
Aljazeera News|Business and Economy
Karzai: Biden order on frozen funds ‘atrocity against Afghans’
President Biden signed an order to free $7.1bn in Afghan assets to be divided between 9/11 victims and humanitarian aid to Afghans
![<div class=__reading__mode__extracted__imagecaption>Former Afghan leader Karzai called on President Joe Biden to rescind last week's order [Pablo Martinez Monsivais/AP Photo]](https://www.aljazeera.com/wp-content/uploads/2017/11/77f8641e3d924c75b06d7c0c9f84e6d4_18.jpeg?resize=770%2C513)

LEILA FADEL, HOST:
There are about $7 billion of Afghan funds from the country's central bank frozen in the United States. Afghanistan's economy is on the verge of collapse. Inflation is soaring, and millions of Afghans are on the brink of starvation. So what's happening with that money?
On Friday, President Biden signed an executive order that would seize the Afghan assets and move half to a fund designated for humanitarian aid for Afghanistan. The administration nodded to legal wranglings with some 9/11 families pursuing claims against those assets as the reason for not trying to free the other half of Afghan funds for the Afghan people. And that decision - well, it sparked outrage.
Naser Shahalemi is the founder of an Afghan advocacy organization called End Afghan Starvation. It's been fighting to free those funds. He joins me now. Good morning.
[...]
FADEL: So, Naser, what was your reaction to this announcement last week?
SHAHALEMI: Well, initially there was a deep amount of shock initially as we were waiting to see what would happen with the frozen funds and what the course of action was going to be from the White House. We were dismayed. We were shocked. We were appalled. We were in complete awe of what the decision was, and we hope that a better decision can come about this and this decision could get rescinded at some level.
FADEL: What would you say to the Biden administration, which is saying that this is its way of getting at least some of the money to Afghanistan?
SHAHALEMI: Yeah. I mean, the way that they divided this money was absolutely illogical because first we need to decipher who has the right to decide another country's national assets and federal reserve. The United States spent 20 years developing the federal reserve with Afghanistan, and then to, you know, dismantle it and leave it in a paralyzed state is not very copacetic for the future of Afghanistan or the economic growth of Afghanistan.
FADEL: Give us a sense of the humanitarian situation in Afghanistan right now, nearly six months since the U.S. withdrawal.
SHAHALEMI: Yeah, the humanitarian situation is horrific at this point. The majority of the people of Afghanistan are starving, and they are locked out of their funds. They cannot access their bank cards. They cannot access their bank accounts. Many of them are in a position where - that they shouldn't need to be because they do have money in the banks.
FADEL: Yeah.
SHAHALEMI: They do have the ability to take care of themselves. But because of the sanctions, they've been locked away from their own money. And if that happened in America, people would be in outrage.
FADEL: And the sanctions you refer to are the sanctions on the Taliban, which is now in control of the country. What do you say to people who say, well, if this money goes back to Afghanistan, it will just go into the hands of the Taliban?
SHAHALEMI: It's not really how it works. Ultimately, this money that was in the federal reserve of Afghanistan's central bank was there to bolster the afghani note and to keep it steady. The money is - that money is hard-earned taxpayer Afghan money that was collected over 20 years...
FADEL: We saw demonstrations over the weekend condemning this move from the administration. What were the hopes for these funds?
SHAHALEMI: The hope for these funds was that it would be returned to the people of Afghanistan and that they would be allowed to use it for economic purposes, for business, day-to-day businesses.
Aljazeera News|Business and Economy
President Biden signed an order to free $7.1bn in Afghan assets to be divided between 9/11 victims and humanitarian aid to Afghans
![<div class=__reading__mode__extracted__imagecaption>Former Afghan leader Karzai called on President Joe Biden to rescind last week's order [Pablo Martinez Monsivais/AP Photo]](https://www.aljazeera.com/wp-content/uploads/2017/11/77f8641e3d924c75b06d7c0c9f84e6d4_18.jpeg?resize=770%2C513)
14 Feb 2022
"Former Afghanistan President Hamid Karzai has called a White House order to unfreeze $3.5bn in Afghan assets held in the United States for families of 9/11 victims an atrocity against the Afghan people.
Karzai, at a packed news conference, sought the help of Americans, particularly the families of the thousands killed in the September 11, 2001, attacks on the United States, to press President Joe Biden to rescind last week’s order.
“The people of Afghanistan share the pain of the American people, share the pain of the families and loved ones of those who died, who lost their lives in the tragedy of September 11,” said Karzai.
“We commiserate with them [but] Afghan people are as much victims as those families who lost their lives. Withholding money or seizing money from the people of Afghanistan in their name is unjust and unfair and an atrocity against Afghan people.”
President Biden’s order, signed last Friday, freed $7.1bn in Afghan assets currently held in the US, to be divided between September 11 victims and humanitarian aid to Afghans. . .[ ]
The $3.5bn was set aside for a US court to decide whether it can be used to settle claims by families of 9/11 victims.
US courts would also have to sign off before the release of humanitarian assistance money.
We “ask the US courts to do the opposite, to return the Afghan money back to the Afghan people”, said Karzai. . ."
OK so let's see what they said

"The US Federal Bureau of Investigation (FBI) revealed that the BlackByte ransomware group has breached the networks of at least three organizations from US critical infrastructure sectors in the last three months.
This was disclosed in a TLP:WHITE joint cybersecurity advisory released Friday in coordination with the US Secret Service.
"As of November 2021, BlackByte ransomware had compromised multiple US and foreign businesses, including entities in at least three US critical infrastructure sectors (government facilities, financial, and food & agriculture).," the federal law enforcement agency said [PDF].
"BlackByte is a Ransomware as a Service (RaaS) group that encrypts files on compromised Windows host systems, including physical and virtual servers."
The advisory focuses on providing indicators of compromise (IOCs) that organizations can use to detect and defend against BlackByte's attacks.
The IOCs associated with BlackByte activity shared in the advisory include MD5 hashes of suspicious ASPX files discovered on compromised Microsoft Internet Information Services (IIS) servers and a list of commands the ransomware operators used during attacks.
In related news, NFL's San Francisco 49ers team revealed over the weekend that it's recovering from a BlackByte ransomware attack.
The threat actors claimed the attack, saying that they also stole data from the football org's servers during the incident and leaked almost 300MB worth of files on their data leak blog.
The 49ers confirmed the ransomware attack in a statement to BleepingComputer and said it only caused a temporary disruption to portions of its IT network.
BlackByte ransomware operation has been active since at least July 2021, when it started targeting corporate victims worldwide.
This gang is known for exploiting software vulnerabilities (including Microsoft Exchange Server) to gain initial access to their enterprise targets' network, illustrating that keeping your servers updated will most likely block their attacks.
In October, cybersecurity firm Trustwave created and released a free BlackByte decryptor, enabling some victims to restore their files for free after the ransomware gang used the same decryption/encryption key in multiple attacks.
The two agencies also shared a list of measures that can help admins mitigate BlackByte attacks:
US govt warns of Russian hackers targeting critical infrastructure
CISA warns critical infrastructure to stay vigilant for ongoing threats
FBI warns of fake job postings used to steal money, personal info
FBI warns of malicious QR codes used to steal your money
NFL's San Francisco 49ers hit by Blackbyte ransomware attack
OTHER RELATED CONTENT

Ransomware attacks impact organizations every single day. But it doesn’t always have to be bad news. Victims of BlackByte ransomware can now decrypt and get back their files as a free decryption tool has just been made public this week.
In this blog post you will find information about the ransomware group BlackByte, which has victims in many countries, and how to use the latest released decryptor.
Who is BlackByte?BlackByte is a ransomware operation that began targeting corporate victims worldwide in July 2021. The first findings regarding this group emerged after victims sought help decrypting their files.
In C#, BlackByte attempts to terminate numerous security, mail server, and database processes to encrypt a device successfully. The BlackByte ransomware group disables Microsoft Defender on target devices before attempting encryption.
According to the information reported so far, BlackByte was not as active as other ransomware operations, but the researchers’ eyes were on it. . .
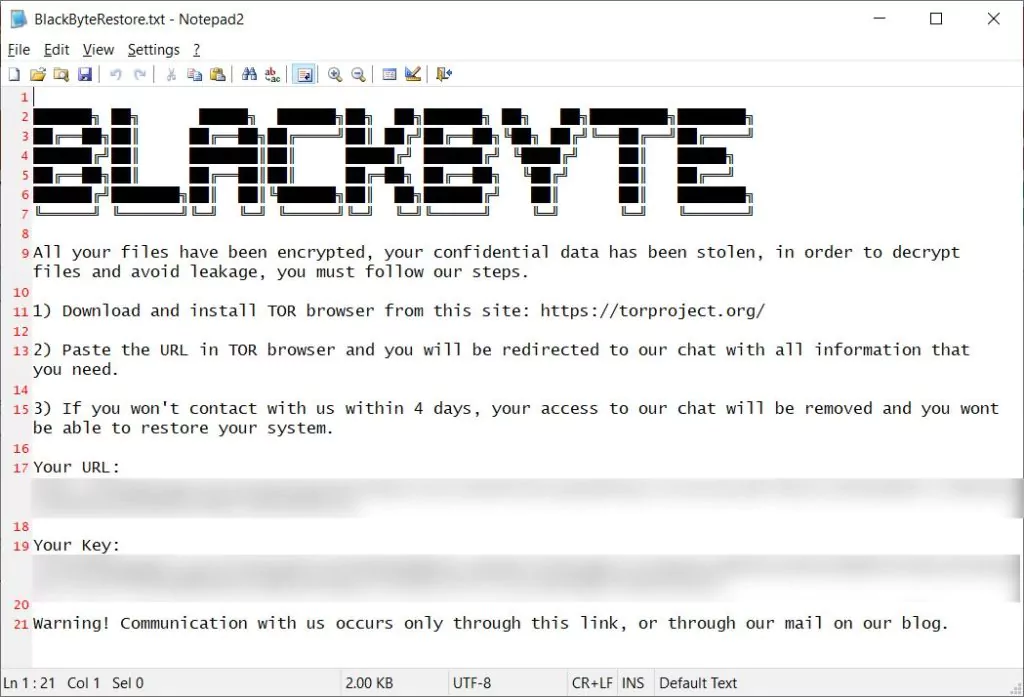
According to information obtained by SOCRadar, the BlackByte ransomware group has so far attacked companies in the manufacturing, mining, food, beverage, healthcare, and construction sectors from the USA, France, Australia, Italy, Austria, Croatia, Chile, and Turkey.
Playing a sheriff

By |February 14th, 2022|AZ Elections, AZ Politics
"Retired energy industry executive Jim Lamon is banking that Super Bowl fans this weekend will be inspired to cast votes for him at the polls in August.
Lamon is a former CEO for DEPCOM, a Scottsdale-based utility-scale solar company that has grown to several hundred workers over the years. Before that, Lamon worked in the coal and natural gas-fired power plant industry.
The Republican who lives in Fountain Hills is gunning for a seat in the U.S. Senate, seeking to oust the incumbent Democratic Senator Mark Kelly.
> Lamon is among several prominent Republicans who submitted false information trying to certify Arizona’s November 2020 election results in favor of Donald Trump. He even bankrolled efforts related to the election audit security detail and has bragged about pushing Karen Fann, a key Republican state senator to move forward with the partisan election “fraudit” in Maricopa County.
Lamon is using political theater for attention with a polarizing 30-second long campaign ad that NBC will show Arizonans watching the Super Bowl. The advertisement package cost the campaign “upwards of six figures,” according to the campaign’s manager Stephen Puetz.
[The ad ran on] Tucson’s NBC station [KVOA 4] on Sunday during the football game and then will be broadcast statewide on Sunday night.
Curious that the KVOA web page does not have a story about this controversial ad.
But Lamon is already being shot down by critics on social media, some of whom he was hoping would become his constituents.
In the advertisement, Lamon is the sheriff and hero on the set of a “spaghetti western-style” movie scene where he pursues a gun battle with top-ranking Democrats, including Mark Kelly.
One local political campaign executive criticized the advertisement for missing the mark with voters.
“It’s embarrassing, desperate, and cringeworthy all in one,” Barrett Marson, a long-time bipartisan campaign strategist in Phoenix, told Phoenix New Times.
Super Bowl fans might catch just a half-minute glimpse of the advertisement between plays. Avid supporters and critics alike may watch the 70-second-long clip campaign organizers described as the “directors cut” afterward.
Lamon garnered $600,000 of individual donations for his campaign, upwards of $10 million from his own coffers, and has spent $1 million each month since his bid for office began.
The Super Bowl ad is one of his biggest investments so far.
“The only candidates with the resources to afford Super Bowl ads are statewide campaigns,” said Ben Petersen, the Republican National Convention’s Arizona representative.
It was not immediately clear if any other state-level office campaigns in Arizona — eight in all — are running an advertisement during the Super Bowl.
Lamon promised to spend $50 million by Election Day.
His campaign manager, Puetz, called Lamon’s commercial a “one-of-a-kind campaign ad.”
The Lamon campaign has spent nearly $1 million on TV advertisements each month.
Last month, Yahoo rejected a different video ad campaign, calling it “overly inflammatory and offensive.” That commercial featured the emergent GOP slogan, “Let’s Go, Brandon,” a play on “Fuck Joe Biden.”
In the ad, Lamon plays himself as “Big Jim Lamon,” the altruistic Wild West sheriff who saves the good people of Arizona from the unholy Washington D.C. Gang in a Hollywood-esque quick-draw duel.
The U.S.-Mexico border security debate is center stage. . ."
And what are the most important things Americans should understand about Iran-Contra?
Richard Cheney - the vice president - played a prominent part as a member of the joint congressional Iran-Contra inquiry of 1986, taking the position that Congress deserved major blame for interfering with Executive privilege
Robert M. Gates - President Bush's nominee to succeed Donald Rumsfeld - was accused of knowing more about Iran-Contra while it was underway than he admitted once the scandal broke. He was forced to give up his chance to head the CIA in early 1987 because of suspicions about his role but managed to attain the position when he was re-nominated in 1991.
John Negroponte - appointed U.N. representative from 2001-2004,rambassador to Iraq in 2004 and director of national intelligence in 2005 - was the career diplomat who increased the U.S. military and intelligence presence in Central America as ambassador to Honduras, as well as participated in efforts to get the Honduran government to support the Contras after Congress banned direct U.S. aid to the rebels...
Elliott Abrams (former consulting attorney to Reagan) became director of the Office for Democracy, Human Rights and International Operations at the National Security Council - a White House position which is not subject to Senate confirmation. Abrams was convicted of lying to Congress about the Iran-Contra affair, but was later pardoned by Bush's father in 1992.
Perhaps more important is that no one involved in the highest ranks of the presidential administrations was held accountable. Bush was elected president while Abrams and other scandal vets were rewarded with prominent posts in the next Republican administration of George W. Bush."
Reference: http://gorhistory.com/hist111/irancontra.html

Valentine's Day is a time to celebrate romance and love and kissy-face fealty. But the origins of this festival of candy and cupids are actually dark, bloody — and a bit muddled.
Though no one has pinpointed the exact origin of the holiday, one place to start is ancient Rome.
From Feb. 13 to 15, the Romans celebrated the feast of Lupercalia. The men sacrificed a goat and a dog, then whipped women with the hides of the animals they had just slain.
The Roman romantics "were drunk. They were naked," Noel Lenski, now a religious studies professor at Yale, told NPR in 2011. Young women would actually line up for the men to hit them, Lenski said. They believed this would make them fertile.
The brutal fete included a matchmaking lottery, in which young men drew the names of women from a jar. The couple would then be, um, coupled up for the duration of the festival — or longer, if the match was right.
The ancient Romans may also be responsible for the name of our modern day of love. Emperor Claudius II executed two men both named Valentine — on Feb. 14 of different years in the 3rd century A.D. Their martyrdom was honored by the Catholic Church with the celebration of St. Valentine's Day.

Later, Pope Gelasius I muddled things in the 5th century by combining St. Valentine's Day with Lupercalia to expel the pagan rituals. But the festival was more of a theatrical interpretation of what it had once been. Lenski added, "It was a little more of a drunken revel, but the Christians put clothes back on it. That didn't stop it from being a day of fertility and love."
Around the same time, the Normans celebrated Galatin's Day. Galatin meant "lover of women." That was likely confused with St. Valentine's Day at some point, in part because they sound alike.
As the years went on, the holiday grew sweeter. Chaucer and Shakespeare romanticized it in their work, and it gained popularity throughout Britain and the rest of Europe. Handmade paper cards became the tokens-du-jour in the Middle Ages.
Eventually, the tradition made its way to the New World. The industrial revolution ushered in factory-made cards in the 19th century. And in 1913, Hallmark Cards of Kansas City, Mo., began mass producing valentines. February has not been the same since.
Today, the holiday is big business. But that commercialization has spoiled the day for many. Helen Fisher, a sociologist at Rutgers University, said we have only ourselves to blame.
"This isn't a command performance," she said. "If people didn't want to buy Hallmark cards, they would not be bought, and Hallmark would go out of business."
And so the celebration of Valentine's Day goes on, in varied ways. Many will break the bank buying jewelry and flowers for their beloveds. Some will celebrate in a SAD (that's Single Awareness Day) way, dining alone and binging on self-gifted chocolates — while others find a way to make peace with singlehood in a society that wants everyone to partner up."
In 2021, cybersecurity authorities in the United States,[1][2][3] Australia,[4] and the United Kingdom[5] observed an increase in sophisticated, high-impact ransomware incidents against critical infrastructure organizations globally. The Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the National Security Agency (NSA) observed incidents involving ransomware against 14 of the 16 U.S. critical infrastructure sectors, including the Defense Industrial Base, Emergency Services, Food and Agriculture, Government Facilities, and Information Technology Sectors. The Australian Cyber Security Centre (ACSC) observed continued ransomware targeting of Australian critical infrastructure entities, including in the Healthcare and Medical, Financial Services and Markets, Higher Education and Research, and Energy Sectors. The United Kingdom’s National Cyber Security Centre (NCSC-UK) recognizes ransomware as the biggest cyber threat facing the United Kingdom. Education is one of the top UK sectors targeted by ransomware actors, but the NCSC-UK has also seen attacks targeting businesses, charities, the legal profession, and public services in the Local Government and Health Sectors.
2
Sure enough, we updated our ransomware numbers a few times throughout 2021, reflecting new payments we hadn’t identified previously. As of January 2022, we’ve now identified just over $692 million in 2020 ransomware payments — nearly double the amount we initially identified at the time of writing last year’s report.

After the Maze ransomware operation began shutting down in October 2020, it was always hoped that they would publicly release decryption keys to allow remaining victims to recover their files.
Tuesday night, almost fourteen months later, the alleged ransomware developer released the decryption keys in a BleepingComputer forum post.
While the developer says they had always planned to publish the keys, it is generally believed that they did it now as a gesture of goodwill due to the recent arrests and server seizures.
Using these keys, cybersecurity firm Emsisoft created a decryptor allowing victims to recover their files for free.
The other big news is the sentencing of a Netwalker ransomware affiliate from Canada, who obtained more than $27.6 million by attacking companies worldwide. After pleading guilty, the affiliate was sentenced to six years and eight months in prison.
This week's other interesting ransomware news includes publishing LockBit 2.0 ransomware technical details by the FBI, a free decryptor for the TargetCompany ransomware, and Puma announcing a data breach due to the Kronos ransomware attack.
Contributors and those who provided new ransomware information and stories this week include: @Seifreed, @billtoulas, @malwareforme, @VK_Intel, @BleepinComputer, @FourOctets, @DanielGallagher, @serghei, @malwrhunterteam, @jorntvdw, @fwosar, @Ionut_Ilascu, @PolarToffee, @LawrenceAbrams, @demonslay335, @struppigel, @chainalysis, @emsisoft, @Avast, @LadislavZezula, @coveware, @ddd1ms, @BrettCallow, @pcrisk, @USCERT_gov, and @CISAgov.
The Black Cat ransomware gang, also known as ALPHV, has confirmed they are former members of the notorious BlackMatter/DarkSide ransomware operation.
The Federal Bureau of Investigation (FBI) has released technical details and indicators of compromise associated with LockBit ransomware attacks in a new flash alert published this Friday.
The numerous law enforcement operations leading to the arrests and takedown of ransomware operations in 2021 have forced threat actors to narrow their targeting scope and maximize the efficiency of their operations.