
|

|
|
|
|
|

|

|
|
|
|
|
 "Apple's announcement that it was suing Israeli malware purveyor NSO Group for targeting iPhone users was coupled with another, equally dismaying (I mean, for NSO…) announcement:
"Apple's announcement that it was suing Israeli malware purveyor NSO Group for targeting iPhone users was coupled with another, equally dismaying (I mean, for NSO…) announcement: If NSO doesn't like it, it can suck it. It chose to sell to governments with long histories of targeting critics and violating human rights. Its customers can likewise suck it. They've given themselves an infinite amount of leash and NSO's exploits have let them take full advantage of this. Even a minimal amount of thwarting of nefarious doings is welcome in a world where the powerful go unpunished and unchecked far too often. >
Filed Under: hacking, malware, pegasus, surveillance
Companies: apple, nso group
Spyware sold to authoritarian regimes used to target activists, politicians and journalists, data suggests
Stephanie Kirchgaessner, Paul Lewis, David Pegg,Sam Cutler,Nina Lakhani and Michael Safi
Last modified on Sun 18 Jul 2021 16.39 EDT
". . . Human rights activists, journalists and lawyers across the world have been targeted by authoritarian governments using hacking software sold by the Israeli surveillance company NSO Group, according to an investigation into a massive data leak.
The investigation by the Guardian and 16 other media organisations suggests widespread and continuing abuse of NSO’s hacking spyware, Pegasus, which the company insists is only intended for use against criminals and terrorists.
Pegasus is a malware that infects iPhones and Android devices to enable operators of the tool to extract messages, photos and emails, record calls and secretly activate microphones.
The leak contains a list of more than 50,000 phone numbers that, it is believed, have been identified as those of people of interest by clients of NSO since 2016.
Forbidden Stories, a Paris-based nonprofit media organisation, and Amnesty International initially had access to the leaked list and shared access with media partners as part of the Pegasus project, a reporting consortium. . .Through its lawyers, NSO said the consortium had made “incorrect assumptions” about which clients use the company’s technology. It said the 50,000 number was “exaggerated” and the list could not be a list of numbers “targeted by governments using Pegasus”. 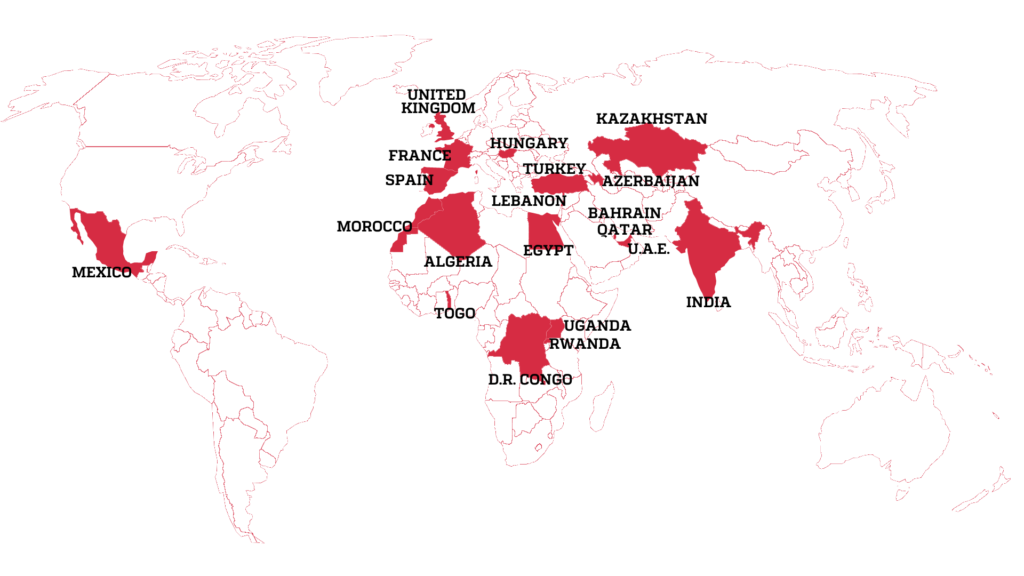
The lawyers said NSO had reason to believe the list accessed by the consortium “is not a list of numbers targeted by governments using Pegasus, but instead, may be part of a larger list of numbers that might have been used by NSO Group customers for other purposes”. After further questions, the lawyers said the consortium was basing its findings “on misleading interpretation of leaked data from accessible and overt basic information, such as HLR Lookup services, which have no bearing on the list of the customers' targets of Pegasus or any other NSO products ...
> Claudio Guarnieri, who runs Amnesty International’s Security Lab, said once a phone was infected with Pegasus, a client of NSO could in effect take control of a phone, enabling them to extract a person’s messages, calls, photos and emails, secretly activate cameras or microphones, and read the contents of encrypted messaging apps such as WhatsApp, Telegram and Signal. . . By accessing GPS and hardware sensors in the phone, he added, NSO’s clients could also secure a log of a person’s past movements and track their location in real time with pinpoint accuracy, for example by establishing the direction and speed a car was travelling in.
The latest advances in NSO’s technology enable it to penetrate phones with “zero-click” attacks, meaning a user does not even need to click on a malicious link for their phone to be infected.
_____________________________________________________________________________
"The ‘Digital Violence: How the NSO Group Enables State Terror’ platform that details the operations of Israeli startup NSO Group (Courtesy)
An interactive online platform created by research agency Forensic Architecture, and supported by Amnesty International and the internet watchdog group Citizen Lab, has mapped the global spread of the spyware Pegasus, made by Israeli cybersecurity firm NSO Group.
Titled “Digital Violence: How the NSO Group Enables State Terror,” the website shows, for what is said to be the first time, geographic areas in which Pegasus spyware has been deployed worldwide, and interviews lawyers, activists and other civil society figures about their experiences.
Forensic Architecture, based in the University of London, investigates human rights violations by states, police forces and corporations.
“The company’s Pegasus spyware has been used in some of the most insidious digital attacks on human rights defenders,” Amnesty International said on its website. “When Pegasus is surreptitiously installed on a person’s phone, an attacker has complete access to a phone’s messages, emails, media, microphone, camera, calls and contacts.”
“The investigation reveals the extent to which the digital domain we inhabit has become the new frontier of human rights violations, a site of state surveillance and intimidation that enables physical violations in real space,” said Forensic Architecture researcher Shourideh Molavi in the Amnesty statement.
Guarnieri has identified evidence NSO has been exploiting vulnerabilities associated with iMessage, which comes installed on all iPhones, and has been able to penetrate even the most up-to-date iPhone running the latest version of iOS. His team’s forensic analysis discovered successful and attempted Pegasus infections of phones as recently as this month. . ."
_____________________________________________________________________________

Magazine
The president went from skeptic to evangelist on global democracy. But over the past year, his ambitions have collided repeatedly—and uncomfortably—with reality.
[...] "The language of “American exceptionalism” now has a nostalgic ring, because the United States is arguably no longer either the world’s most powerful country or its most effective democracy. Indeed, one stated premise of the summit, too plainly true to be dismissed as mere rhetoric, is that America has as much to gain from the experience of other countries as they do from that of the United States. . ."

[ The Biden team hopes to encourage states to stand up to Russia and China on issues like electoral interference and targeting dissidents. | Ding Lin/Xinhua via AP ]
". . .Erosion inside the world’s democracies requires a very different, and yet more urgent, endeavor from the one first articulated by Woodrow Wilson when he promised a new order after World War I that would make the world "safe for democracy.” That crusade now feels like a luxury. Biden, by contrast, hopes to protect or preserve democracy where it already exists. He has frequently cast his ambitious domestic agenda as proof that democracies can “deliver” prosperity and security in a way that autocracies cannot. This is no easy argument to make at a time when China has achieved sustained economic growth at a rate unprecedented in modern history. It is by no means obvious that democracies work better than non-democracies.
[...]
Nevertheless, what looked a year ago like a democratic jamboree now resembles a C-SPAN marathon. Given the high hopes that the prospect of a democracy summit once kindled, the whole affair may be an exercise in anti-climax.
In the course of my conversation with Blinken, I asked what he thought the United States could get out of the summit. "There is a call-to-action aspect of this that also is part of our summoning of our better angels," he said, "which the President strongly believes continues to resonate powerfully with most Americans. Things have gotten lost along the way. This is a moment to try to refocus our fellow citizens on what makes us exceptional. It does speak to something that continues to unite us, and that people aspire to, even despite the frustrations."
I wonder if this is the language of noble aspiration or of nostalgic yearning. . ."
In a concerning development, the notorious Emotet malware now installs Cobalt Strike beacons directly, giving immediate network access to threat actors and making ransomware attacks imminent.
Emotet is a malware infection that spreads through spam emails containing malicious Word or Excel documents. These documents utilize macros to download and install the Emotet Trojan on a victim's computer, which is then used to steal email and deploy further malware on the device.
Historically, Emotet would install the TrickBot or Qbot trojans on infected devices. These Trojans would eventually deploy Cobalt Strike on an infected device or perform other malicious behavior.
Cobalt Strike is a legitimate penetration testing toolkit that allows attackers to deploy "beacons" on compromised devices to perform remote network surveillance or execute further commands.
However, Cobalt Strike is very popular among threat actors who use cracked versions as part of their network breaches and is commonly used in ransomware attacks.
Today, Emotet research group Cryptolaemus warned that Emotet is now skipping their primary malware payload of TrickBot or Qbot and directly installing Cobalt Strike beacons on infected devices.
WARNING We have confirmed that #Emotet is dropping CS Beacons on E5 Bots and we have observed the following as of 10:00EST/15:00UTC. The following beacon was dropped: https://t.co/imJDQTGqxV Note the traffic to lartmana[.]com. This is an active CS Teams Server. 1/x
— Cryptolaemus (@Cryptolaemus1) December 7, 2021
A Flash Alert shared with BleepingComputer by email security firm Cofense explained that a limited number of Emotet infections installed Cobalt Strike, attempted to contact a remote domain, and then was uninstalled. . ." READ MORE

December 7, 2021 10:15 AM
Due to the pandemic and the rising trend of working from home, organizations have begun to rely heavily on cloud-based services. This necessity also increased cloud providers utilizing Eltima's SDK that allow employees to mount local USB mass storage devices for use on their cloud-based virtual desktops.
However, as cloud desktop providers, including Amazon Workspaces, rely on tools like Eltima, SentinelOne warned that millions of users worldwide have become exposed to the discovered vulnerabilities.
The implications of exploiting the flaws are significant as they could allow remote threat actors to gain elevated access on a cloud desktop to run code in kernel mode.
"These vulnerabilities allow attackers to escalate privileges enabling them to disable security products, overwrite system components, corrupt the operating system, or perform malicious operations unimpeded," explained a new report by Sentinel Labs.
This elevated access could allow malware to steal credentials that threat actors can use to breach an organization's internal network.
In total, there are 27 vulnerabilities discovered by SentinelOne, with the CVE IDs listed below:
CVE-2021-42972, CVE-2021-42973, CVE-2021-42976, CVE-2021-42977, CVE-2021-42979, CVE-2021-42980, CVE-2021-42983, CVE-2021-42986, CVE-2021-42987, CVE-2021-42988, CVE-2021-42990, CVE-2021-42993, CVE-2021-42994, CVE-2021-42996, CVE-2021-43000, CVE-2021-43002, CVE-2021-43003, CVE-2021-43006, CVE-2021-43637, CVE-2021-43638, CVE-2021-42681, CVE-2021-42682, CVE-2021-42683, CVE-2021-42685, CVE-2021-42686, CVE-2021-42687, CVE-2021-42688These vulnerabilities have been responsibly disclosed to Eltima, who has already released fixes for affected versions. However, it is now up to cloud services to upgrade their software to utilize the updated Eltima SDK.
According to SentinelOne, the affected software and cloud platforms are:
It is important to note that Sentinel Labs hasn’t looked into all possible products that could incorporate the vulnerable Eltima SDK, so there could be more products affected by the set of flaws.
Also, some services are vulnerable on the client-side, others on the server-side, and a few on both, depending on code-sharing policies
In a concerning development, the notorious Emotet malware now installs Cobalt Strike beacons directly, giving immediate network access to threat actors and making ransomware attacks imminent.
 0
0Open-source analytics and interactive visualization solution Grafana received an emergency update today to fix a high-severity, zero-day vulnerability that enabled remote access to local files.
 1
1Amazon AWS in the US-EAST-1 Region is suffering an outage that affected numerous online services, including Ring, Netflix, and Amazon Prime Video, and Roku.
 0
0A 31-year old Canadian national has been charged in connection to ransomware attacks against organizations in the United States and Canada, a federal indictment unsealed today shows.
 0
0US universities are being targeted in multiple phishing attacks designed to impersonate college login portals to steal valuable Office 365 credentials.
 0
0The Essential Windows 11 Course provides an easy way to learn your way around, with 5½ hours of video tutorials. It's normally priced at $75, but you can get it today for only $19.99,
 0
0Microsoft has started rolling out the new and completely redesigned Notepad for Windows 11 to all Windows Insiders in the Dev Channel.
 0
0Cerber ransomware is back, as a new ransomware family adopts the old name and targets Atlassian Confluence and GitLab servers using remote code execution vulnerabilities.
 0
0Google announced today that it has taken action to disrupt the Glupteba botnet that now controls more than 1 million Windows PCs around the world, growing by thousands of new infected devices each day.
 0
0Researchers have discovered 27 vulnerabilities in Eltima SDK, a library used by numerous cloud providers to remotely mount a local USB device.
 0
0German security software company G DATA has released a vaccine that will block STOP Ransomware from encrypting victims' files after infection.
 3
3QNAP warned customers today of ongoing attacks targeting their NAS (network-attached storage) devices with cryptomining malware, urging them to take measures to protect them immediately.
 0
0Scammers monitor every tweet containing requests for support on MetaMask, TrustWallet, and other popular crypto wallets, and respond to them with scam links in just seconds.
 1
1Nordic Choice Hotels has now confirmed a cyber attack on its systems from the Conti ransomware group. Although there is no indication of card or payment information being affected, information pertaining to guest bookings was potentially leaked.