US govt grants academics $12M to develop cyberattack defense tools

"The US Department of Energy (DOE) has announced that it will provide $12 million in funding to six university teams to develop defense and mitigation tools to protect US energy delivery systems from cyberattacks.
Cybersecurity tools developed as a result of the six university-led research, development, and demonstration (RD&D) projects will focus on detecting, blocking, and mitigating attempts to compromise critical controls within the US power grid.
The teams behind these RD&D projects funded by the US government will also work on innovative technology that will enable energy delivery systems to survive and recover quickly following cyberattacks.
"DOE's Office of Cybersecurity, Energy Security, and Emergency Response (CESER) will fund six university teams to perform cybersecurity RD&D to advance anomaly detection, artificial intelligence and machine learning, and physics-based analytics to strengthen the security of next-generation energy systems," DOE said.
"These systems include components placed in substations to detect cyber intrusions more quickly and automatically block access to control functions."
The complete list of university teams and projects funded by DOE CESER includes:
- Florida International University: artificial intelligence (AI)-based detection tools and design effective cyber threat mitigation strategies using these technologies.
- Iowa State University: defense-in-depth security and resilience for cyber-physical systems using AI-integrated, attack-resilient, and proactive system technologies and solutions.
- New York University: a program called Tracking Real-time Anomalies in Power Systems (TRAPS) to detect and localize anomalies in power grid cyber-physical systems.
- Texas A&M Engineering Experiment Station: will leverage AI and machine learning to develop techniques and scalable prototypes for intrusion response against advanced cyber-physical threats to power systems.
- University of Illinois at Chicago: a resilient, next-generation solid-state power substation, integrating cybersecurity considerations to improve adoptability.
- Virginia Polytechnic Institute and State University: a program called Cyber REsilience of SubsTations (CREST), a two-part system to detect and mitigate cyber incidents while maintaining secure communication and critical functions.
DOE's announcement comes after two joint advisories from the US government in January and from Five Eyes nations on Wednesday, warning of an increased risk that Russian-backed hacking groups could target critical infrastructure organizations worldwide.
> The FBI also revealed in its Internet Crime Complaint Center (IC3) 2021 Internet Crime Report that ransomware gangs breached at least 649 organizations from multiple US critical infrastructure sectors last year.
Since the start of the year, the FBI has issued other alerts highlighting how ransomware gangs, including BlackByte, Ragnar Locker, and Avoslocker, targeted and hacked dozens of critical infrastructure organizations across the United States.
> Earlier in April, a joint cybersecurity advisory from CISA, NSA, FBI, and the Department of Energy (DOE) also warned of government-sponsored hacking groups using a new ICS-focused malware toolkit (tracked as PIPEDREAM or INCONTROLLER) to hijack industrial control system (ICS) and supervisory control and data acquisition (SCADA) devices.
> The FBI, CISA, and the NSA advised US critical infrastructure orgs to focus on detecting their malicious activity by enforcing robust log collection/retention and monitoring them for behavioral evidence or network and host-based artifacts."
================================================================
Chinese hackers behind most zero-day exploits during 2021

Threat analysts report that zero-day vulnerability exploitation is on the rise, with Chinese hackers using most of them in attacks last year.
Zero-day vulnerabilities are security weaknesses in software products that are either unknown or have not been fixed at the time of discovery
Zero-day disclosures are of particular interest to hackers because they have a wider exploitation window until vendors address the flaws and clients start applying the updates.
Typically, this window of opportunity lasts for at least a couple of days, and since not all admins apply security updates immediately, the number of vulnerable targets remains high for a while.
2021 zero-day landscape
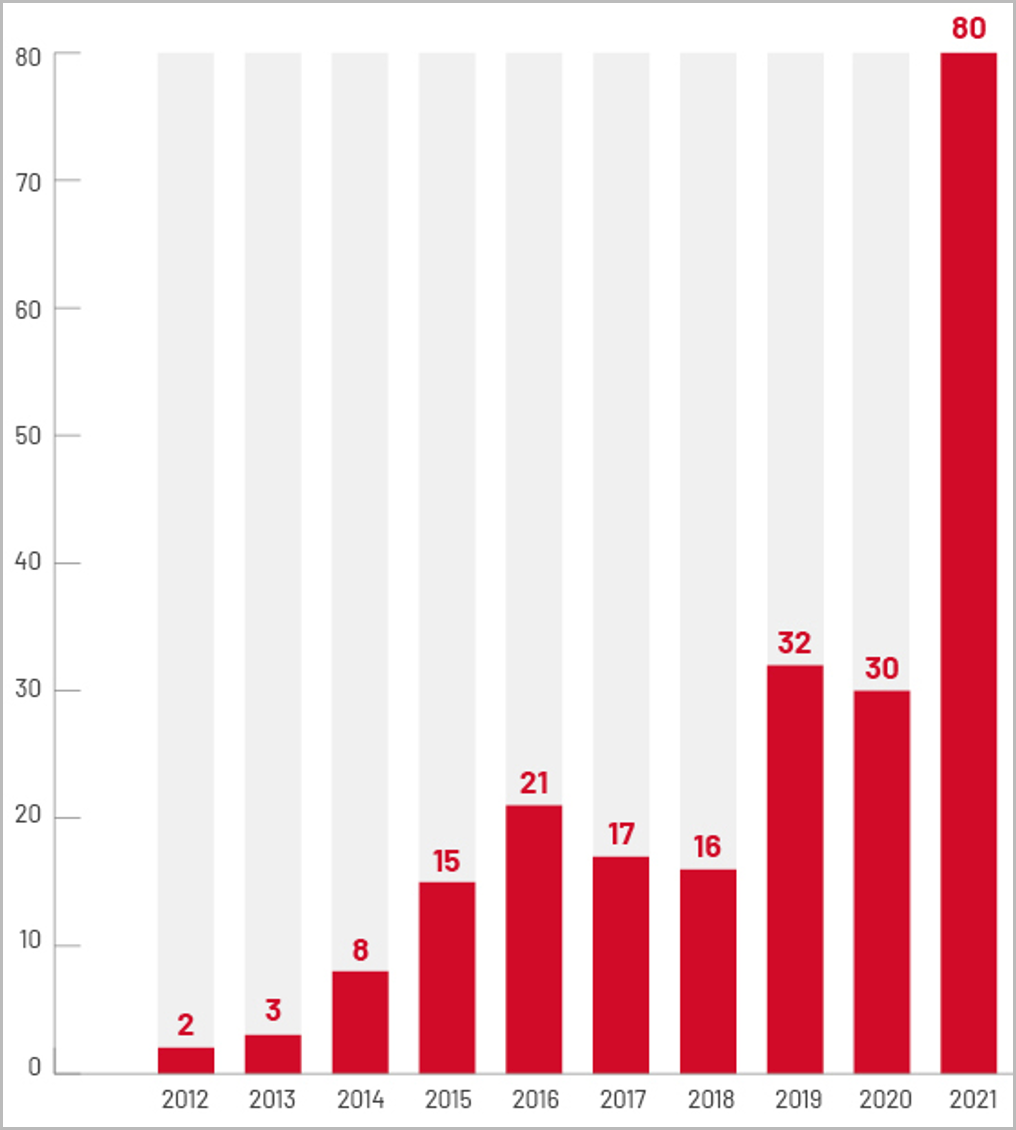
According to an analysis from cybersecurity firm Mandiant, last year there were 80 cases of zero-days exploited in the wild, 18 more than 2020 and 2019 combined.
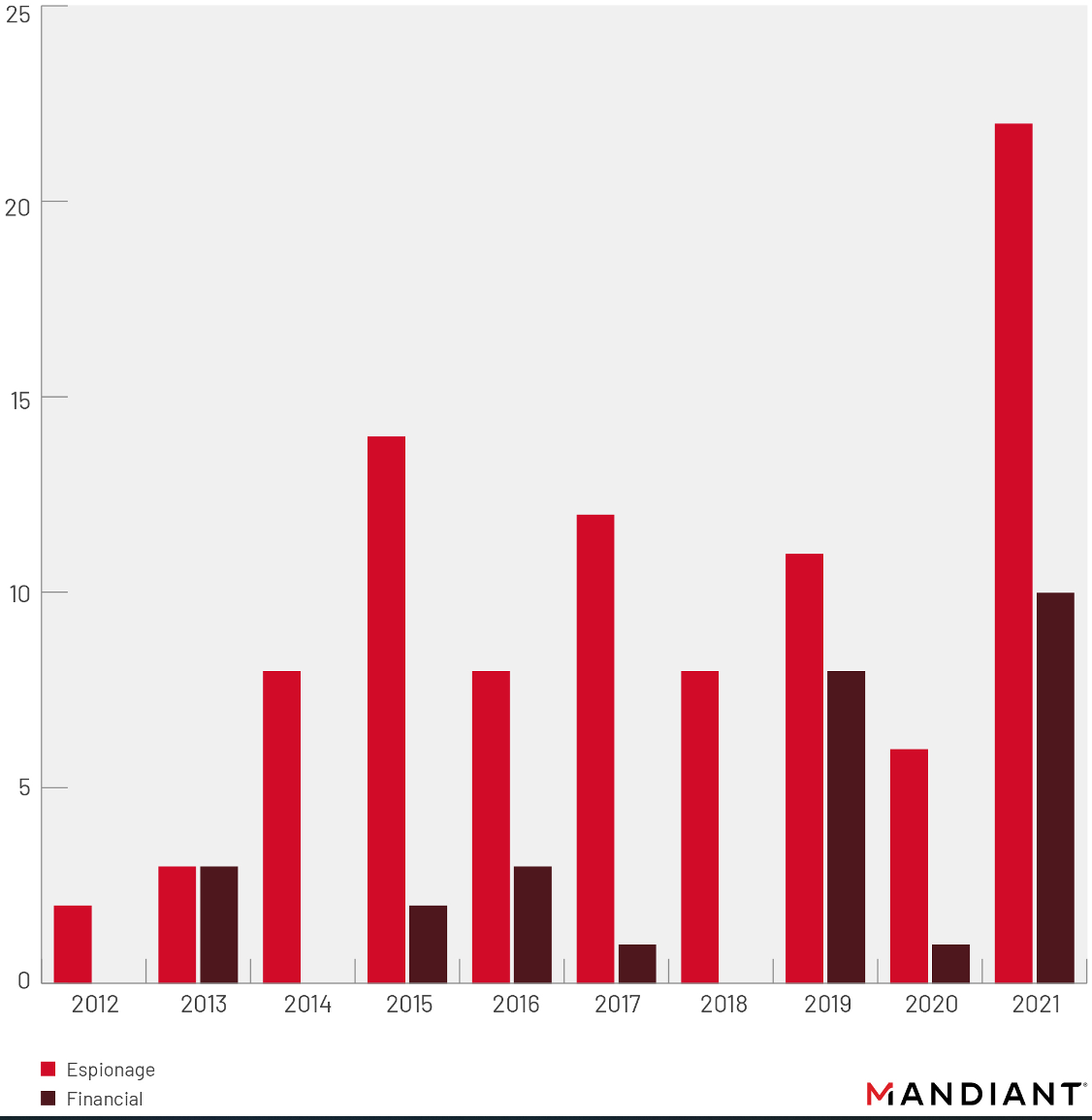
Most of them were attributed to cyberespionage operations from state-backed actors.
However, the company found that one out of three malicious actors exploiting zero-day vulnerabilities was financially motivated, a statistic that continues a growing trend from previous years.
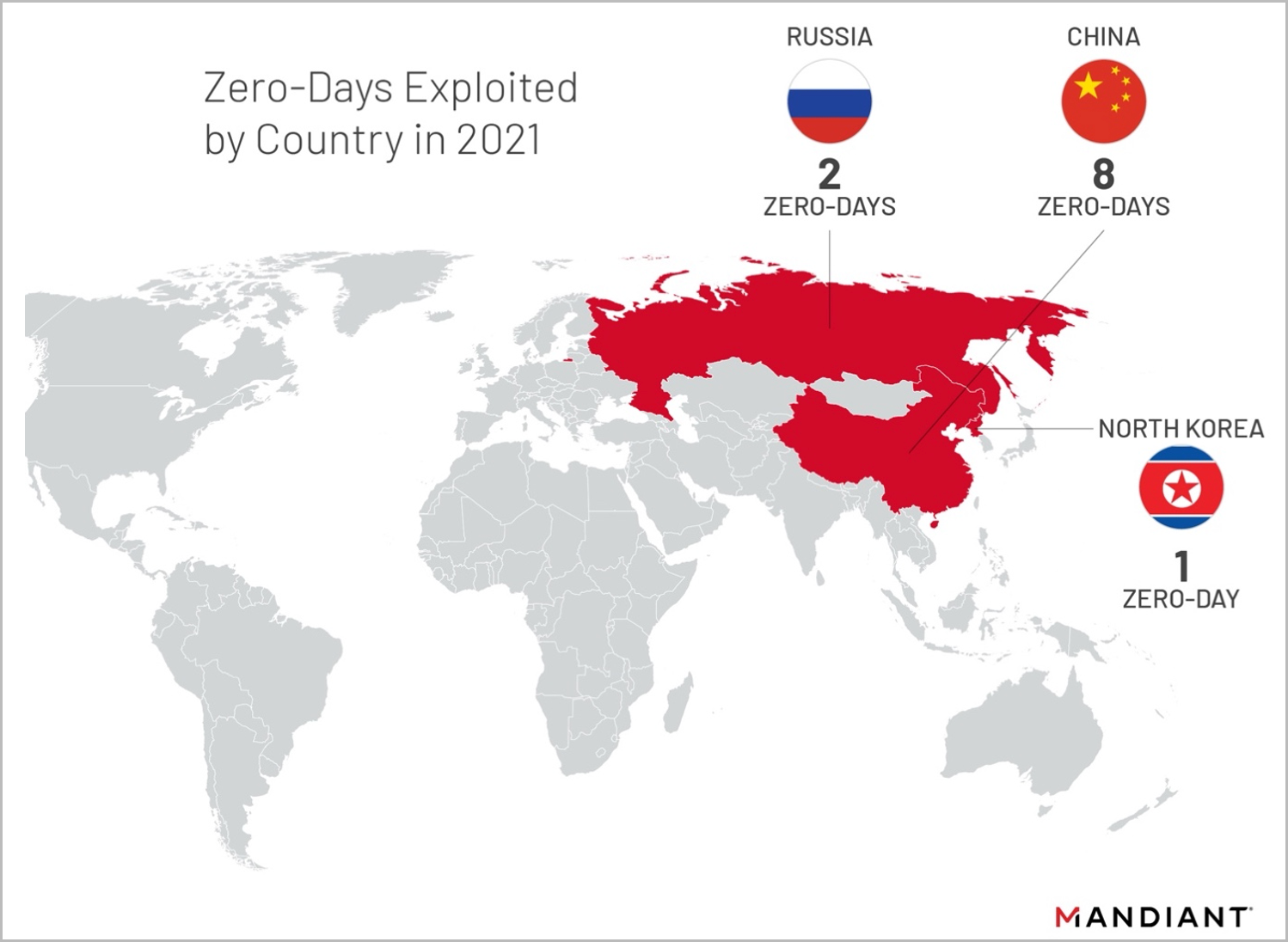
In terms of threat actors, China tops the list with eight zero-days used in cyberattacks in 2021, followed by Russia which used two, and North Korea with one.
The most notable case was that of Hafnium, a Chinese state-sponsored hacking group that utilized four zero-day vulnerabilities on the Microsoft Exchange servers to access email communications of Western organizations.
Mandiant also recorded an uptick in ransomware operatives exploiting zero-day flaws to breach networks and deploy their file-encrypting payloads.
One prominent example of this activity was that of HelloKitty ransomware operators, who exploited a zero-day bug in SonicWall SMA 100 VPN appliances.
The most targeted vendors in 2021 zero-day attacks were Microsoft, Apple, and Google, accounting for over 75% of all attacks.
As BleepingComputer reported recently, the number of mobile OS zero-days targeting Android and iOS is also on an ascending trend, going from under five in 2019 and 2020 to 17 in 2021.
.png)
What to expect in 2022
Last year saw a record break in zero-day exploitation, and current evidence indicates that it will be worse this year.
“We suggest that significant campaigns based on zero-day exploitation are increasingly accessible to a wider variety of state-sponsored and financially motivated actors, including as a result of the proliferation of vendors selling exploits and sophisticated ransomware operations potentially developing custom exploits” - Mandiant
PLEASE NOTE: Google’s Project Zero team on Tuesday published a report on the same topic, underlining that the rise in zero-day exploitation is partly a result of greater visibility and detection and not necessarily an increase of activity or attacks' complexity.
As the report details, only two out of 58 new zero-days Project Zero disclosed in 2021 exhibit technical excellence and uniqueness, which could point to software security maturity."
=========================================================================
Related Articles:
'Hack DHS' bug hunters find 122 security flaws in DHS systems
FBI: BlackCat ransomware breached at least 60 entities worldwide
FBI warns of ransomware attacks targeting US agriculture sector
US and allies warn of Russian hacking threat to critical infrastructure
US warns of Lazarus hackers using malicious cryptocurrency apps


No comments:
Post a Comment