55m ago
Podcast: Has Ukraine’s counter offensive begun?

Follow on Apple, Google or Spotify. Listen on the Reuters app. Read the episode transcript.
Russia says it’s thwarted a major Ukrainian attack in the Donetsk region – is this the long-promised counter-offensive?
Ukrainian counteroffensive attempt failed – Russian MOD

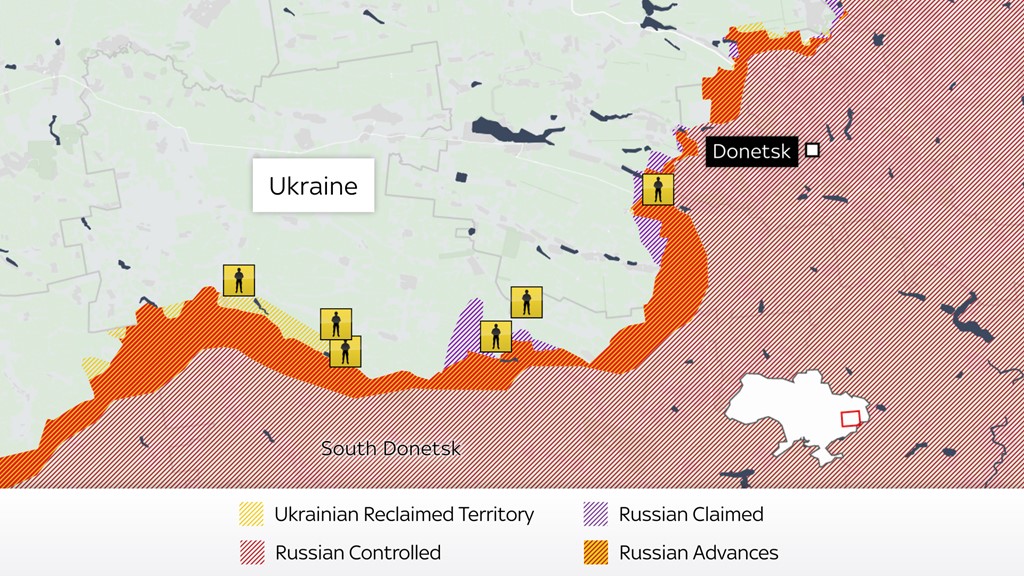
"Ukrainian forces attempted to mount a large-scale offensive in the southern part of the Donetsk People’s Republic, Russia's Defense Ministry claimed on Monday.
In a statement, the ministry said that on Sunday, Ukrainian troops attempted to attack Russian forces using six mechanized and two tank battalions. However, it added that as a result of the actions of the ‘East’ military grouping, as well as owing to air strikes and artillery fire near the settlements of Neskuchnoye and Novodarovka, both of which are some 100km west of Donetsk, the Ukrainian forces incurred “significant losses.”
As a result of the botched attack, in the last 24 hours Ukraine has lost up to 300 service members, 16 tanks, 26 armored and 14 ordinary vehicles, the statement read. “The enemy failed to accomplish its goals,” the ministry concluded.
The ministry’s statement comes after earlier in the day it said that Ukraine had tried to break through Russian defenses in five sections of the front line in Donbass using its “strategic reserves,” but failed to do so.
Ukrainian officials have for months promised to launch a counteroffensive, which initially was expected to happen in spring. Ukrainian President Vladimir Zelensky has on numerous occasions said that Kiev was “ready” for the push but “still needs a bit more time” in order to receive more Western weapons.
- Ukraine’s General Staff provided no comment on the counteroffensive, saying only that there had been 29 combat clashes in the Donetsk and neighboring Lugansk Regions in the last 24 hours.
- Ukraine’s Centre for Strategic Communications also failed to address Moscow’s statement head-on, but accused Russia of attempting to “spread false information” in order to demoralize Ukrainians.
>