CISA, the NSA, and MS-ISAC warned today in a joint advisory that attackers are increasingly using legitimate remote monitoring and management (RMM) software for malicious purposes.
More worryingly, CISA discovered malicious activity within the networks of multiple federal civilian executive branch (FCEB) agencies using the EINSTEIN intrusion detection system after the release of a Silent Push report in mid-October 2022.
This activity was linked to the "widespread, financially motivated phishing campaign" reported by Silent Push and was detected on "many other FCEB networks" after first being spotted on a single FCEB network in mid-September 2022.
CISA: Federal agencies hacked using legitimate remote desktop tools
CISA, the NSA, and MS-ISAC warned today in a joint advisory that attackers are increasingly using legitimate remote monitoring and management (RMM) software for malicious purposes.
- January 25, 2023
- 04:18 PM
 0
0
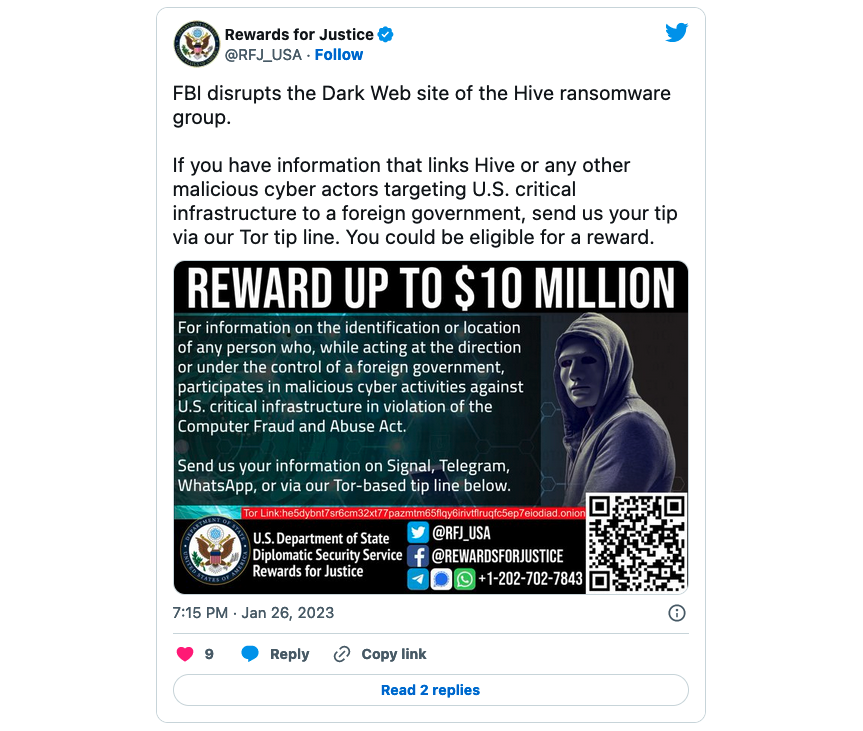
US offers $10M bounty for Hive ransomware links to foreign governments

The U.S. Department of State today offered up to $10 million for information that could help link the Hive ransomware group (or other threat actors) with foreign governments.
In November, the FBI revealed that this ransomware operation had extorted around $100 million from over 1,500 companies since June 2021.
"If you have information that links Hive or any other malicious cyber actors targeting U.S. critical infrastructure to a foreign government, send us your tip via our Tor tip line. You could be eligible for a reward," the State Department's Rewards for Justice Twitter account said.
"For information on the identification or location of any person who, while acting at the direction of a foreign government, participates in malicious cyber activities against U.S. critical infrastructure in violation of the Computer Fraud and Abuse Act."
"Send us your information on Signal, Telegram, WatshApp, or via our Tor-based tip line."
During the last two years, the State Department also offered rewards of up to $15 million for tips that could help locate members of the Conti [1, 2], REvil (Sodinokibi), and Darkside ransomware operations.
The State Department offers these rewards as part of its Transnational Organized Crime Rewards Program (TOCRP), through which over $135 million in rewards have been paid since 1986.
Disrupted after FBI infiltrated Hive's servers
This offer comes after Hive ransomware's Tor websites were seized today as part of an international law enforcement operation.
The Justice Department revealed that the FBI infiltrated Hive servers at a hosting provider in California last July and secretly monitored the operation for six months (Dutch police gained access to backup servers hosted in the Netherlands).
As a result, the FBI could warn targets as it learned about attacks before they occurred and distribute over 1,300 decryption keys to Hive victims, thus saving them at least $130 million in ransom payments.
Besides decryption keys, the FBI also discovered Hive communication records, malware file hashes, and information on 250 Hive affiliates.
The gang's Tor payment and data leak sites now display an animated seizure banner warning other ransomware gangs of this coordinated action and listing the law enforcement organizations and countries involved in this international takedown operation.
"This hidden site has been seized. The Federal Bureau of Investigation seized this site as part of a coordinated law enforcement action taken against Hive Ransomware," the seizure notice reads.
"This action has been taken in coordination with the United States Attorney's Office for the Middle District of Florida and the Computer Crime and Intellectual Property Section of the Department of Justice with substantial assistance from Europol."
-
RCE exploit for vRealize Log Insight coming next week, patch now
Security researchers with Horizon3's Attack Team will release next week an exploit targeting a vulnerability chain for gaining remote code execution on unpatched VMware vRealize Log Insight appliances.
- January 28, 2023
- 11:32 AM
 0
0
-
Hackers use new SwiftSlicer wiper to destroy Windows domains
Security researchers have identified a new data-wiping malware they named SwiftSlicer that aims to overwrite crucial files used by the Windows operating system.
- January 28, 2023
- 10:21 AM
 0
0
-
Learn to be an ethical hacker with this $39.99 course bundle deal
The Ultimate White Hat Hacker Certification Bundle is more than just a random collection of cybersecurity tutorials. The full bundle includes nearly 100 hours of instruction and hands-on exercises, and you can get it now for hundreds off the total MSRP at $39.99.
- January 28, 2023
- 08:27 AM
 0
0
-
The Week in Ransomware - January 27th 2023 - 'We hacked the hackers'
For the most part, this week has been relatively quiet regarding ransomware attacks and researcher — that is, until the FBI announced the disruption of the Hive ransomware operation.
- January 27, 2023
- 07:08 PM
 0
0
-
Massive Microsoft 365 outage caused by WAN router IP change
Microsoft says this week's five-hour-long Microsoft 365 worldwide outage was caused by a router IP address change that led to packet forwarding issues between all other routers in its Wide Area Network (WAN).
- January 27, 2023
- 03:32 PM
 0
0
-
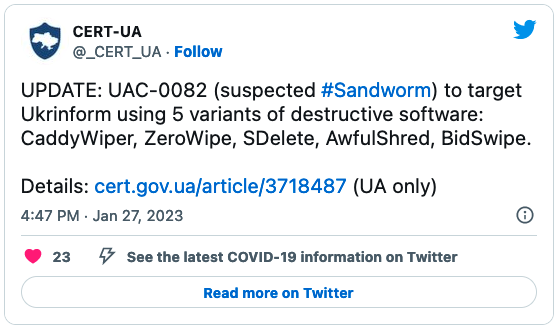
Ukraine: Sandworm hackers hit news agency with 5 data wipers
The Ukrainian Computer Emergency Response Team (CERT-UA) found a cocktail of five different data-wiping malware strains deployed on the network of the country's national news agency (Ukrinform) on January 17th.
- January 27, 2023
- 01:10 PM
 0
0
-
Microsoft fixes Windows 11 issue behind Remote Desktop freezes
Microsoft has addressed a known issue causing Remote Desktop app freezes on Windows 11 systems after installing the Windows 11 2022 Update.
- January 27, 2023
- 11:42 AM
 0
0
-
PlugX malware hides on USB devices to infect new Windows hosts
Security researchers have analyzed a variant of the PlugX malware that can hide malicious files on removable USB devices and then infect the Windows hosts they connect to.
- January 27, 2023
- 11:00 AM
 4
4
-
This refurbished Microsoft Surface deal lets you be productive anywhere
This refurbished Microsoft Surface 3 deal lets you be productive safely from anywhere for $169.99, 71% off the $594 MSRP.
- January 27, 2023
- 07:15 AM
 0
0
-
Microsoft starts force upgrading Windows 11 21H2 devices
Microsoft has started the forced rollout of Windows 11 22H2 to systems running Windows 11 21H2 that are approaching their end-of-support (EOS) date on October 10, 2023.
- January 26, 2023
- 07:08 PM
 11
11
-
Windows 11 KB5022360 preview update released with 15 improvements
Microsoft has released the Windows 11 22H2 KB5022360 preview cumulative update with fifteen fixes or improvements.
- January 26, 2023
- 07:05 PM
 0
0
-
Microsoft urges admins to patch on-premises Exchange servers
Microsoft urged customers today to keep their on-premises Exchange servers patched by applying the latest supported Cumulative Update (CU) to have them always ready to deploy an emergency security update.
- January 26, 2023
- 06:02 PM
 2
2
-
Bitwarden password vaults targeted in Google ads phishing attack
Bitwarden and other password managers are being targeted in Google ads phishing campaigns to steal users' password vault credentials.
- January 26, 2023
- 04:40 PM
 12
12


.webp)














.jpg)


.jpg)

.jpg)
.jpg)
.jpg)
.jpg)