Wednesday, April 13, 2022
LATEST ARTICLES 04.13.2022: Bleeping Computer -- Joint Cybersecurity Advisory CISA, NSA, FBI + DOE
US warns of government hackers targeting industrial control systems
"A joint cybersecurity advisory issued by CISA, NSA, FBI, and the Department of Energy (DOE) warns of government-backed hacking groups being able to hijack multiple industrial devices.
The federal agencies said the threat actors could use custom-built modular malware to scan for, compromise, and take control of industrial control system (ICS) and supervisory control and data acquisition (SCADA) devices.
"The APT actors' tools have a modular architecture and enable cyber actors to conduct highly automated exploits against targeted devices. Modules interact with targeted devices, enabling operations by lower-skilled cyber actors to emulate higher-skilled actor capabilities," the joint advisory reads.
"The APT actors can leverage the modules to scan for targeted devices, conduct reconnaissance on device details, upload malicious configuration/code to the targeted device, back up or restore device contents, and modify device parameters."
ICS/SCADA devices at risk of being compromised and hijacked include:
- Schneider Electric MODICON and MODICON Nano programmable logic controllers (PLCs)
- Omron Sysmac NJ and NX PLCs, and
- Open Platform Communications Unified Architecture (OPC UA) servers
DOE, CISA, NSA, and the FBI also found that state-sponsored hackers also have malware that leverages CVE-2020-15368 exploits to target Windows systems with ASRock motherboards to execute malicious code and move laterally to and disrupt IT or OT environments.
New PIPEDREAM malware targeting ICS devices
While the federal agencies did not share any additional info on the hacking tools and malware mentioned in the advisory, Robert M. Lee, the co-founder and CEO of industrial cybersecurity firm Dragos, said the company has been tracking one of the malware strains as PIPEDREAM since its discovery in early 2022.
"Dragos has been analyzing this since early 2022 and working with our partners the best we can to make sure the community is aware," Lee said.
"PIPEDREAM is the seventh ever ICS specific malware. It's highly capable and worth paying attention to."
Dragos assesses with high confidence this was developed by a state actor with the intent on deploying it to disrupt key infrastructure sites.
— Robert M. Lee (@RobertMLee) April 13, 2022
The federal agencies recommend network defenders start taking measures to protect their industrial networks from attacks using these new capabilities and malicious tools.
They advise enforcing multifactor authentication (MFA) for remote access to ICS networks, changing default passwords to ICS/SCADA devices and systems, rotating passwords, and using OT monitoring solutions to detect malicious indicators and behaviors.
Additional mitigation measures can be found within today's advisory, with more information provided by CISA and the Department of Defense on blocking attacks targeting OT systems [PDF], layer network security via segmentation, and reducing exposure across industrial systems."
Related Articles:
US says Russian state hackers breached defense contractors
FBI warns of MFA flaw used by state hackers for lateral movement
CISA orders agencies to patch actively exploited Sophos firewall bug
FBI warns election officials of credential phishing attacks
CISA warns of attacks targeting Internet-connected UPS devices
"A months-long global operation led by Microsoft's Digital Crimes Unit (DCU) has taken down dozens of domains used as command-and-control (C2) servers by the notorious ZLoader botnet.
The court order obtained by Microsoft allowed it to sinkhole 65 hardcoded domains used by the ZLoader cybercrime gang to control the botnet and another 319 domains registered using the domain generation algorithm used to create fallback and backup communication channels.
"During our investigation, we identified one of the perpetrators behind the creation of a component used in the ZLoader botnet to distribute ransomware as Denis Malikov, who lives in the city of Simferopol on the Crimean Peninsula," explained Amy Hogan-Burney, the DCU General Manager.
"We chose to name an individual in connection with this case to make clear that cybercriminals will not be allowed to hide behind the anonymity of the internet to commit their crimes."
Multiple telecommunication providers and cybersecurity firms worldwide partnered with Microsoft's threat intel and security researchers throughout the investigative effort, including ESET, Black Lotus Labs (Lumen's threat intelligence arm), Palo Alto Networks' Unit 42, and Avast.
The Financial Services Information Sharing and Analysis Centers (FS-ISAC) and the Health Information Sharing and Analysis Center (H-ISAC) also contributed data and insights to help strengthen the legal case.
> Zloader (aka Terdot and DELoader) is a widely-known banking trojan first spotted back in August 2015 when deployed in attacks against several British financial companies' customers.
> Like Zeus Panda and Floki Bot, this malware is almost wholly based on the Zeus v2 trojan's source code leaked online over a decade ago.
The malware has been used to target banks worldwide, from Australia and Brazil to North America, with the end goal of harvesting financial data via web injections that use social engineering to trick infected bank customers into handing out authentication codes and credentials.
Zloader also features backdoor and remote access capabilities, and it can be used as a malware loader to drop additional payloads on infected devices.
More recently, operators of multiple ransomware gangs have also used it to deploy malicious payloads such as Ryuk and Egregor.
Reports from ESET and the Microsoft 365 Defender Threat Intelligence Team provide indicators of compromise and further info on defense techniques and ZLoader's attack chains."
Related Articles:
Microsoft: Ukraine hit with FoxBlade malware hours before invasion
New EnemyBot DDoS botnet recruits routers and IoTs into its army
Microsoft April 2022 Patch Tuesday fixes 119 flaws, 2 zero-days
Microsoft: Windows Server now supports automatic .NET updates

Critical Apache Struts RCE vulnerability wasn't fully fixed, patch now
"Apache has fixed a critical vulnerability in its vastly popular Struts project that was previously believed to have been resolved but, as it turns out, wasn't fully remedied. As such, CISA is urging users and administrators to upgrade to the latest, patched Struts 2 versions."
YESTERDAY
Ethereum dev imprisoned for helping North Korea evade sanctions
"Virgil Griffith, a US cryptocurrency expert, was sentenced on Tuesday to 63 months in prison after pleading guilty to assisting the Democratic People's Republic of Korea (DPRK) with technical info on how to evade sanctions."
- Sergiu Gatlan
- April 12, 2022
- 05:42 PM
 0
0
RECORD LOWS THIS YEAR: Ransom DDoS Attacks | Bleeping Computer
Ransom DDoS attacks have dropped to record lows this year
"Extortion denial-of-service activity, the so-called RDDoS (ransom distributed denial-of-service) attacks have taken a tumble in the first quarter of the year, according to recent statistics from Cloudflare.
During a RDDoS attack, the threat actor hits a target company with large amounts of data to cause a service outage. The attacker then demands a ransom to stop the assault.
Ransom DDoS
Threat actors figured out that causing an outage could be a strong incentive for many companies to pay up to become operational again, especially organizations that risk a significant financial impact.
It should be noted that RDDoS attacks are launched by a different type of threat actors than ransomware gangs, who use DDoS to add more pressure on the victim on top of file encryption and the threat to publish stolen data.
Cloudflare reports that ransom DDoS attacks have dropped drastically in 2022, with only 17% of its DDoS-targeted clients reporting an extortion in January, 6% in February, and just 3% in March.
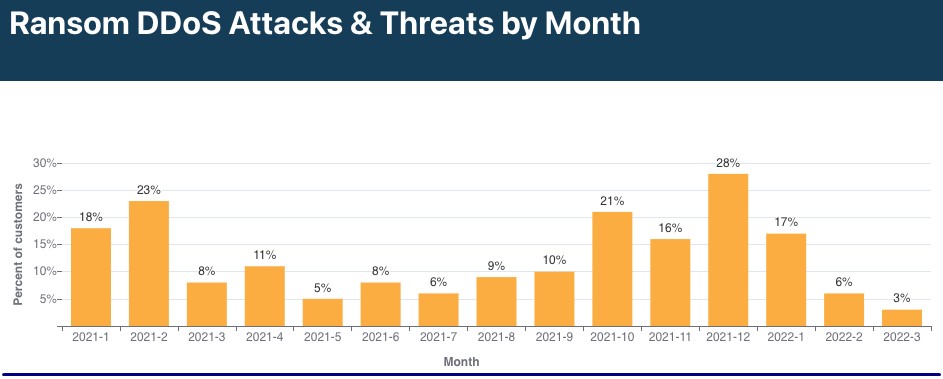
That’s a 28% decrease year over year and a 52% decrease compared to the last quarter of 2021 when ransom DDoS attacks spiked at 28% in the last month.
The reason for this drop remains unclear at this time.
First 2022 trends
On the rising trends reflected in Q1 2022 data, Cloudflare reports a whopping 164% YoY rise in application-layer DDoS attacks.
The most noteworthy trends within that category are a 5,086% QoQ increase in application-layer DDoS attacks against the consumer electronics industry and a 2,131% QoQ increase against online media firms.
Another concerning emerging trend is the reflection-amplification method, which we recently reported as something that has transcended theory and is already under active exploitation.
Reflection attacks start with a small packet reflected inside a closed network while its size gets amplified with each bounce. When reaching the possible upper limit, the resulting massive volume of traffic is channeled to the target.
An interesting in-the-wild exploitation case presented in Cloudflare’s report is that of the Lantronix Discovery Protocol being used in a large number of IoT devices.
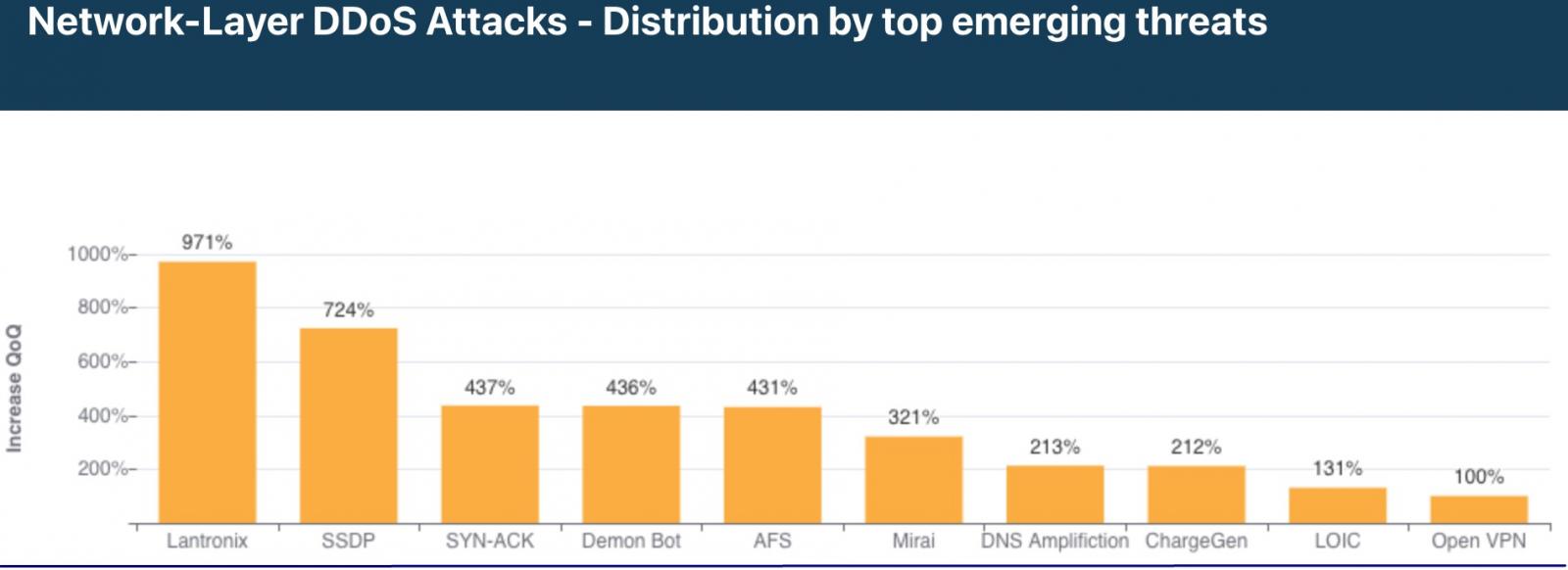
Attackers use 4-byte requests to target publicly exposed Lantronix devices, generating a 30-byte response, reaching an amplification ratio of 7.5x. While this is far from the most impressive ratio we’ve seen lately, it can still be very potent if large enough swarms of devices are recruited in these attacks.
By spoofing the source IP of the victim, the hackers can direct a large number of generated responses to a target, suddenly overwhelming them with an indirect attack.
Finally, Cloudflare reports a massive uptick in volumetric DDoS attacks, with those over 100 Gbps rising by 645% QoQ and those over 10 Mpps growing by over 300% QoQ.
As it has been the case for many years now, DDoS attacks aren’t going out of fashion but instead change form, methods, and traffic mixing tricks, and return to knock at the door of vulnerable, poorly protected, and weak servers."
Related Articles:
Russians bypass website blocks to access Western news sources
Beastmode botnet boosts DDoS power with new router exploits
Hacked WordPress sites force visitors to DDoS Ukrainian targets
BITCOIN SEIZURE MYSTERIES
Hmmm
‘Staggering’ Crypto Seizures Have Cops Struggling to Keep Up
Some criminals see digital assets as easier to hide and transfer. Law enforcement is learning fast.

"One spring day in a village just west of London, residents saw a man being muscled into a car in front of a nearby house. He reappeared with cuts and bruises 13 hours later, but the cops had already discovered the house was a cannabis-growing operation. A separate search of the man’s home in a nearby town turned up something more intriguing—some of the first cryptocurrency that would ever be seized by U.K. police.
That era-defining 2017 case yielded a safety-deposit box containing jewelry, gold bars, £263,000 ($345,000) in cash, and an item that flummoxed the lead investigator, Matthew Durkin, a 19-year veteran of the Surrey police. It was a USB device found in the suspect’s study. The gadget was wrapped in a small notebook, which contained two strings of 12 random words. A young probationary officer recognized the device, a KeepKey, as a virtual currency holder and the words as seed phrases to access crypto wallets. Eventually, police discovered it held 295 Bitcoin. . ."
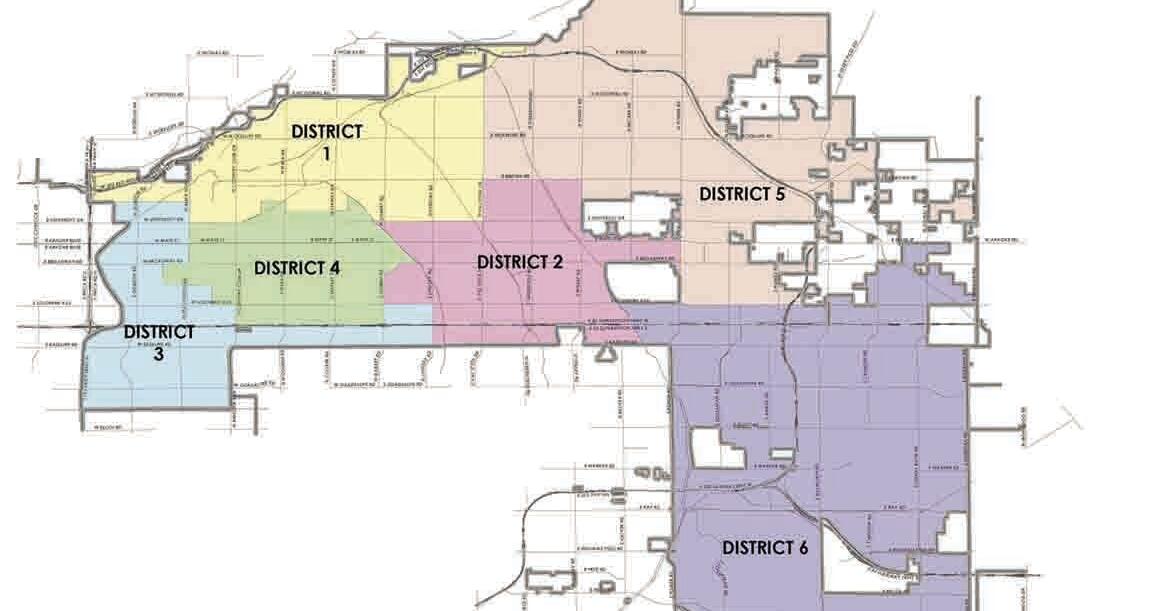
QUICK SKETCHES OF CANDIDATES RUNNING FOR 3 MESA CITY COUNCIL SEATS: Districts 4, 5 and 6
Alicia Goforth has lived in Mesa for 14 years.
Darla Trendler is a business owner who has lived in Mesa for 23 years.
-
Flash News: Ukraine Intercepts Russian Kh-59 Cruise Missile Using US VAMPIRE Air Defense System Mounted on Boat. Ukrainian forces have made ...