Ah-ha --- so were detected + here we go again!
SpringShell attacks target about one in six vulnerable orgs
Roughly one out of six organizations worldwide that are impacted by the Spring4Shell zero-day vulnerability have already been targeted by threat actors, according to statistics from one cybersecurity company.
The exploitation attempts took place in the first four days since the disclosure of the severe remote code execution (RCE) flaw, tracked as CVE-2022-22965, and the associated exploit code.
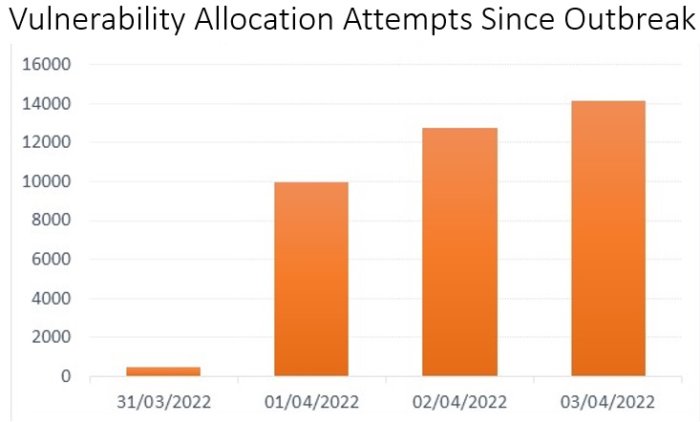
According to Check Point, who compiled the report based on their telemetry data, 37,000 Spring4Shell attacks were detected over the past weekend alone.
The most impacted industry appears to be software vendors, accounting for 28% of the total, potentially due to being excellent candidates for supply chain attacks.
As for the most targeted region, Check Point ranks Europe first with 20%, based on their visibility.
This indicates that the malicious effort to take advantage of existing RCE opportunities against vulnerable systems is well underway, and threat actors appear to be shifting to Spring4Shell while they can still take advantage of unpatched systems.
Exploit signs in the U.S.
North America accounts for 11% of Check Point’s detected Spring4Shell attacks, and confirmations of active exploitation in the U.S. come from other entities too.
Yesterday, the U.S. Cybersecurity & Infrastructure Security Agency (CISA) added four vulnerabilities to its catalog of flaws known to be leveraged in actual attacks, one of them being Spring4Shell.
More specifically, the agency has seen evidence of attacks targeting VMware products, for which the software vendor released security updates and advisories yesterday.
Microsoft also published guidance for detecting and protecting against Spring4Shell attacks and noted that they are already tracking exploitation attempts.
"Since the Spring Core vulnerability was announced, we have been tracking a low volume of exploit attempts across our cloud services for Spring Cloud and Spring Core vulnerabilities," Microsoft said.
Protect against Spring4Shell attacks
CVE-2022-22965 impacts Spring MVC and Spring WebFlux apps running on JDK 9+, so all Java Spring deployments should be considered as potential attack vectors.
The vendor has released Spring Framework versions 5.3.18 and 5.2.2, as well as Spring Boot 2.5.12, which successfully address the RCE problem. Therefore, there is a strong recommendation to upgrade to these versions or later.
Moreover, system admins should also consider the CVE-2022-22963 and CVE-2022-22947 remote code execution flaws in the Spring Cloud Function and Spring Cloud Gateway. Proof of concept exploits for these flaws already exist and are publicly available."



No comments:
Post a Comment