promoting it on Russian hacking forums starting with April 2018.
"Dekhtyarchuk began advertising the sale of compromised account data in Russianlanguage hacker forums in April 2018 and opened Marketplace A in May 2018. Dekhtyarchuk immediately began advertising Marketplace A and the products it sold in May 2018," reads the DOJ indictment.
"As of May 2021, Dekhtyarchuk, through Marketplace A, publicly advertised that he has sold over 48,000 compromised email accounts, 25,000 compromised Company B accounts, and 19,000 compromised Company A accounts."
When buyers purchased device access from the marketplace, they were allegedly contacted on Telegram by Dekhtyarchuk or one of his associates and sent either login credentials or a login cookie that allows access to the purchased device or account.
Dekhtyarchuk has since been added to the FBI's Cyber Most Wanted List on charges of Wire Fraud, Access Device Fraud, and Aggravated Identity Theft.
=========================================================================
LATEST ARTICLES
Russia bans Google News for "unreliable" info on war in Ukraine
Roskomnadzor, Russia's telecommunications regulator, has banned Alphabet's news aggregator service Google News and blocked access to the news.google.com domain for providing access to "unreliable information" on the ongoing war in Ukraine.
- Sergiu Gatlan
- March 23, 2022
- 04:55 PM
 13
13
New Mustang Panda hacking campaign targets diplomats, ISPs
An ongoing Mustang Panda campaign that has started at least eight months ago has been uncovered by threat analysts who also managed to sample and analyze custom malware loaders and a new Korplug variant.
- Bill Toulas
- March 23, 2022
- 03:13 PM
 0
0
FBI: Ransomware hit 649 critical infrastructure orgs in 2021
The Federal Bureau of Investigation (FBI) says ransomware gangs have breached the networks of at least 649 organizations from multiple US critical infrastructure sectors last year, according to the Internet Crime Complaint Center (IC3) 2021 Internet Crime Report.
- Sergiu Gatlan
- March 23, 2022
- 03:00 PM
 0
0
GIMMICK: Discovered in Late 2021 Custom Chinese Malware In A Cyber Espionage Campaign
Intro: Well in hindsight, at least we know now months after the fact. . .the malware initializes by performing several data decoding steps and eventually establishes a session to Google Drive, using hard-coded OAuth2 credentials.

Custom macOS malware of Chinese hackers ‘Storm Cloud’ exposed
- March 22, 2022
- 04:49 PM
"Researchers have discovered a previously unknown macOS malware variant called GIMMICK, which is believed to be a custom tool used by a Chinese espionage threat actor known as 'Storm Cloud.'
> The malware was discovered by researchers at Volexity, who retrieved it from the RAM of a MacBook Pro running macOS 11.6 (Big Sur), which was compromised in a late 2021 cyberespionage campaign.
The exposure of custom malware used by sophisticated threat actors isn't common. Those groups operate very carefully, leaving a minimal trace and wiping remnants of the malware to keep their tools secret and evade IoC-based detection.
However, sometimes even the most advanced cybercriminals slip up and leave behind malware that can then be dissected by security researchers, as is the case with GIMMICK.
Dissecting the GIMMICK malware
GIMMICK is a multi-platform malware written in Objective C (macOS), or .NET and Delphi (Windows).
All variants use the same C2 architecture, file paths, behavioral patterns, and heavily abuse Google Drive services, so it's tracked as one tool despite the code differences.
GIMMICK is launched either directly by the user or as a daemon on the system and installs itself as a binary file named 'PLIST,' usually mimicking a heavily used application on the target machine.
Next, the malware initializes by performing several data decoding steps and eventually establishes a session to Google Drive, using hard-coded OAuth2 credentials.
(Volexity)
After initialization, GIMMICK loads three malware components, namely DriveManager, FileManager, and GCDTimerManager, with the first being responsible for the below actions:
- Manage the Google Drive and proxy sessions.
- Maintain a local map of the Google Drive directory hierarchy in memory.
- Manage locks for synchronizing tasks on the Google Drive session.
- Handle download and upload tasks to and from the Google Drive session.
Each infected system’s hardware UUID is used as an identifier for the Google Drive directory that corresponds to it.
FileManager manages the local directory where C2 information and command tasks are stored, and the GCDTimerManager undertakes the management of the various GCD objects.
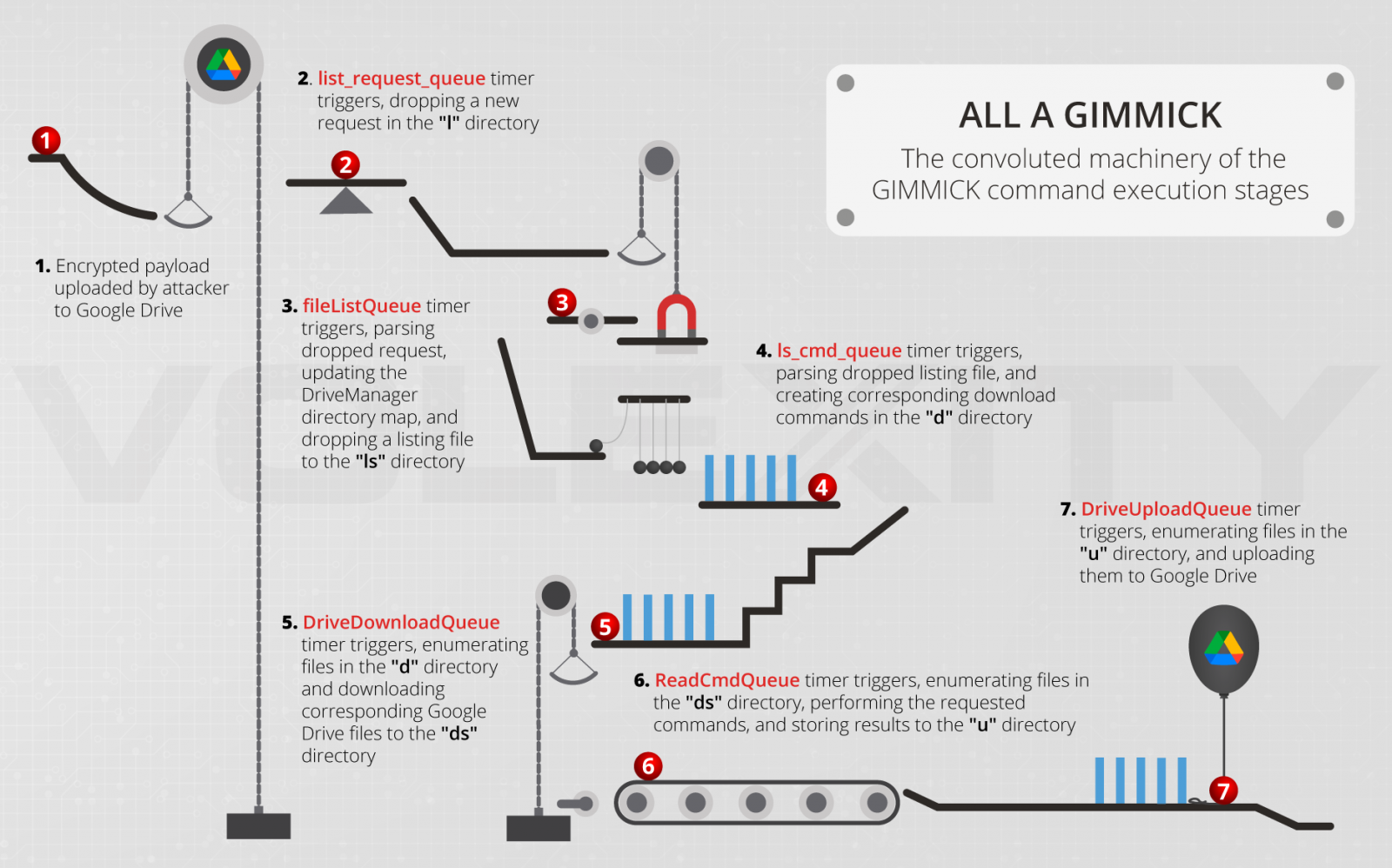
The commands supported by GIMMICK, which arrive on the system in AES-encrypted form, are the following:
- Transmit base system information
- Upload file to C2
- Download file to client
- Execute a shell command and write output to C2
- Set client Google Drive timer interval
- Set client timer interval for client info heartbeat message
- Overwrite client work period information
“Due to the asynchronous nature of the malware operation, command execution requires a staged approach. Though the individual steps occur asynchronously, every command follows the same.” explains Volexity in its technical report
It is this asynchronous design that makes GIMMICK so robust and at the same time complex, so porting it on a new platform, macOS in this case, is a feat that underscores Storm Cloud’s skills and resources.
Volexity notes that the possibility of Storm Cloud buying the malware from a third-party developer and using it exclusively shouldn't be ruled out.
Protect against GIMMICK
Apple has also rolled out new protections to all supported macOS versions with new signatures for XProtect and MRT, which should be able to block and remove the malware since March 17, 2022. To ensure you have received these signatures, follow Apple's support page instructions.
READ MORE DETAILS Go Here >> https://www.bleepingcomputer.com/news/security/custom-macos-malware-of-chinese-hackers-storm-cloud-exposed/
Related Articles:
Hackers exploit new WPS Office flaw to breach betting firms
Google: Chinese state hackers target Ukraine’s government
Microsoft: Ukraine hit with FoxBlade malware hours before invasion
Chinese cyberspies target govts with their ‘most advanced’ backdoor
FritzFrog botnet grows 10x, hits healthcare, edu, and govt systems
Thursday, March 24, 2022
ORWELLIAN REAL ID COMPLIANT REPLACEMENT: All Your Information in One Swipe at Security Checkpoints
Arizona is the first state to put its driver’s license and state ID in Apple’s Wallet
More states will follow soon
/cdn.vox-cdn.com/uploads/chorus_image/image/70661994/Screen_Shot_2022_03_23_at_8.38.33_AM.0.png)
"The first state to officially roll out Apple’s digital driver’s license and state ID is Arizona, the iPhone maker announced Wednesday. “Starting today, Arizonans can add their driver’s license or state ID to Wallet, and tap their iPhone or Apple Watch to seamlessly and securely present it at select TSA security checkpoints in Phoenix Sky Harbor International Airport,” Apple announced in a press release.
If you live in Arizona and want to add your license or ID to Wallet, you can do so right from the Wallet app. Take photos of the front and back of your license or ID, and you will “be prompted to complete a series of facial and head movements during the setup process,” according to Apple. Apple is not the one approving requests to add licenses or IDs to Wallet — instead, the company says Arizona will be responsible for that.
:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/23339657/apple_id.jpg)
If you want to show your digital license or ID to TSA at the airport, here’s what the process looks like, according to Apple:
On their iPhone or Apple Watch, users will be shown which information is requested by the TSA, and can consent to provide it with Face ID or Touch ID, without having to unlock their iPhone or show their ID card. All information is shared digitally, so users do not need to show or hand over their device to present their ID.
According to Apple, during this process, “the TSA will also capture a picture of the traveler for verification purposes.” We’ve asked the TSA for details on where those photos might be stored, how they can ensure they stay private, and if the photos will be deleted after a certain period of time; when we asked Apple, it said it passed our questions to the TSA.
> Initially, only travelers using PSA PreCheck at the Phoenix airport will be able to use the feature, according to a TSA press release. And passengers “must continue” to still carry their physical driver’s license or ID and have it available if needed.
 Real ID-compliant identification cards will be supported by Wallet, Apple spokesperson Heather Norton tells The Verge.
Real ID-compliant identification cards will be supported by Wallet, Apple spokesperson Heather Norton tells The Verge.
You’ll need one of those to fly domestically beginning in May 2023 (though that deadline has already been pushed a couple of times). . .The digital licenses / IDs are right now only available “for use in select states at select TSA checkpoints within Phoenix Sky Harbor International Airport (PHX),” according to Apple’s fine print. Digital hotel keys are available at certain Hyatt hotels. You can add a COVID-19 vaccine card to Wallet only if your healthcare provider or health authority supports the feature. . .
Apple says additional states will offer the driver’s license and ID feature “soon,” including Colorado, Connecticut, Georgia, Hawaii, Iowa, Kentucky, Maryland, Mississippi, Ohio, Oklahoma, the territory of Puerto Rico, and Utah."
Wednesday, March 23, 2022
DHS denied claims that it would destroy evidence following the fatal shooting of Alex Jeffrey Pretti | Daily Beast
Trump-Appointed Judge Blocks Cover-Up in VA Nurse Killing TAMPER-PROOF DHS denied claims that it would destroy evidence following the fata...

-
Flash News: Ukraine Intercepts Russian Kh-59 Cruise Missile Using US VAMPIRE Air Defense System Mounted on Boat. Ukrainian forces have made ...




