Thursday, May 05, 2022
Wednesday, May 04, 2022
You might have missed this ...News from The Other Side
3 May, 2022 15:15
Terror attack foiled near Ukrainian border – Transnistria
 A weaponized cargo drone was intercepted overnight near a large telecom center located in the village of Mayak, the Interior Ministry of the self-proclaimed republic of Transnistria said on Tuesday.
A weaponized cargo drone was intercepted overnight near a large telecom center located in the village of Mayak, the Interior Ministry of the self-proclaimed republic of Transnistria said on Tuesday.
The intercepted drone appeared to be a home-made contraption, jury-rigged from different parts, the ministry said.
“The drone with a diameter of one and a half meters was assembled from various components. The equipment was so powerful it could move loads of up to 20 kilograms to a distance of some 30 kilometers from the operator who controlled it,” it added.
The drone carried a canister containing “unknown brown liquid” and a small barrel containing two kilograms of plastic explosives with radio detonators attached. Imagery released by the Transnistrian authorities suggest the drone was also fitted with a payload release system to drop its deadly cargo.
The aircraft was “neutralized” by the border guards deployed to patrol the crucial facility after it was attacked by unknown assailants late in April. Back then, two large radio masts transmitting Russian radio stations were blown up in the center.
In recent days, Transnistria has endured a string of mysterious incidents involving the region’s critical civilian and military infrastructure. Apart from the attacks on the Mayak broadcasting center, Transnistria’s Ministry of State Security was targeted by three unknown assailants, who fired shoulder-mounted rocket launchers at the building, shattering its windows and damaging its façade. Several explosions also occurred at a military compound outside Transnistria’s capital city of Tiraspol.
The president of the self-proclaimed republic, Vadim Krasnoselsky, blamed the incidents he described as “terror attacks” on Ukrainian nationals, urging Kiev to probe the armed groups that had allegedly infiltrated his region.
Transnistria, officially known as the Pridnestrovian Moldavian Republic (PMR), is an unrecognized state located along a narrow strip of land between the Dniester River and Ukrainian border in the eastern part of Moldova.
The region broke away from Moldova in the early 1990s, shortly after the collapse of the Soviet Union. The region maintains close ties with Russia, with Russian peacekeepers stationed there and a vast part of the local population holding Russian citizenship."
1,2,3 >> DNS POISONING FLAW ...ISPs ordered to block the pirate websites "by any technological means available."
THREE REPORTS:
1 First discovered in 2008 by researcher Dan Kaminsky, DNS poisoning requires a hacker to first masquerade as an authoritative DNS server and then use it to flood a DNS resolver inside an ISP or device with fake lookup results for a trusted domain. When the fraudulent IP address arrives before the legitimate one, end users automatically connect to the imposter site. The hack worked because the unique transaction assigned to each lookup was predictable enough that attackers could include it in fake responses.
Gear from Netgear, Linksys, and 200 others has unpatched DNS poisoning flaw
Vulnerability in 3rd-party libraries can send devices users to malicious sites.

"Hardware and software makers are scrambling to determine if their wares suffer from a critical vulnerability recently discovered in third-party code libraries used by hundreds of vendors, including Netgear, Linksys, Axis, and the Gentoo embedded Linux distribution.
The flaw makes it possible for hackers with access to the connection between an affected device and the Internet to poison DNS requests used to translate domains to IP addresses, researchers from security firm Nozomi Networks said Monday. By feeding a vulnerable device fraudulent IP addresses repeatedly, the hackers can force end users to connect to malicious servers that pose as Google or another trusted site.
The vulnerability, which was disclosed to vendors in January and went public on Monday, resides in uClibc and uClibc fork uClibc-ng, both of which provide alternatives to the standard C library for embedded Linux. Nozomi said 200 vendors incorporate at least one of the libraries into wares that, according to the uClibc-ng maintainer, include the following:
- Linksys WRT54G - Wireless-G Broadband Router
- NetGear WG602 wireless router
- Most Axis network cameras
- Embedded Gentoo
- Buildroot, a configurable means for building busybox/uClibc-based systems.
- LEAF Bering-uClibc, the successor of the Linux Router Project that supports gateways, routers, and firewalls.
- Tuxscreen Linux Phone
[ ]
What's DNS poisoning, anyway?
DNS poisoning and its DNS cache-poisoning relative allow hackers to replace the legitimate DNS lookup for a site such as google.com or arstechnica.com—normally 209.148.113.38 and 18.117.54.175 respectively—with malicious IP addresses that can masquerade as those sites as they attempt to install malware, phish passwords, or carry out other nefarious actions . . ."
2 The three lawsuits were filed by Israeli TV and movie producers and providers against Doe defendants who operate the websites. Each of the three rulings awarded damages of $7.65 million. TorrentFreak pointed out the rulings in an article Monday.
Every ISP in the US has been ordered to block three pirate streaming services
ISPs ordered to block the pirate websites "by any technological means available."

"A federal judge has ordered all Internet service providers in the United States to block three pirate streaming services operated by Doe defendants who never showed up to court and hid behind false identities.
The blocking orders affect Israel.tv, Israeli-tv.com, and Sdarot.tv, as well as related domains listed in the rulings and any other domains where the copyright-infringing websites may resurface in the future. The orders came in three essentially identical rulings (see here, here, and here) issued on April 26 in US District Court for the Southern District of New York.
Each ruling provides a list of 96 ISPs that are expected to block the websites, including Comcast, Charter, AT&T, Verizon, and T-Mobile. But the rulings say that all ISPs must comply even if they aren't on the list:
It is further ordered that all ISPs (including without limitation those set forth in Exhibit B hereto) and any other ISPs providing services in the United States shall block access to the Website at any domain address known today (including but not limited to those set forth in Exhibit A hereto) or to be used in the future by the Defendants ("Newly Detected Websites") by any technological means available on the ISPs' systems. The domain addresses and any Newly Detected Websites shall be channeled in such a way that users will be unable to connect and/or use the Website, and will be diverted by the ISPs" DNS servers to a landing page operated and controlled by Plaintiffs (the "Landing Page").
That landing page is available here and cites US District Judge Katherine Polk Failla's "order to block all access to this website/service due to copyright infringement."
"If you were harmed in any way by the Court's decision you may file a motion to the Federal Court in the Southern District of New York in the above case," the landing page also says.
[. ] Rulings further target web hosts and banks. . .Financial institutions face similar bans on doing business with the blocked websites. The rulings directly target the defendants' monetary accounts, saying that plaintiffs "shall have the ongoing authority to serve this Order on any party controlling or otherwise holding such accounts" until they have "recovered the full payment of monies owed to them by any Defendant under this Order." This applies to PayPal, banks, and payment providers in general."
3 It’s not the kind of security discovery that happens often. A previously unknown hacker group used a novel backdoor, top-notch tradecraft, and software engineering to create an espionage botnet that was largely invisible in many victim networks.
Botnet that hid for 18 months boasted some of the coolest tradecraft ever
Once-unknown group uses a tunnel fetish and a chameleon's ability to blend in.

". . .The group, which security firm Mandiant is calling UNC3524, has spent the past 18 months burrowing into victims’ networks with unusual stealth. In cases where the group is ejected, it wastes no time reinfecting the victim environment and picking up where things left off. There are many keys to its stealth, including:
- The use of a unique backdoor Mandiant calls Quietexit, which runs on load balancers, wireless access point controllers, and other types of IoT devices that don’t support antivirus or endpoint detection. This makes detection through traditional means difficult.
- Customized versions of the backdoor that use file names and creation dates that are similar to legitimate files used on a specific infected device.
- A live-off-the-land approach that favors common Windows programming interfaces and tools over custom code with the goal of leaving as light a footprint as possible.
- An unusual way a second-stage backdoor connects to attacker-controlled infrastructure by, in essence, acting as a TLS-encrypted server that proxies data through the SOCKS protocol.
A tunneling fetish with SOCKS
In a post, Mandiant researchers Doug Bienstock, Melissa Derr, Josh Madeley, Tyler McLellan, and Chris Gardner wrote:
Throughout their operations, the threat actor demonstrated sophisticated operational security that we see only a small number of threat actors demonstrate. The threat actor evaded detection by operating from devices in the victim environment’s blind spots, including servers running uncommon versions of Linux and network appliances running opaque OSes. These devices and appliances were running versions of operating systems that were unsupported by agent-based security tools, and often had an expected level of network traffic that allowed the attackers to blend in. The threat actor’s use of the QUIETEXIT tunneler allowed them to largely live off the land, without the need to bring in additional tools, further reducing the opportunity for detection. This allowed UNC3524 to remain undetected in victim environments for, in some cases, upwards of 18 months.
The SOCKS tunnel allowed the hackers to effectively connect their control servers to a victim’s network where they could then execute tools without leaving traces on any of the victims' computers. . .
[. ]
One of the ways the hackers maintain a low profile is by favoring standard Windows protocols over malware to move laterally. To move to systems of interest, UNC3524 used a customized version of WMIEXEC, a tool that uses Windows Management Instrumentation to establish a shell on the remote system.
Eventually, Quietexit executes its final objective: accessing email accounts of executives and IT personnel in hopes of obtaining documents related to things like corporate development, mergers and acquisitions, and large financial transactions. . ."
Tuesday, May 03, 2022
DISCLOSURE: Unpatched DNS bug affects millions of routers and IoT devices
Unpatched DNS bug affects millions of routers and IoT devices
- May 3, 2022
- 09:18 AM
- 2
A vulnerability in the domain name system (DNS) component of a popular C standard library that is present in a wide range of IoT products may put millions of devices at DNS poisoning attack risk.
A threat actor can use DNS poisoning or DNS spoofing to redirect the victim to a malicious website hosted at an IP address on a server controlled by the attacker instead of the legitimate location.
The library uClibc and its fork from the OpenWRT team, uClibc-ng. Both variants are widely used by major vendors like Netgear, Axis, and Linksys, as well as Linux distributions suitable for embedded applications.
According to researchers at Nozomi Networks, a fix is not currently available from the developer of the developer of uClibc, leaving products of up to 200 vendors at risk.
Vulnerability details
The uClibc library is a C standard library for embedded systems that offers various resources needed by functions and configuration modes on these devices.
The DNS implementation in that library provides a mechanism for performing DNS-related requests like lookups, translating domain names to IP addresses, etc.
Nozomi reviewed the trace of DNS requests performed by a connected device using the uClibc library and found some peculiarities caused by an internal lookup function.
After investigating further, the analysts discovered that the DNS lookup request's transaction ID was predictable. Because of this, DNS poisoning might be possible under certain circumstances.
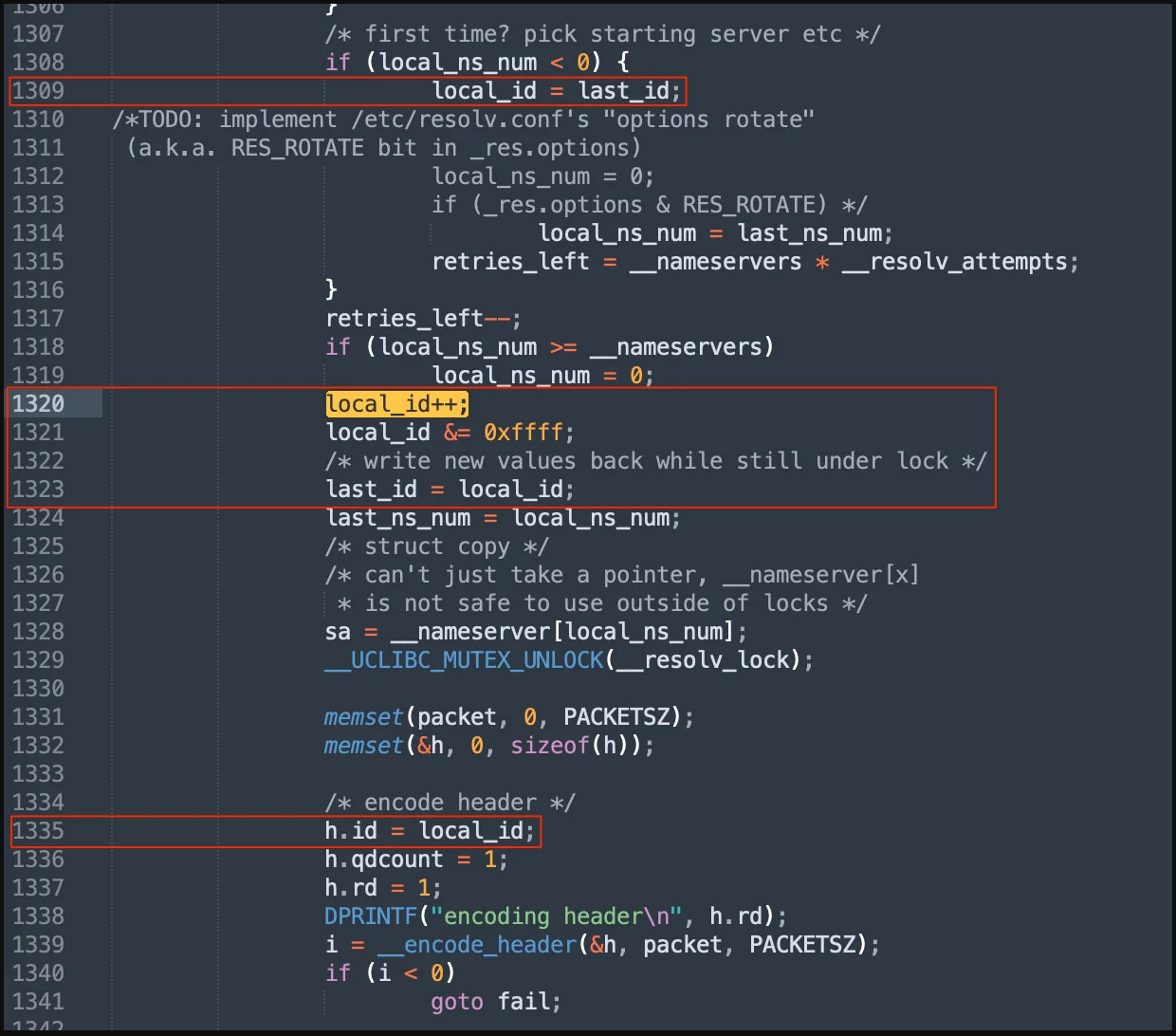
Flaw implications
If the operating system doesn't use source port randomization, or if it does but the attacker is still capable of brute-forcing the 16-bit source port value, a specially-crafted DNS response sent to devices using uClibc could trigger a DNS poisoning attack.
DNS poisoning is practically tricking the target device into pointing to an arbitrarily defined endpoint and engaging in network communications with it.
By doing that, the attacker would be able to reroute the traffic to a server under their direct control.
"The attacker could then steal or manipulate information transmitted by users and perform other attacks against those devices to completely compromise them. The main issue here is how DNS poisoning attacks can force an authenticated response," - Nozomi Networks
Mitigation and fixing
Nozomi discovered the flaw in September 2021 and informed CISA about it. Then, in December, it reported to the CERT Coordination Center, and finally, in January 2022, it disclosed the vulnerability to over 200 potentially impacted vendors.
As mentioned above, there's currently no fix available for the flaw, which is now tracked under ICS-VU-638779 and VU#473698 (no CVE yet).
Currently, all stakeholders are coordinating to develop a viable patch and the community is expected to play a pivotal role in this, as this was precisely the purpose of the disclosure.
As the affected vendors will have to apply the patch by implementing the new uClibc version on firmware updates, it will take a while for the fixes to reach end consumers.
Even then, end-users will have to apply the firmware updates on their devices, which is another choke point that causes delays in fixing critical security flaws.
"Because this vulnerability remains unpatched, for the safety of the community, we cannot disclose the specific devices we tested on," says Nozomi
"We can, however, disclose that they were a range of well-known IoT devices running the latest firmware versions with a high chance of them being deployed throughout all critical infrastructure."
Users of IoT and router devices should keep an eye on new firmware releases from vendors and apply the latest updates as soon as they become available.
Related Articles:
Synology warns of critical Netatalk bugs in multiple products
Magniber ransomware gang now exploits Internet Explorer flaws in attacks
Access:7 vulnerabilities impact medical and IoT devices
Log4j: List of vulnerable products and vendor advisories
Online library app Onleihe faces issues after cyberattack on provider
Zelensky Calls for a European Army as He Slams EU Leaders’ Response
Jan 23, 2026 During the EU Summit yesterday, the EU leaders ...
-
Flash News: Ukraine Intercepts Russian Kh-59 Cruise Missile Using US VAMPIRE Air Defense System Mounted on Boat. Ukrainian forces have made ...

