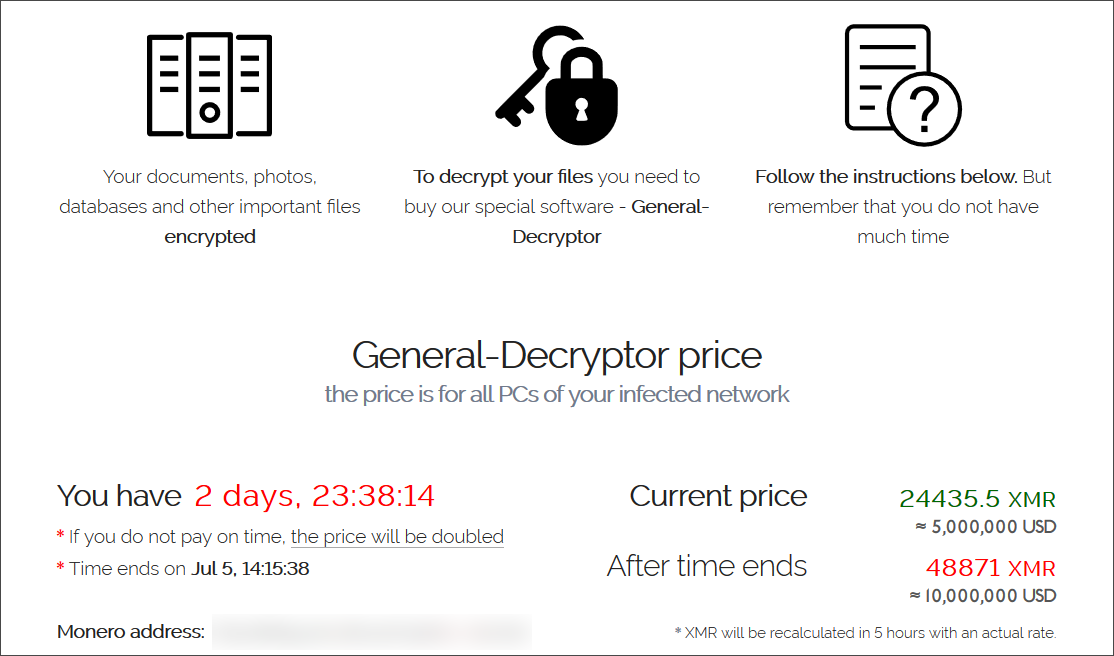
Just in time to ruin the holiday weekend, ransomware attackers have apparently used Kaseya — a software platform designed to help manage IT services remotely — to deliver their payload. Sophos director and ethical hacker Mark Loman tweeted about the attack on Friday, and reported that affected systems will demand $44,999 to be unlocked. A note on Kaseya’s website implores customers to shut off their VSA servers for now “because one of the first things the attacker does is shutoff administrative access to the VSA.”
=========================================================================
Important Notice July 3rd, 2021
July 3, 2021 1:30 PM EDT
Latest Updates will be published at: Important Notice July 3rd, 2021 – Kaseya
Kaseya’s VSA product has unfortunately been the victim of a sophisticated cyberattack. Due to our teams’ fast response, we believe that this has been localized to a very small number of on-premises customers only.
Kaseya is progressing on the security incident along multiple workstreams:
- Since the security of our customers is paramount, we are continuing to strongly recommend that our on-premises customers’ VSA servers remain offline until further notice. We will also keep our SaaS servers offline until further notice.
- We have been advised by our outside experts, that customers who experienced ransomware and receive communication from the attackers should not click on any links -- they may be weaponized.
- We have engaged with the FBI and are working with them on an incident handling process for our worldwide customers impacted by the cyberattack. We will be publishing a list of contacts later today.
- Kaseya executives are directly reaching out to impacted customers to understand their situations and what assistance is possible. If you believe that you have been impacted, please contact support@kaseya.com with the subject “Security Incident Report.”
- We continue to engage with Industry experts to assess the manner and impact of the attack to ensure that our R&D organization has properly identified and mitigated the vulnerability.
- R&D has replicated the attack vector and is working on mitigating it. We will not publish a resolution timeframe until we have thoroughly validated and tested the proposed solution. We appreciate your patience.
- We have engaged a computer forensics firm to identify the indicators of compromise (IOCs) to ensure that we can identify which systems and data were accessed.
- R&D is working on a self-assessment tool for our customers, to enable them to definitively determine whether they were affected. This will be published as part of the patch for on-premises customers.
- At this time, we believe that none of our NOC customers (neither SaaS nor on-premises) were affected by the attack. We’re continuing to investigate this.
- ALL ON-PREMISES VSA SERVERS SHOULD CONTINUE TO REMAIN OFFLINE UNTIL FURTHER INSTRUCTIONS FROM KASEYA ABOUT WHEN IT IS SAFE TO RESTORE OPERATIONS. A PATCH WILL BE REQUIRED TO BE INSTALLED PRIOR TO RESTARTING THE VSA.
- SAAS & HOSTED VSA SERVERS WILL BECOME OPERATIONAL ONCE KASEYA HAS DETERMINED THAT WE CAN SAFELY RESTORE OPERATIONS.
=========================================================================
INSERT: 
Kaseya VSA Supply-Chain Ransomware Attack
Original release date: July 02, 2021 CISA is taking action to understand and address the recent supply-chain ransomware attack against Kaseya VSA and the multiple managed service providers (MSPs) that employ VSA software. CISA encourages organizations to review the
Kaseya advisory and immediately follow their guidance to shutdown VSA servers.
=========================================================================
On Saturday, Kaseya issued another update, saying that it had been advised by its outside experts that “customers who experienced ransomware and receive a communication from the attackers should not click on any links – they may be weaponized.”
Insert >> hot potato:
A ransomware attack has hit hundreds of businesses across the US, in a supply chain attack that targets Kaseya’s VSA system management platform (used for remote monitoring and IT management). While Kaseya claims less than 40 of over 36,000 customers were affected, the targeting of large managed service providers has led to vast numbers of clients further downstream being hit as a result.
Ransomware gang REvil appear to have their payload delivered via a standard automatic software update. It then uses PowerShell to decode and extract its contents while simultaneously suppressing numerous Windows Defender mechanisms such as including real-time monitoring, cloud lookup, and controlled folder access (Microsoft’s own built-in anti-ransomware feature). This payload also includes an older (but legitimate) version of Windows Defender, which is used as a trusted executable in order to launch a DLL with the encryptor.
It’s not yet known if REvil is stealing any data from victims before activating their ransomware and encryption, but the group is known to have done so in past attacks.
The scale of the attack is still unfolding; supply chain attacks like these that compromise weak links further upstream (instead of hitting targets directly) have the potential to wreak havoc on a broad scale if those weak links are widely used — as Kaseya’s VSA is, in this case. Furthermore, its arrival on the weekend of 4th of July seems to have been timed to minimize the availability of staff to deal with the threat and slowing the response to it.
=========================================================================
> According to a report from Bleeping Computer, the attack targeted six large MSPs and has encrypted data for as many as 200 companies.
> At DoublePulsar, Kevin Beaumont has posted more details about how the attack seems to work, with REvil ransomware arriving via a Kaseya update and using the platform’s administrative privileges to infect systems. Once the Managed Service Providers are infected, their systems can attack the clients that they provide remote IT services for (network management, system updates, and backups, among other things).
In a statement, Kaseya told The Verge that “We are investigating a potential attack against the VSA that indicates to have been limited to a small number of our on-premises customers only.” A notice claims that all of its cloud servers are now in “maintenance mode,” a move that the spokesperson said is being taken due to an “abundance of caution.” Later on Friday evening, Kaseya CEO Fred Voccola issued a statement saying they estimated the number of MSPs affected is fewer than 40, and are preparing a patch to mitigate the vulnerability.
“While our early indicators suggested that only a very small number of on-premises customers were affected, we took a conservative approach in shutting down the SaaS servers to ensure we protected our more than 36,000 customers to the best of our ability,” Voccola said in the statement, adding that the company’s SaaS customers were never at risk, and reiterating that “only a very small percentage of our customers were affected.”
> On Saturday, Bloomberg reported that the attack was affecting more than 1,000 businesses in a ripple effect; the attack focused on managed service providers, but these providers offer IT services to other companies that may now be affected as well.
> A grocery chain in Sweden reported it couldn’t open 800 of its stores on Saturday when the attack resulted in its cash registers malfunctioning, Bloomberg reported.
The attack has been linked to the notorious REvil ransomware gang (already linked to attacks on Acer and meat supplier JBS earlier this year), and
> The Record notes that, collecting incidents under more than one name, this may be the third time Kaseya software has been a vector for their exploits.
Kaseya said Saturday it would provide updates on the situation every three to four hours.
Update July 2nd, 10:40PM ET: Added statement from Kaseya CEO.
Update July 3rd 12:04PM ET: Added new information from Kaseya and updates about the spread of the attack